Ubiquitous social engineering schemes, never fade away. ZeuS crimeware campaigners are currently using a 123greetings.com ecard-themed campaign, in an attempt to entice users to "enjoy their ecard".
Subject: "You have received an Greeting eCard"
Message: "Good day. You have received an eCard
To pick up your eCard, choose from any of the following options: Click on the following link (or copy & paste it into your web browser): matt-levine.com /ecard.exe; secondary URL offered: forestarabians.nl /ecard.exe Your card will be aviailable for pick-up beginning for the next 30 days. Please be sure to view your eCard before the days are up! We hope you enjoy you eCard. Thank You!"
Detection rate:
- ecard.exe - Cryp_Zbot-12; Trojan/Win32.Vundo - Result: 9/42 (21.43%)
File size: 147968 bytes
MD5...: e6f3aa226bf9733b7e8c07cab339f4dc
SHA1..: e983767931900a13b88a615d6c1d3f6ff8fb6b60
Upon execution, the sample phones back to:
zephehooqu.ru /bin/koethood.bin - 77.78.240.115, AS42560 - Email: skit@5mx.ru
jocudaidie.ru /9xq/_gate.php - 118.169.173.218, AS3462 - Email: skit@5mx.ru - FAST-FLUXED
Multiple MD5s are also currently active at zephehooqu.ru.
Detection rates:
aimeenei.exe - Win32/Zbot.CJI - Result: 30/42 (71.43%)
File size: 149504 bytes
MD5...: 096b7e8c4f611f0eb69cfb776f3a0e7e
SHA1..: 909d7c2740f84599d5e30ffed7261e19ad4a962a
cahdoigu.exe - Mal/Zbot-U - Result: 27/42 (64.29%)
File size: 147968 bytes
MD5...: 11f9f96c17584a672c2a563744130a46
SHA1..: f31c40c5c766c7628023105be6f004e5322b17b6
koethood.exe - Troj/Zbot-SW - Result: 30/42 (71.43%)
File size: 147968 bytes
MD5...: da1979227141844be69577f7f31a7309
SHA1..: 5ada2c390e63ca051c9582fe723384ce52a45912
loobuhai.exe - BKDR_QAKBOT.SMB - Result: 33/42 (78.58%)
File size: 147968 bytes
MD5...: df4e19af8c356b3ff810bc52f6081ccc
SHA1..: d4a1d2f147ae0d24a3eaac66e8d2f9de50cf7a0c
oovaenai.exe - Packed.Win32.Katusha.j - Result: 32/42 (76.2%)
File size: 147456 bytes
MD5...: f0fd5579f06d5b581b5641546ae91d52
SHA1..: c81fa66c546020f3c1c34a0d1aa191b2d9578f07
quohthei.exe - Win32/Spy.Zbot.YW - Result: 33/42 (78.58%)
File size: 147968 bytes
MD5...: ffc0d66024f690e875638f4c33ba86f1
SHA1..: c958f3426a3e6fedd76b86a5aef16c90915ac539
sofeigoo.exe - Win32/Spy.Zbot.YW - Result: 31/42 (73.81%)
File size: 148992 bytes
MD5...: 45e98426fafd221ffb7d55ce8a1ae531
SHA1..: 8235b3a80ba6611779dfd4db40a48627af7374eb
teemaeko.exe - PWS:Win32/Zbot.gen!Y - Result: 32/42 (76.2%)
File size: 148992 bytes
MD5...: 9758f04d2f1bd664f37c4285a013372a
SHA1..: 4273dc48f9aeaf69cb7047c4a882af74479fb635
thaigogo.exe - Win32/Spy.Zbot.YW - Result: 34/42 (80.96%)
File size: 147968 bytes
MD5...: b667d75f5bb9f23a8ae249f7de4000a5
SHA1..: 7b57783dcf2aeaafbab3407bb608469851d342bb
ziejaing.exe - Trojan.Zbot.610 - Result: 30/42 (71.43%)
File size: 147456 bytes
MD5...: 7592e957de01e53956517097c0e9ccd8
SHA1..: e7c04d2c8c5d4a51e2615a2ee015d87d28655320
Related .ru cybercrime-friendly domains, sharing fast-flux infrastructure with this campaign's C&C:
adaichaepo.ru - Email: subtle@maillife.ru
aroolohnet.ru - Email: brawn@bigmailbox.ru
dahzunaeye.ru - Email: celia@freenetbox.ru
esvr3.ru - Email: bender@freenetbox.ru
hazelpay.ru - Email: owed@bigmailbox.ru
iesahnaepi.ru - Email: heel@bigmailbox.ru
iveeteepew.ru - Email: atomic@freenetbox.ru
jocudaidie.ru - Email: skit@5mx.ru
ohphahfech.ru - Email: warts@maillife.ru
railuhocal.ru - Email: celia@freenetbox.ru
sdlls.ru - Email: vc@bigmailbox.ru
Name servers of notice within the fast-flux infrastructure:
ns1.tophitnews.net - 74.122.197.22 - Email: worldchenell@ymail.com
ns2.tophitnews.net - 173.19.142.57
ns1.usercool.net - 74.122.197.22
ns2.usercool.net - 76.22.74.15
ns1.welcominternet.net - 74.54.82.223 - Email: admin@rangermadeira.com
ns2.welcominternet.net - 74.54.82.223
ns1.gamezoneland.com - 188.40.204.158 - Email: xtrail.corp@gmail.com
ns2.gamezoneland.com - 174.224.63.18
ns1.tropic-nolk.com - 188.40.204.158 - Email: greysy@gmx.com
ns2.tropic-nolk.com - 171.103.51.158
ns1.interaktivitysearch.net - 202.60.74.39 - Email: ssupercats@yahoo.com
ns2.interaktivitysearch.net - 202.60.74.39
ns1.openworldwhite.net - 202.60.74.39 - Email: xtrail.corp@gmail.com
ns2.openworldwhite.net - 43.125.79.23
ns1.helphotbest.net - Email: worldchenell@ymail.com
It gets even more interesting.
greysy@gmx.com has already been profiled in an Avalanche botnet campaign using TROYAK-AS's services back then (The Avalanche Botnet and the TROYAK-AS Connection), followed by another assessment "TorrentReactor.net Serving Crimeware, Client-Side Exploits Through a Malicious Ad" where the same email was also used to register a name server part of the fast-flux infrastructure of the ZeuS crimeware's C&Cs.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
Independent Contractor. Bitcoin: 15Zvie1j8CjSR52doVSZSjctCDSx3pDjKZ Email: dancho.danchev@hush.com OMEMO: ddanchev@conversations.im | OTR: danchodanchev@xmpp.jp | TOX ID: 2E6FCA35A18AA76B2CCE33B55404A796F077CADA56F38922A1988AA381AE617A15D3D3E3E6F1
Tuesday, July 20, 2010
ZeuS Crimeware Serving 123Greetings Ecard Themed Campaign in the Wild
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Monday, July 19, 2010
Dissecting the Xerox WorkCentre Pro Scanned Document Themed Campaign
Over the weekend, a "Scan from a Xerox WorkCentre Pro" themed malware campaign relying on zip archives, was actively spamvertised by cybecriminals seeking to infect gullible end/corporate users.
