
The average web based command and control kit for a botnet consisting of single user, single campaign functions only, has just lost its charm, with a recent discovery of a proprietary botnet kit whose features clearly indicate that the kit's coder know exactly which niches to fill - presumably based on his personal experience or market research into competing products.
What are some its key differentiation factors?
Multitasking at its best, for instance, the kits provides the botnet master with the opportunity to manage numerous different task such as several malware campaigns and DDoS attacks simultaneously, where each of these gets a separate metrics page.
 Automation
Automation of malicious tasks, by setting up tasks, and issuing notices on the status of the task, when it was run and when it was ended. Just consider the possibilities for a scheduling malware and DDoS attacks for different quarters.
Segmentation in every aspect of the tasks, for instance, a DDoS attacks against a particular site can be scheduled to launched on a specific date from infected hosts based in chosen countries only.
 Customized DDoS
Customized DDoS in the sense of empowering the botnet master with point'n'click ability to dedicate a precise number of the bots to participate, which countries they should be based in, and for how long the attack should remain active.
Quality and assurance in DDoS attacks based on the measurement of the bot's bandwidth against a particular country, in this case the object of the attack, so theoretically bots from neighboring countries would DDoS the country in question far more efficiently.
 Historical malware campaign performance
Historical malware campaign performance, is perhaps the most quality assurance feature in the entire kit, presumably created in order to allow the person behind it to measure which were the most effective malware and DDoS campaigns that he executed in the past. From an OSINT perspective, sacrificing his operational security by maintaing detailed logs from previous attacks is a gold mine directly establishing his relationships with previous malware campaigns.
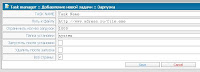 Bot Description
Bot Description:
1. Completely invisible Bot work in the system.
2. Not loads system.
3. Invisible in the process.
4. Workaround all firewall.
5. Bot implemented as a driver.
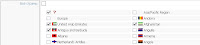 Functions Bot
Functions Bot (constantly updated):
1. Downloading a file (many options).
2. HTTP DDoS (many options, including http authentication).
 The web interface
The web interface -- Convenient manager tasks.
-- Every task can be stopped, put on pause, etc. ...
-- Interest and visual scale of the task.
-- A task manager for DDoS and Loader

--
For DDoS tasks Bots involved in DDoS 'f.
Condition of the victim (works, fell).

2.
Bots manager -- Displays a list of bots (postranichno).
-- Obratseniya date of the first and last.
-- ID Bot.
-- Country Bot.
-- Type Bot.
-- The status Bot (online / offline).
-- Bot bandwidth to different parts of the world (europe, asia).
-- The possibility of removing bots
-- When you click on ID Bot loadable still a wealth of information about it

3.
Statistics botneta -- Statistics both common and build Bot.
-- Information on the growth and decline botneta dates (and build).
-- Bots online
-- All bots

-- Dead bots.
4.
Statistics botneta country-- All countries to work on
-- New work by country
-- Online work from country to country
-- Dead bots by country
5. Detailed history botneta
6. Convenient user-friendly interface adding teams
7. Admin minimal server loads
-- Use php5/mysql
 Upcoming features :
Upcoming features : 1. Form grabber (price increase substantially), for old customers will be charged as an upgrade
2. Public key cryptography
3. Clustering campaigns and DDoS attacks
Despite it's proprietary nature, it's quality and innovative features will sooner or later leak out for everyone to take advantage of, a rather common lifecycle for the majority of proprietary malware kits in general.
Related posts:
 "Are you a Human?" - once asked the CAPTCHA, and the question got answered by, well, a human, thousands of them to be precise. Speculations around one of the main weaknesses of CAPTCHA based authentication in the face of human CAPTCHA solvers, seems to have evolved into a booming economy in India during the past 12 months, with thousands of people involved.
"Are you a Human?" - once asked the CAPTCHA, and the question got answered by, well, a human, thousands of them to be precise. Speculations around one of the main weaknesses of CAPTCHA based authentication in the face of human CAPTCHA solvers, seems to have evolved into a booming economy in India during the past 12 months, with thousands of people involved.













































0 Comments: