Dear blog readers, dare to take a moment of your precious time to check a venerable and recently proposed cyber security project investment including the opportunity to enter a Bold New World of Hacking and Information Security? Has the time come to set them straight? Keep reading.
Check out this Onion - http://lkzihepprlhxtvbutjedoazbsqd4avmifhpjms3zuq7itceiu4qajwad.onion/ and donate today!
Stay tuned!
Independent Contractor. Bitcoin: 15Zvie1j8CjSR52doVSZSjctCDSx3pDjKZ Email: dancho.danchev@hush.com OMEMO: ddanchev@conversations.im | OTR: danchodanchev@xmpp.jp | TOX ID: 2E6FCA35A18AA76B2CCE33B55404A796F077CADA56F38922A1988AA381AE617A15D3D3E3E6F1
Monday, August 19, 2019
g0t Bitcoin?
Tags:
Bitcoin,
Cyber Security Investment,
Dark Web,
Information Security,
Security,
Security Investment,
Virtual Reality,
Virtual Reality Social Network,
Virtual World
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, August 02, 2019
Assessing the Recently Leaked FSB Contractor Data - A Peek Inside Russia's Understanding of Social Network Analysis and Tailored Access Operations
I've recently managed to obtain a copy of the recently leaked FSB contractor data courtesy of 0v1ru$ and "Digital Revolution" and I've decided to take a closer look including an in-depth overview and discussion of the leaked data in the context of today's modern-driven AI-powered automated OSINT technologies in the broader context of the U.S Intelligence Community in particular the utilization of rogue TOR exit nodes for the purpose of intercepting and harvesting TOR exit node data within the Russian Federation including social-network analysis data-mining and possible "lawful surveillance" and "lawful interception" including possible data collection type of Tailored Access Operation campaigns launched by "0day Technologies" and "SyTech".
Sample Company Logo:
Sample personal photos of the individuals behind "0day Technologies" and "SyTech":
Sample Twitter account involved in the campaign:
hxxp://twitter.com/d1g1r3v
hxxp://twitter.com/0v1ruS
Sample URL known to have participated in the campaign:
hxxp://d1g1r3v.net
Related URL of the currently leaked data:
https://mega.nz/#F!3c0lTaLI!jVUS_O7Q0opCHUPYgK1E_w
Sample Company Logo:
Sample Company Logo:
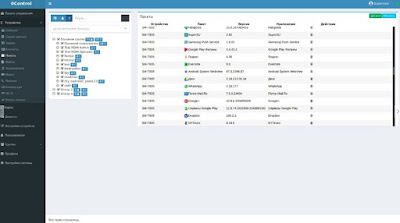
Sample Screenshots of the User-Interface behind the "Lawful Surveillance" and "Lawful Interception":
Sample Screenshots of the Rogue and Bogus Tor-Exit-Node Research Project:
Sample URLs involved in the campaign:
hxxp://0day.ru
hxxp://sytech.ru
Sample Telegram account involved in the campaign:
hxxp://t.me/D1G1R3V_DigitalRevolution
Sample Vkontakt account involved in the campaign:
hxxp://vk.com/d1g1r3v
Sample Twitter account involved in the campaign:
hxxp://twitter.com/d1g1r3v
hxxp://twitter.com/0v1ruS
Sample URL known to have participated in the campaign:
hxxp://d1g1r3v.net
Related URL of the currently leaked data:
https://mega.nz/#F!3c0lTaLI!jVUS_O7Q0opCHUPYgK1E_w
Tags:
CIA,
Cyber Attack,
Cyber Espionage,
Cyber Warfare,
Cybercrime,
Eavesdropping,
HUMINT,
Information Security,
Information Warfare,
Intelligence,
Intelligence Agency,
NSA,
Security,
Surveillance
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Subscribe to:
Posts (Atom)