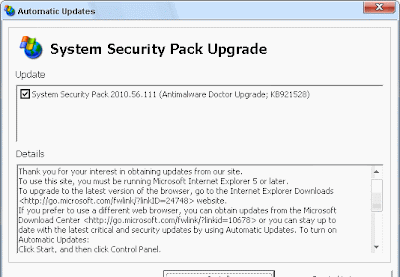
What's particularly interesting about this campaign, is the cocktail of malware dropped on infected hosts, including Asprox sample (Money Mule Recruiters use ASProx's Fast Fluxing Services), and two separate samples of Antimalware Doctor.
- Sample subject: Scan from a Xerox WorkCentre Pro $9721130
- Sample message: "Please open the attached document. It was scanned and sent to you using a Xerox WorkCentre Pro.
Sent by: Guest
Number of Images: 1
Attachment File Type: ZIP [DOC]
WorkCentre Pro Location: machine location not set Device Name: XRX2090AA7ACDB45466972. For more information on Xerox products and solutions, please visit http://www.xerox.com"
- Detection rates:
- Xerox_doc1.exe - Trojan.Win32.Jorik.Oficla.bb - Result: 34/42 (80.96%)
File size: 30926 bytes
MD5...: 1d378a6bc94d5b5a702026d31c21e242
SHA1..: 545e83f547d05664cd6792e254b87539fba24eb9
- Xerox_doc2.exe - Trojan.Win32.Jorik.Oficla.ba - Result: 34/42 (80.96%)
File size: 43520 bytes
MD5...: 829c86d4962f186109534b669ade47d7
SHA1..: 5d3d02d0f6ce87cd96a34b73dc395460d623616e
The samples then phone back to the Oficla/Sasfis C&Cs at hulejsoops.ru/images/bb.php?v=200&id=554905388&b=avpsales&tm=3 - 91.216.215.66, AS51274 - Email: mxx3@yandex.ru which periodically rotates three different executables using the following URLs:
0815.ch /pic/view.exe
curseri.ch /pictures/securedupdaterfix717.exe
regionalprodukte-beo.ch /about/cgi.exe
Backup URLS:
leeitpobbod.ru/image/bb.php - 59.53.91.195, AS4134 - Email: mxx3@yandex.ru - dead response
loloohuildifsd.ru/image/bb.php - 68.168.222.158 - Email: mxx3@yandex.ru - dead response
nemohuildifsd.ru/image/bb.php - 59.53.91.195 (nemohuildiin.ru, russianmomds.ru), AS4134 - Email: mxx3@yandex.ru - dead response
Let's take a peek at the samples found within the C&C.
view.exe - Trojan.Win32.Jorik.Aspxor.e - Result: 11/42 (26.2%)
File size: 79360 bytes
MD5...: 5d296fe1ef7bf67f36fe9adb209398ee
SHA1..: 41b45bcd241cd97b72d7866d13c4a0eb6bf6a0ee
Upon execution, the sample phones back to well known Asprox C&Cs:
cl63amgstart.ru: 80/board.php - 91.213.217.4, AS42473 - Email: ssa1@yandex.ru
hypervmsys.ru: 80/board.php - 89.149.223.232 (hostagents.ru), AS28753 - Email: vadim.rinatovich@yandex.ru
Previously, all of the following ASPRox domains used exclusively for massive SQL injections, used to respond to 91.213.217.4:
webservicesbba.ru - Email: anrnews@mail.ru
webservicelupa.ru - Email: anrnews@mail.ru
webserivcekota.ru - Email: anrnews@mail.ru
webservicesrob.ru - Email: anrnews@mail.ru
webserivcezub.ru - Email: anrnews@mail.ru
webserviceforward.ru - Email: anrnews@mail.ru
webserivcessh.ru - Email: anrnews@mail.ru
webservicesmulti.ru - Email: anrnews@mail.ru
webservicezok.ru - Email: anrnews@mail.ru
webservicebal.ru - Email: anrnews@mail.ru
webservicefull.ru - Email: anrnews@mail.ru
webservicessl.ru - Email: anrnews@mail.ru
webserviceaan.ru - Email: anrnews@mail.ru
webservicedevlop.ru - Email: anrnews@mail.ru
webserviceftp.ru - Email: anrnews@mail.ru
hypervmsys.ru - Email: anrnews@mail.ru
webserviceget.ru - Email: anrnews@mail.ru
webserviceskot.ru - Email: anrnews@mail.ru
cl63amgstart.ru - Email: ssa1@yandex.ru
ml63amgstart.ru - Email: ssa21@yandex.ru
webservicesttt.ru - Email: anrnews@mail.ru
webservicenow.ru - Email: anrnews@mail.ru
webservicekuz.ru - Email: anrnews@mail.ru
Currently, the gang's migrating this infrastructure to 109.196.134.58, AS39150, VLTELECOM-AS VLineTelecom LLC Moscow, Russia.
All of these domains+subdomains sharing the same js.js directory structure, which upon visiting loads URLs such as (accesspad.ru :8080/index.php?pid=6) with the rest of the domains sharing the same infrastructure as the ones profiled in "Spamvertised Amazon "Verify Your Email", "Your Amazon Order" Malicious Emails" post:
access.webservicebal.ru
admin.webserivcekota.ru
api.webserivcessh.ru
app.webserviceforward.ru
app.webservicesrob.ru
base.webserviceftp.ru
batch.webserviceaan.ru
batch.webservicebal.ru
bios.webservicesbba.ru
block.webserviceaan.ru
block.webservicesrob.ru
cache.webservicesbba.ru
cache.webservicesmulti.ru
chk.webservicezok.ru
cmdid.webserivcezub.ru
code.webservicesbba.ru
com.webserivcekota.ru
com.webservicedevlop.ru
ddk.webservicesrob.ru
default.webservicezok.ru
diag.webserviceftp.ru
direct.webserviceftp.ru
dll.webservicelupa.ru
drv.webservicebal.ru
drv.webservicesrob.ru
encode.webservicefull.ru
err.webserivcessh.ru
export.webservicedevlop.ru
ext.webserviceaan.ru
ext.webservicesbba.ru
file.webserivcekota.ru
file.webserivcessh.ru
filter.webservicedevlop.ru
font.webservicelupa.ru
gdi.webserviceftp.ru
get.webservicesbba.ru
go.webserivcekota.ru
go.webservicefull.ru
guid.webserivcezub.ru
hostid.webservicesbba.ru
hostid.webservicesmulti.ru
http.webserviceforward.ru
icmp.webservicesbba.ru
id.webserivcezub.ru
inf.webserviceaan.ru
info.webservicedevlop.ru
ini.webservicesrob.ru
ioctl.webservicedevlop.ru
kernel.webservicezok.ru
lan.webservicefull.ru
lan.webservicesbba.ru
lib.webservicebal.ru
lib.webserviceftp.ru
libid.webservicelupa.ru
load.webservicebal.ru
locate.webservicelupa.ru
log.webservicelupa.ru
log.webservicezok.ru
log-in.webservicessl.ru
manage.webservicesbba.ru
map.webserivcezub.ru
map.webservicedevlop.ru
media.webserviceftp.ru
mode.webservicelupa.ru
net.webservicebal.ru
netapi.webserviceaan.ru
netmsg.webserivcezub.ru
ns1.webservicelupa.ru
ns2.webservicelupa.ru
ntdll.webservicessl.ru
ntio.webservicelupa.ru
ntio.webservicezok.ru
obj.webservicesbba.ru
object.webserivcessh.ru
object.webservicesmulti.ru
oem.webservicebal.ru
offset.webservicefull.ru
ole.webservicesbba.ru
org.webservicesrob.ru
page.webserviceaan.ru
parse.webservicebal.ru
peer.webserviceaan.ru
pic.webservicesbba.ru
pool.webservicelupa.ru
port.webservicebal.ru
port.webservicesbba.ru
port.webservicessl.ru
proc.webserviceaan.ru
proc.webservicessl.ru
rdir.webserviceftp.ru
redir.webservicedevlop.ru
refer.webserivcezub.ru
reg.webserviceaan.ru
remote.webservicessl.ru
run.webserivcekota.ru
script.webserivcezub.ru
sdk.webserivcezub.ru
search.webserviceaan.ru
search.webservicedevlop.ru
setup.webserivcezub.ru
setup.webservicezok.ru
snmp.webserviceforward.ru
snmp.webservicesrob.ru
sslcom.webserivcessh.ru
sslcom.webservicesrob.ru
sslid.webserivcekota.ru
sslnet.webservicedevlop.ru
svc.webservicedevlop.ru
tag.webservicebal.ru
tag.webservicessl.ru
tid.webserviceftp.ru
time.webservicelupa.ru
udp.webserviceftp.ru
udp.webservicezok.ru
update.webserviceftp.ru
update.webservicefull.ru
url.webservicesbba.ru
url.webservicezok.ru
vba.webservicesrob.ru
vbs.webservicelupa.ru
ver.webserivcekota.ru
webserivcekota.ru
webserivcessh.ru
webserivcezub.ru
webserviceaan.ru
webservicebal.ru
webservicedevlop.ru
webserviceforward.ru
webserviceftp.ru
webservicefull.ru
webserviceget.ru
webservicelupa.ru
webservicesmulti.ru
webservicesrob.ru
webservicessl.ru
webservicezok.ru
win.webservicezok.ru
xml.webservicefull.ru
Getting back to the samples rotated by the original campaign binary, and their detection rates, network interactions.
- Detection rates:
- securedupdaterfix717.exe - Trojan.Win32.FakeYak - Result: 22/42 (52.39%)
File size: 36864 bytes
MD5...: cd16d4c998537248e6d4d0a3d51ca6de
SHA1..: 7e36ef0ce85fac18ecffd5a82566352ce0322589
Phones back to:
s.ldwn.in/inst.php?fff=7071710000&saf=ru - 91.188.60.236 (updget.in; wordmeat.in), AS6851 - Email: feliciachappell@ymail.com
bootfree.in/ MainModule717release10000.exe - 194.8.250.207 (flowload.in; lessown.in; sstats.in), AS43134 - Email: feliciachappell@ymail.com
s.wordmeat.in/install.php?coid= - 91.188.60.236, AS6851 - Email: feliciachappell@ymail.com
- Detection rate for MainModule717release10000.exe
- MainModule717release10000.exe - Trojan:Win32/FakeYak - Result: 26/42 (61.90%)
File size: 1043968 bytes
MD5...: 3c30c62e9981bd86c5897447cb358235
SHA1...: 36bfc285a61bcb67f2867dd303ac3cefa0e490a0
Phones back to:
wordmeat.in - 91.188.60.236 - Email: feliciachappell@ymail.com
vismake.in - 91.188.60.236 - Email: keelingelizabeth@ymail.com
- Detection rate for the 3rd binary rotated in the original C&C:
- cgi.exe - Trojan.Inject.8960 - Result: 6/42 (14.29%)File size: 62976 bytes
MD5...: 45c062490e0fc262c181efc323cb83ba
SHA1..: bff90630f2064d7bcc82b7389c2b8525ff960870
Phones back to:
musiceng.ru /music/forum/index1.php - 91.212.127.40, AS49087 - Email: ol.feodosoff@yandex.ru
The whole campaign, is a great example of what cybercrime underground multitasking is all about. Moreover, it illustrates the interactions between the usual suspects, with the not so surprising appearance of the already profiled AS6851, BKCNET, Sagade Ltd.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, July 16, 2010
Spamvertised Amazon "Verify Your Email", "Your Amazon Order" Malicious Emails
And they're back (Gumblar or RUmblar due to the extensive use of .ru domains) for a decent start of the weekend - switching social engineering themes one more time, this time impersonating Amazon.com
- NOTE: A summary of the malicious payload served will be posted at a later stage. Meanwhile, in order to facilitate quicker response, a complete list of the domains participating will be featured/disseminated across the appropriate parties.
- Sample message: "Dear email, You recently changed your e-mail address at Amazon.com. Since you are a subscriber of Amazon.com Delivers E-mail Subscriptions, you will need to verify your new e-mail address. Please verify that the e-mail address email belongs to you. You can click on the link below to complete the verification process. Alternatively, you can type or paste the following link into your Web browser: http://www.amazon.com"
Client-side exploitation is taking place through, for instance, crystalrobe.ru: 8080/index.php?pid=14 and hillchart.com: 8080/index.php?pid=14. As seen in previous campaigns, this one is also sharing an identical directory structure, such as:
malicious-domain.com :8080/index.php?pid=2
malicious-domain.com :8080/Notes1.pdf (Notes1-to-Notes10.pdf)
malicious-domain.com :8080/NewGames.jar
malicious-domain.com :8080/Games.jar
malicious-domain.com :8080/Applet1.html (Applet1-to-Applet10.html)
malicious-domain.com :8080/welcome.php?id=6&pid=1&hello=503
crystalrobe.ru :8080/index.php?pid=14
crystalrobe.ru :8080/jquery.jxx?v=5.3.4
crystalrobe.ru :8080/new/controller.php
crystalrobe.ru :8080/js.php
crystalrobe.ru :8080/welcome.php?id=6&pid=1&hello=503
crystalrobe.ru :8080/welcome.php?id=0&pid=1
Client-side exploits serving domains (94.23.231.140; 91.121.115.208; 94.23.11.38; 94.23.224.221; 94.23.229.220) part of the campaign:
applecorn.com - Email: es@qx8.ru
areadrum.com - Email: qx@freenetbox.ru
busyspade.com - Email: baffle@freenetbox.ru
cafemack.com - Email: soy@qx8.ru
clanday.com - Email: elope@fastermail.ru
dnsofthost.com - Email: depot@infotorrent.ru
drunkjeans.com - Email: runway@5mx.ru
earlymale.com - Email: amply@maillife.ru
galslime.com - Email: soy@qx8.ru
gigasofa.com - Email: grind@fastermail.ru
hillchart.com - Email: soy@qx8.ru
hugejar.com - Email: runway@5mx.ru
ionicclock.com - Email: kin@maillife.ru
lasteye.com - Email: amply@maillife.ru
luckysled.com - Email: kin@maillife.ru
macrotub.com - Email: dodge@5mx.ru
oldgoal.com - Email: kin@maillife.ru
outerrush.com - Email: amply@maillife.ru
quietzero.com - Email: grind@fastermail.ru
radiomum.com - Email: es@qx8.ru
roundstorm.com - Email: es@qx8.ru
sadute.com - Email: grind@fastermail.ru
sheepbody.com - Email: es@qx8.ru
shinytower.com - Email: cord@maillife.ru
splatspa.com - Email: elope@fastermail.ru
tanspice.com - Email: dodge@5mx.ru
tanyear.com - Email: grind@fastermail.ru
tightsales.com - Email: runway@5mx.ru
tuneblouse.com - Email: es@qx8.ru
validplan.com - Email: dodge@5mx.ru
waxyblock.com - Email: cord@maillife.ru
allnext.ru - Email: swipe@maillife.ru
barnsoftware.ru - Email: people@bigmailbox.ru
bestbidline.ru - Email: jody@fastermail.ru
bestexportsite.ru - Email: orphan@qx8.ru
bittag.ru - Email: tips@freenetbox.ru
boozelight.ru - Email: ole@bigmailbox.ru
brandnewnet.ru - Email: orphan@qx8.ru
cangethelp.ru - Email: liver@freenetbox.ru
chainjoke.ru - Email: ole@bigmailbox.ru
comingbig.ru - Email: swipe@maillife.ru
countypath.ru - Email: liver@freenetbox.ru
crystalrobe.ru - Email: people@bigmailbox.ru
cupjack.ru - Email: tips@freenetbox.ru
dealyak.ru - Email: people@bigmailbox.ru
eyesong.ru - Email: tips@freenetbox.ru
familywater.ru - Email: ole@bigmailbox.ru
funsitedesigns.ru - Email: orphan@qx8.ru
galneed.ru - Email: people@bigmailbox.ru
girllab.ru - Email: tips@freenetbox.ru
greedford.ru - Email: ole@bigmailbox.ru
guntap.ru - Email: tips@freenetbox.ru
heroguy.ru - Email: ole@bigmailbox.ru
homecarenation.ru - Email: orphan@qx8.ru
homesitecam.ru - Email: orphan@qx8.ru
hookdown.ru - Email: crag@maillife.ru
horsedoctor.ru - Email: ole@bigmailbox.ru
jarpub.ru - Email: ole@bigmailbox.ru
liplead.ru - Email: ole@bigmailbox.ru
livesitedesign.ru - Email: orphan@qx8.ru
mansbestsite.ru - Email: orphan@qx8.ru
marketholiday.ru - Email: people@bigmailbox.ru
metalspice.ru - Email: ole@bigmailbox.ru
mingleas.ru - Email: crag@maillife.ru
motherfire.ru - Email: people@bigmailbox.ru
musicbestway.ru - Email: jody@fastermail.ru
musicsiteguide.ru - Email: crag@maillife.ru
netbesthelp.ru - Email: liver@freenetbox.ru
netwebinternet.ru - Email: dibs@freemailbox.ru
newagedirect.ru - Email: orphan@qx8.ru
newhomelady.ru - Email: orphan@qx8.ru
newinfoworld.ru - Email: orphan@qx8.ru
newworldunion.ru - Email: orphan@qx8.ru
ourfreesite.ru - Email: orphan@qx8.ru
panlip.ru - Email: tips@freenetbox.ru
pantscow.ru - Email: ole@bigmailbox.ru
problemdollars.ru - Email: people@bigmailbox.ru
raceobject.ru - Email: people@bigmailbox.ru
silencepill.ru - Email: ole@bigmailbox.ru
sisterqueen.ru - Email: ole@bigmailbox.ru
slaveday.ru - Email: ole@bigmailbox.ru
stareastwork.ru - Email: next@fastermail.ru
superblenderworld.ru - Email: crag@maillife.ru
superhoppie.ru - Email: soft@bigmailbox.ru
supertruelife.ru - Email: edsel@fastermail.ru
superwestcoast.ru - Email: crag@maillife.ru
theantimatrix.ru - Email: ole@bigmailbox.ru
tintie.ru - Email: swipe@maillife.ru
topmediasite.ru - Email: tips@freenetbox.ru
treecorn.ru - Email: tips@freenetbox.ru
trueblueally.ru - Email: soft@bigmailbox.ru
trueblueberyl.ru - Email: soft@bigmailbox.ru
tunemug.ru - Email: tips@freenetbox.ru
ushead.ru - Email: crag@maillife.ru
westbendonline.ru - Email: edsel@fastermail.ru
yaktrack.ru - Email: ole@bigmailbox.ru
yournewonline.ru - Email: orphan@qx8.ru
yourtolltag.ru - Email: orphan@qx8.ru
yourtruecrime.ru - Email: soft@bigmailbox.ru
zooneed.ru - Email: ole@bigmailbox.ru
Name servers of notice:
ns1.dnsofthost.com - 81.2.210.98
ns2.dnsofthost.com - 194.79.88.121
ns3.dnsofthost.com - 67.223.233.101
ns4.dnsofthost.com - 85.214.29.9
The NAUNET-REG-RIPN domain registrar, although, having already registered over a 100 ZeuS crimeware friendly domains, there's little chance they'll take action. Updates, including take down/remediation actions will be posted as soon as they emerge.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Thursday, July 15, 2010
Sampling Malicious Activity Inside Cybercrime-Friendly Search Engines
UPDATED, Friday, July 16, 2010 - Directi has suspended the domains portfolio of the cybercrime-friendly search engines.
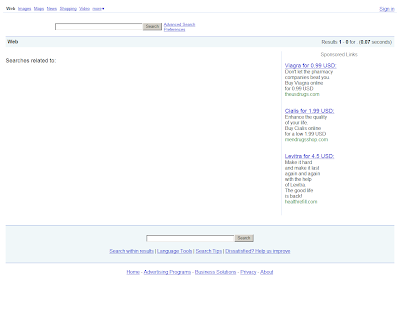
Cybercrime-friendly search engines are bogus search engines, which in between visually social engineering their users, offer fake results leading to client-side exploits, bogus video players dropping more malware, scareware, next to the pharmaceutical scams, and domain farms neatly embedded with Google AdSense scripts for monetization.
In the majority of cases -- whenever blackhat SEO is not an option -- end users are exposed the their maliciousness once they get infected with malware redirecting each and every request to popular search engines such as Google, Yahoo and Bing to the malicious IPs/domains operated by the cybercriminals.
As far as their monetization tactics are concerned, fellow cybercriminals are free to purchase any kind of keyword they want to, for instance "spyware", make it look like the end user is clicking on security-vendor.com's site, whereas upon clicking, based on his physical location a particular type of malicious activity takes place.
Remember the HOSTS file modification taking place courtesy of the malware at AS6851, BKCNET, Sagade Ltd., and in particular the Koobface gang related IP 89.149.210.109? Sampling the malicious activity within the search engines parked/forwarded (DNS recursion) from this IP, results in client-side exploits, bogus video players dropping malware, and scareware, and that in less than 5 minutes of testing.
The cybercrime-friendly domains in question:
searchclick1.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick2.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick3.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick4.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick5.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick6.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick7.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick8.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick9.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchclick10.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
searchmeup4.com - 78.159.112.46 - AS28753
zetaclicks4.com - 78.159.112.46 - AS28753
websafeclicks.com - Email: d.bond@mail.ru - 78.159.112.46 - AS28753
Internal redirections reading to malicious take place through the following domains:
7search.com - 12.171.94.40 - Email: webadmin@7search.com
greatseeking.com, superfindmea.info - 213.174.154.9 - Email: serdukov.art@gmail.com
superseeking.org - 213.174.154.9 - Email: serdukov.art@gmail.com
searching4all.com, pharmc9.com - 66.230.188.68 - Email: abuse@click9.com
syssmessage.com; sysstem-mesage.com; sys-mesage.com; potectmesage.com - 91.188.59.62 - Email: roroaleksey@gmail.com
xml.click9.com/click.php - 66.230.188.67 - Email: abuse@click9.com
sunday-traffic.com/in.php - 74.52.216.46 - Email: tech@add-manager.com
efindsite.info/search2.php - 74.52.216.46
greatseeking.com/search2.php - 213.174.154.9 - Email: serdukov.art@gmail.com
n-traff.com/clickn.php - 64.111.208.39
going-to-n.com/clickn.php - 64.111.208.38
everytds.tk/in.cgi?3=&ID=19504; onlyscan.tk; pornstaar.tk; dotroot.tk - 94.100.31.26
Internal pharmaceutical redirections take place through the following domains:
medsbrands.com - 74.52.216.46 - Email: tech@add-manager.com
thepillsdiscounts.info - 74.52.216.46 - Email: tech@add-manager.com
yourcatalogonline.biz - 74.52.216.46
bestderden.org - 74.52.216.46
Internal redirections reading to malicious take place through the following IPs:
199.80.55.19/go.php?data=
199.80.55.80/go.php?data=
78.140.141.18/kkk.php
78.140.143.83/go.php
64.111.212.234/c.php
64.111.196.126/c.php
66.230.188.67
68.169.92.61/c.php
68.169.92.60/c.php
68.169.93.242/c.php
68.169.92.55/c.php
Sample malicious activity consists of scareware campaigns, client-side exploits, and bogus video players dropping malware.
Upon visiting the bogus PornTube at vogel-tube.com/xfreeporn.php?id= - 66.197.187.118 (the-real-tube-best.com great-celebs-tube.net parked there) - Email: admin@thenweb.com the use is tricked into manually installing basemultimedia.com/video-plugin.45309.exe - 66.197.154.21 (visualbasismedia.com) - Email: joe@silentringer.com
- Detection rate
video-plugin.45309.exe - Downloader-CEW.b, Result: 6/42 (14.29%)
File size: 113152 bytes
MD5...: 25e644171bf9ee2a052b5fa71f8284e5
SHA1..: e4ac01534c7c1b71d2a38cf480339d31db187ecb
Upon execution, the sample phones back to:
best-arts-2010.com - 216.240.146.119 - Email:
hello-arts.com - 64.191.44.73 - Email:
youngfinearts.com - 64.20.35.3 - Email:
newchannelarts.com - 64.191.64.105 - Email:
vrera.com/oms.php - 208.43.125.180 - Email:
allxt.com/borders.php - 64.191.82.25
Parked at 216.240.146.119, AS7796 are also:
best-arts-2010.com - Email: aurora@seekrevenue.com
crystaldesignlab.com - Email: tamara.watson@chemist.com
homegraphicarts.com - Email: elizabethj@theplate.com
mediaartsplaza.com - Email: darhom@lendingears.com
morefinearts.net - Email: vdickerson37@yahoo.com
photoartsworld.com - Email: margaret_adams@rocketmail.com
pinehousearts.com - Email: jgaron@physicist.net
sunnyartsite.com - Email: jbowker@blader.com
thefanarts.com - Email: keasler@surferdude.com
waycoolart.com - Email: blynch@net-shopping.com
woodsmayart.com - Email: raymo@songwriter.net
garner.funtaff.com - Email: dph@greentooth.net
Parked at 64.191.44.73, AS21788 are also:
auctionhouseart.com - Email: emerynancy@ymail.com
bestmalearts.com - Email: mcfarlin@religions.com
coolcatart.com - Email: pbiron@catlover.com
freesurrealarts.com - Email: ghuertas@rocketmail.com
goldfireart.com - Email: thysell@gardener.com
greatmovieart.com - Email: linger@theplate.com
worldartsguide.com - Email: ghagen@allergist.com
install.netwaq.com - Email: admin@overseedomainmanagement.com
Parked at 64.20.35.3, AS19318 are also:
artscontact.net - Email: mschneider@doctor.com
catbodyart.com - Email: pbiron@catlover.com
feearts.com - Email: breckenridge56@hotmail.com
freeflasharts.com - Email: russell@clubmember.org
gardendesignart.com - Email: jasona@gardener.com
greatflashstudies.com - Email: jdeal@worshipper.com
superlegoarts.com - Email: jdeal@worshipper.com
thedigitalarts.com - Email: hoffman@theaterpillow.com
virginmegaart.com - Email: hoffman@theaterpillow.com
Related malicious domains sharing the same DNS infrastructure:
iransatnews.org
best-arts-2010.com - Email: aurora@seekrevenue.com
mediasite2010.com - Email: webmaster@pullstraws.com
setlamedia.com - Email: monro@eclipsetool.com
doublesetmedia.com - Email: monro@eclipsetool.com
thetestmedia.com - Email: webmaster@maidnews.com
trinitytestmedia.com - Email: webmaster@maidnews.com
i-metodika.com - Email: facovskiy__n__1977@rambler.ru
iffic.com
moviefactinc.com - Email: usa@crystals.com
newdataltd.com - Email: wenzel@techie.com
new-2010-tube.com - Email: fortney@petlover.com
super-world-tube.com - Email: fortney@petlover.com
real-good-tube.com - Email: fortney@petlover.com
green-real-tube.com - Email: sanctim59@yahoo.com
sensual-tube.com - Email: sanctim59@yahoo.com
webfilmoffice.com - Email: pam@skunkalert.com
xxl-tube-home.com
nowsearchonline.com
localmediasearch.com - Email: mega@stockdvds.com
mediaonsearch.com - Email: mega@stockdvds.com
mesghal.com - Email: shahnamgolshany@yahoo.com
niptoon.com
mydvdinfo.com - Email: usa@crystals.com
receptionist-pro.com
hitinto.com
importedfoodscorp.com - Email: apompeo@importedfoodscorp.com
newhavenfiles.com - Email: wenzel@techie.com
walterwagnerassociates.com
excellentutilites.com - Email: wentexkino@ymail.com
pengs.com
livingwithdragons.com - Email: gregory@lamerton.ltd.uk
amigroups.com
iransatnews.com
dvddatadirect.com - Email: friese@toke.com
itlist.com - Email: support@gossimer.biz
gossimer.net - Email: support@gossimer.biz
Following the bogus dropper, the cybercriminals are also directly serving client-side exploits to users seeking for security related content. In this case, the exploits/malware are served from xoxipemej.cn/gr/s1/ - 178.63.170.185 - Email: shiwei_fang77@126.com.
- Detection rate:
.exe - Rootkit.Agent.AJDR, Result: 20/42 (47.62%)
File size: 53760 bytes
MD5...: 23244c5b5b02fab65b3a7ab51005fd51
SHA1..: a5f1a10344378f2c8f13c266dce39247ba3bae5f
Parked on the same IP 178.63.170.185, AS24940 are also:
2011traff.com - Email: MillieDiaz4@aol.com
2011-traff.com - Email: MillieDiaz4@aol.com
bbbinvestigation.org - Email: accounting@moniker.com
best-sofa-choice.com - Email: migray71@yahoo.com
celloffer-2015.com - Email: migray71@yahoo.com
flying-city-2011.com - Email: migray71@yahoo.com
jiujitsufgua.com - Email: varcraft@care2.com
jopaduloz.cn - Email: qing_hongwei@126.com
lokexawan.cn - Email: shiwei_fang77@126.com
mapozeloq.cn - Email: shiwei_fang77@126.com
melonirmonianmonia.com - Email: accounting@moniker.com
mivaqodaz.cn - Email: shiwei_fang77@126.com
nasnedofweiggyt.com - Email: roller_59@hotmail.com
redolopip.cn - Email: shiwei_fang77@126.com
redspot2010.com - Email: migray71@yahoo.com
rohudufoj.cn - Email: qing_hongwei@126.com
sujelodos.cn - Email: qing_hongwei@126.com
traff2011.com - Email: MillieDiaz4@aol.com
traff-2012.com - Email: MillieDiaz4@aol.com
uweyujem.com - Email: resumemolars@live.com
viwuvefot.cn - Email: shiwei_fang77@126.com
wkeuhryyejt.com - Email: excins@iname.com
xoxipemej.cn - Email: shiwei_fang77@126.com
Last, but not least is the scareware infection taking place through www1.warezforyou24.co.cc/?p=p52 - 114.207.244.146; 114.207.244.143; 114.207.244.144; 114.207.244.145. Parked on these IPs is also an extensive portfolio of related scareware domains.
- Detection rate:
packupdate107_231.exe - Suspicious:W32/Malware!Gemini, Result: 3/42 (7.15%)
File size: 238080 bytes
MD5...: 93517875c59ac33dab655bc8432b0724
SHA1..: 774af049406baeef3427b91a2d67ee0250b2b51b
Upon execution the sample phones back to:
update2.cleanupyoursoft.com - 209.222.8.101 - Email: gkook@checkjemail.nl
update1.soft-cleaner.com - 95.169.186.25 - Email: gkook@checkjemail.nl
secure1.smartavz.com - 91.207.192.26 - Email: gkook@checkjemail.nl
report.mygoodguardian.com - 93.186.124.94 - Email: gkook@checkjemail.nl
www5.securitymasterav.com - 91.207.192.25 - Email: gkook@checkjemail.nl
update2.soft-cleaner.net - 209.222.8.100 - Email: gkook@checkjemail.nl
report.mytrueguardian.net - 79.171.23.150 - Email: gkook@checkjemail.nl
secure2.smartavz.net - 217.23.5.99 - Email: gkook@checkjemail.nl
update1.free-guard.com - Email: gkook@checkjemail.nl
report.mygoodguardian.com - 93.186.124.94 - Email: gkook@checkjemail.nl
update1.soft-cleaner.com - 95.169.186.25 - Email: gkook@checkjemail.nl
www5.securitymasterav.com - 91.207.192.25 - Email: gkook@checkjemail.nl
update2.soft-cleaner.net - 209.222.8.100 - Email: gkook@checkjemail.nl
report.mytrueguardian.net - 79.171.23.150 - Email: gkook@checkjemail.nl
The cybercrime-friendly domains portfolio is in a process of getting suspended.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Wednesday, July 14, 2010
Exploits, Malware, and Scareware Courtesy of AS6851, BKCNET, Sagade Ltd.
Never trust an AS whose abuse-mailbox is using a Gmail account (piotrek89@gmail.com), and in particular one that you've come across to during several malware campaigns over the past couple of month. It's AS6851, BKCNET "SIA" IZZI I'm referring to, also known as Sagade Ltd.
Let's dissect the currently ongoing malicious activity at that Latvian based AS, expose the exploit/malware/crimeware/scareware serving domain portfolios, sample some of the currently active binaries and emphasize on the hijacking of Google/Yahoo and Bing search engines, as well as take a brief retrospective of AS6851's activities profiled over the past couple of months.
What's so special about AS6851 anyway? It's the numerous times in which the AS popped-up in previously profiled campaigns (see related posts at the bottom of the post), next to a pretty interesting Koobface gang connection. An excerpt from a previous post:
"What's so special about AS6851, BKCNET "SIA" IZZI anyway? It's the Koobface gang connection in the face of urodinam.net, which is also hosted within AS6851, currently responding to 91.188.59.10. More details on urodinam.net:
Moreover, on the exact same IP where Koobface gang's urodinam.net is parked, we also have the currently active 1zabslwvn538n4i5tcjl.com - Email: michaeltycoon@gmail.com, serving client side exploits using the Yes Malware Exploitation kit - 91.188.59.10 /temp/cache/PDF.php; admin panel at: 1zabslwvn538n4i5tcjl.com /temp/admin/index.php
The same michaeltycoon@gmail.com used to register 1zabslwvn538n4i5tcjl.com, was also profiled in the "Diverse Portfolio of Scareware/Blackhat SEO Redirectors Courtesy of the Koobface Gang" assessment."
Related data on AS6851, BKCNET/Sagade Ltd.:
netname: ATECH-SAGADE
descr: Sagade Ltd.
descr: Latvia, Rezekne, Darzu 21
descr: +371 20034981
remarks: abuse-mailbox: piotrek89@gmail.com
country: LV
admin-c: JS1449-RIPE
tech-c: JS1449-RIPE
status: ASSIGNED PA
mnt-by: AS6851-MNT
source: RIPE # Filtered
person: Juris Sahurovs
remarks: Sagade Ltd.
address: Latvia, Rezekne, Darzu 21
phone: +371 20034981
abuse-mailbox: piotrek89@gmail.com
nic-hdl: JS1449-RIPE
mnt-by: ATECH-MNT
source: RIPE # Filtered
AS6851 advertises 15 prefixes:
* 62.84.0.0/19
* 62.84.22.0/23
* 84.38.128.0/20
* 85.234.160.0/19
* 91.123.64.0/20
* 91.188.32.0/19
* 91.188.41.0/24
* 91.188.44.0/23
* 91.188.46.0/24
* 91.188.48.0/23
* 91.188.50.0/24
* 91.188.52.0/23
* 91.188.56.0/24
* 109.110.0.0/19
* 195.244.128.0/20
Uplink courtesy of:
AS6747, LATTELEKOM Lattelekom
AS5518, TELIALATVIJA Telia Latvija SIA
Currently active exploits/malware/scareware serving domain portfolios within AS6851:
Parked at/responding to 85.234.190.15 are:
anrio.in - Email: Ometovgordey@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cogoo.in - Email: SamatovNail@mail.com
conyx.in - Email: NikitasZoya@mail.com
eboyx.in - Email: NikitasZoya@mail.com
ederm.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
foryx.in - Email: NikitasZoya@mail.com
liuyx.in - Email: NikitasZoya@mail.com
moosd.in - Email: VasilevaSvetlana@mail.com
oserr.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ostom.in - Email: skripnikkseniya@live.com
purnv.in - Email: BajenovOleg@mail.com
ragew.in - Email: vednerovasvetlana@gmail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
sdali.in - Email: VasilevaSvetlana@mail.com
seedw.in - Email: vednerovasvetlana@gmail.com
shkey.in - Email: FirulevAndrey@mail.com
spkey.in - Email: FirulevAndrey@mail.com
thynv.in - Email: BajenovOleg@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
wakey.in - Email: FirulevAndrey@mail.com
yxial.in - Email: GaevAlexandr@mail.com
Parked at/responding to 85.234.190.4 are:
anrio.in - Email: Ometovgordey@mail.com
antsd.in - Email: IvanovEvgeny@mail.com
appsd.in - Email: IvanovEvgeny@mail.com
arsdh.in - Email: shadrenkovavanda@mail.com
barui.in - Email: RijovAlexandr@mail.com
bkpuo.in - Email: erofeevalexey77@gmail.com
bleui.in - Email: RijovAlexandr@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
bryhw.in - Email: matatovayanna@mail.com
butui.in - Email: RijovAlexandr@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cirui.in - Email: RijovAlexandr@mail.com
cogoo.in - Email: RijovAlexandr@mail.com
conuo.in - Email: erofeevalexey77@gmail.com
conyx.in - Email: NikitasZoya@mail.com
cusnv.in - Email: SimakovSergey@mail.com
czkey.in - Email: ZaharcevSergey@mail.com
degoo.in - Email: SamatovNail@mail.com
dugoo.in - Email: SamatovNail@mail.com
ecrio.in - Email: Ometovgordey@mail.com
ectuo.in - Email: erofeevalexey77@gmail.com
ederm.in - Email: EvenkoIvan@mail.com
edger.in - Email: EvenkoIvan@mail.com
edimp.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
elrio.in - Email: Ometovgordey@mail.com
enguo.in - Email: erofeevalexey77@gmail.com
eqrio.in - Email: Ometovgordey@mail.com
fibnv.in - Email: SimakovSergey@mail.com
glouo.in - Email: erofeevalexey77@gmail.com
habsd.in - Email: LomaevaTatyana@mail.com
hecuo.in - Email: erofeevalexey77@gmail.com
hekey.in - Email: ZaharcevSergey@mail.com
hygos.in - Email: Hohlunovanika@live.com
imbos.in - Email: Hohlunovanika@live.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
latuo.in - Email: erofeevalexey77@gmail.com
linuo.in - Email: erofeevalexey77@gmail.com
makey.in - Email: ZaharcevSergey@mail.com
oscog.in - Email: Nigmatovaanastasia@hotmail.com
oserr.in - Email: skripnikkseniya@live.com
osmac.in - Email: skripnikkseniya@live.com
osmot.in - Email: skripnikkseniya@live.com
ospor.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ossio.in - Email: skripnikkseniya@live.com
ostab.in - Email: skripnikkseniya@live.com
ostac.in - Email: skripnikkseniya@live.com
ostio.in - Email: skripnikkseniya@live.com
ouned.in - Email: PoleschukovaGalina@mail.com
purnv.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
rekey.in - Email: ZaharcevSergey@mail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
scoos.in - Email: Nigmatovaanastasia@hotmail.com
sdali.in - Email: VasilevaSvetlana@mail.com
sdome.in - Email: OsvyanikovaDarya@mail.com
shkey.in - Email: FirulevAndrey@mail.com
spkey.in - Email: FirulevAndrey@mail.com
sydos.in - Email: Nigmatovaanastasia@hotmail.com
thynv.in - Email: BajenovOleg@mail.com
ugiyx.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
uithi.in - Email: IvanovEvgeny@mail.com
uityp.in - Email: IvanovEvgeny@mail.com
uityr.in - Email: IvanovEvgeny@mail.com
varyx.in - Email: GaevAlexandr@mail.com
wakey.in - Email: FirulevAndrey@mail.com
yokey.in - Email: FirulevAndrey@mail.com
yxiac.in - Email: GaevAlexandr@mail.com
yxial.in - Email: GaevAlexandr@mail.com
Parked at/responding to 91.188.60.225 are:
abrie.in - Email: Bodunovanton@mail.com
agros.in - Email: Hohlunovanika@live.com
alldh.in - Email: bondyashovandrey@mail.com
alodh.in - Email: radostovamariya@mail.com
anrio.in - Email: Ometovgordey@mail.com
antsd.in - Email: IvanovEvgeny@mail.com
aoxtv.in - Email: AkulovSergey@mail.com
appsd.in - Email: IvanovEvgeny@mail.com
aquui.in - Email: RijovAlexandr@mail.com
arrie.in - Email: Bodunovanton@mail.com
arsdh.in - Email: shadrenkovavanda@mail.com
balsd.in - Email: IvanovEvgeny@mail.com
barui.in - Email: RijovAlexandr@mail.com
bikey.in - Email: ZaharcevSergey@mail.com
bkpuo.in - Email: erofeevalexey77@gmail.com
bleui.in - Email: RijovAlexandr@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
bryhw.in - Email: matatovayanna@mail.com
butui.in - Email: RijovAlexandr@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cated.in - Email: PoleschukovaGalina@mail.com
cedhw.in - Email: lopushkoamariya@mail.com
chrie.in - Email: Bodunovanton@mail.com
chrio.in - Email: Ometovgordey@mail.com
cirui.in - Email: RijovAlexandr@mail.com
clrio.in - Email: Ometovgordey@mail.com
cogoo.in - Email: SamatovNail@mail.com
conuo.in - Email: erofeevalexey77@gmail.com
conyx.in - Email: NikitasZoya@mail.com
corie.in - Email: Bodunovanton@mail.com
curie.in - Email: Bodunovanton@mail.com
cusnv.in - Email: SimakovSergey@mail.com
czkey.in - Email: ZaharcevSergey@mail.com
degoo.in - Email: SamatovNail@mail.com
dennv.in - Email: SimakovSergey@mail.com
dugoo.in - Email: SamatovNail@mail.com
eagoo.in - Email: SamatovNail@mail.com
eboyx.in - Email: NikitasZoya@mail.com
ecrio.in - Email: Ometovgordey@mail.co
ectuo.in - Email: erofeevalexey77@gmail.com
edbal.in - Email: VasilevOleg@mail.com
edban.in - Email: VasilevOleg@mail.com
ederc.in - Email: EvenkoIvan@mail.com
ederm.in - Email: EvenkoIvan@mail.com
edger.in - Email: EvenkoIvan@mail.com
edimp.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
elrio.in - Email: Ometovgordey@mail.com
enguo.in - Email: erofeevalexey77@gmail.com
eprio.in - Email: Ometovgordey@mail.com
eqrio.in - Email: Ometovgordey@mail.com
esrie.in - Email: Bodunovanton@mail.com
fakey.in - Email: ZaharcevSergey@mail.com
fegoo.in - Email: SamatovNail@mail.com
fibnv.in - Email: SimakovSergey@mail.com
foryx.in - Email: NikitasZoya@mail.com
franv.in - Email: SimakovSergey@mail.com
fraos.in - Email: Hohlunovanika@live.com
garie.in - Email: Bodunovanton@mail.com
glouo.in - Email: erofeevalexey77@gmail.com
guinv.in - Email: SimakovSergey@mail.com
habsd.in - Email: LomaevaTatyana@mail.com
hecuo.in - Email: erofeevalexey77@gmail.com
hekey.in - Email: ZaharcevSergey@mail.com
humos.in - Email: Hohlunovanika@live.com
hygos.in - Email: Hohlunovanika@live.com
hyrie.in - Email: Bodunovanton@mail.com
imbos.in - Email: Hohlunovanika@live.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
jobos.in - Email: Hohlunovanika@live.com
kykey.in - Email: ZaharcevSergey@mail.com
latuo.in - Email: erofeevalexey77@gmail.com
leunv.in - Email: SimakovSergey@mail.com
linuo.in - Email: erofeevalexey77@gmail.com
liuyx.in - Email: NikitasZoya@mail.com
makey.in - Email: ZaharcevSergey@mail.com
moosd.in - Email: VasilevaSvetlana@mail.com
naios.in - Email: Hohlunovanika@live.com
nvenc.in - Email: BajenovOleg@mail.com
oscog.in - Email: Nigmatovaanastasia@hotmail.com
osenc.in - Email: Nigmatovaanastasia@hotmail.com
oserr.in - Email: skripnikkseniya@live.com
osmac.in - Email: skripnikkseniya@live.com
osmot.in - Email: skripnikkseniya@live.com
ospor.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ossio.in - Email: skripnikkseniya@live.com
ostab.in - Email: skripnikkseniya@live.com
ostac.in - Email: skripnikkseniya@live.com
ostio.in - Email: skripnikkseniya@live.com
ostom.in - Email: skripnikkseniya@live.com
ouned.in - Email: PoleschukovaGalina@mail.com
purnv.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
ragew.in - Email: vednerovasvetlana@gmail.com
rekey.in - Email: ZaharcevSergey@mail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
saled.in - Email: VasilevOleg@mail.com
sated.in - Email: VasilevOleg@mail.com
scoos.in - Email: Nigmatovaanastasia@hotmail.com
sdali.in - Email: VasilevaSvetlana@mail.com
sdall.in - Email: VasilevaSvetlana@mail.com
sdayb.in - Email: OsvyanikovaDarya@mail.com
sdaye.in - Email: OsvyanikovaDarya@mail.com
sdayo.in - Email: OsvyanikovaDarya@mail.com
sdene.in - Email: OsvyanikovaDarya@mail.com
sdich.in - Email: OsvyanikovaDarya@mail.com
sdome.in - Email: OsvyanikovaDarya@mail.com
seedw.in - Email: vednerovasvetlana@gmail.com
shkey.in - Email: FirulevAndrey@mail.com
smoed.in - Email: VasilevOleg@mail.com
soted.in - Email: VasilevOleg@mail.com
spios.in - Email: Nigmatovaanastasia@hotmail.com
spkey.in - Email: FirulevAndrey@mail.com
stteop.in - Email: fibra_appl@yahoo.com
sunyx.in - Email: GaevAlexandr@mail.com
sydos.in - Email: Nigmatovaanastasia@hotmail.com
teaed.in - Email: VasilevOleg@mail.com
thynv.in - Email: BajenovOleg@mail.com
ugiyx.in - Email: GaevAlexandr@mail.com
uinei.in - Email: UshakovAndrey@mail.com
uinge.in - Email: UshakovAndrey@mail.com
uiren.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uisee.in - Email: UshakovAndrey@mail.com
uisma.in - Email: IvanovEvgeny@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
uithi.in - Email: IvanovEvgeny@mail.com
uityp.in - Email: IvanovEvgeny@mail.com
uityr.in - Email: IvanovEvgeny@mail.com
varyx.in - Email: GaevAlexandr@mail.com
veged.in - Email: VasilevOleg@mail.com
wakey.in - Email: FirulevAndrey@mail.com
whasd.in - Email: VasilevaSvetlana@mail.com
wimed.in - Email: VasilevOleg@mail.com
woonv.in - Email: BajenovOleg@mail.com
yokey.in - Email: FirulevAndrey@mail.com
yxiac.in - Email: GaevAlexandr@mail.com
yxial.in - Email: GaevAlexandr@mail.com
yxiam.in - Email: GaevAlexandr@mail.com
Parked at/responding to 91.188.60.3 are:
0checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
10checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
20checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
30checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
40checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
50checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
60checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
70checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
80checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
90checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
av-scaner-onlinemachine.com - Email: gershatv07@gmail.com
easy-ns-server.org - Email: russell1985@hotmail.com
fast-scanerr-online.org - Email: roberson@hotmail.com
fast-scanneronline.org - Email: roberson@hotmail.com
fastscanner-online.org - Email: roberson@hotmail.com
fastscannerr-online.org - Email: roberson@hotmail.com
myantivirsplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirsplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirusplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirus-plus.org - Email: FranciscoPGeorge@hotmail.com
myprotectonline.org - Email: FranciscoPGeorge@hotmail.com
my-protectonline.org - Email: FranciscoPGeorge@hotmail.com
my-protect-online.org - Email: FranciscoPGeorge@hotmail.com
sysprotectonline.org - Email: FranciscoPGeorge@hotmail.com
sys-protectonline.org - Email: FranciscoPGeorge@hotmail.com
sys-protect-online.org - Email: FranciscoPGeorge@hotmail.com
Parked at/responding to 91.188.59.74 are:
allforil1i.com - Email: lordjok@gmail.com
alltubeforfree.com - Email: lordjok@gmail.com
allxtubevids.net - Email: lordjok@gmail.com
downloadfreenow.in - Email: lordjok@gmail.com
enteri1llisec.in - Email: leshapopovi@gmail.com
freeanalsextubemovies.com - Email: lordjok@gmail.com
freetube06.com - Email: lordjok@gmail.com
freeviewgogo.com - Email: leshapopovi@gmail.com
homeamateurclips.com - Email: lordjok@gmail.com
hot4youxxx.in - Email: lordjok@gmail.com
hotxtube.in - Email: lordjok@gmail.com
hotxxxtubevideo.com
iil10oil0.com
ilio01ili1.com
illinoli1l.in - Email: lordjok@gmail.com
porntube2000.com - Email: welolseeees@gmail.com
porntubefast.com - Email: welolseeees@gmail.com
porn-tube-video.com - Email: welolseeees@gmail.com
viewnowfast.com - Email: lordjok@gmail.com
viewxxxfreegall.net - Email: leshapopovi@gmail.com
viiistifor1.com
xhuilil1ii.com - Email: lordjok@gmail.com
youvideoxxx.com - Email: jonnytrade@gmail.com
Parked at/responding to 85.234.190.16 are:
appsd.in - Email: IvanovEvgeny@mail.com
bikey.in - Email: IvanovEvgeny@mail.com
fibnv.in - Email: SimakovSergey@mail.com
franv.in - Email: SimakovSergey@mail.com
guinv.in - Email: SimakovSergey@mail.com
hekey.in - Email: ZaharcevSergey@mail.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
leunv.in - Email: SimakovSergey@mail.com
nvenc.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
uinei.in - Email: GaleevDjamil@mail.com
uinge.in - Email: UshakovAndrey@mail.com
uiren.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uisee.in - Email: UshakovAndrey@mail.com
woonv.in - Email: BajenovOleg@mail.com
yxiam.in - Email: GaevAlexandr@mail.com
Detection rates for the currently active malware samples, including the HOSTS file modifications on infected hosts, for the purposely of redirecting users to cybercrime-friendly search engines, monetized through traffic trading affiliate programs.
- 78490.jar - Result: 0/42 (0%)
File size: 209 bytes
MD5 : 64a19d9b7f0e81c7a5f6d63853a3ed49
SHA1 : 9f8f208c8cdb854cdc342d43a75a3d8672e87822
- ad3.exe - Result: 41/42 (97.62%)
File size: 2560 bytes
MD5...: 9362a3aee38102dde68211ccb63c3e07
SHA1..: 8758679540f48feba82d2b022b8d71756eb935e7
- a-fast.exe - Result: 36/42 (85.72%)
File size: 979968 bytes
MD5...: 69f3949141073679b77aa4d34e41a3e7
SHA1..: e074de46e4760eef522ab85737790058cc3f2fad
- dm.exe - Result: 37/42 (88.1%)
File size: 83968 bytes
MD5...: b658d9b812454e99b2915ab2e9594b94
SHA1..: 134bfb643ae2f161c99db14c448485e261e96c91
- iv.exe - Result: 8/42 (19.05%)
File size: 86016 bytes
MD5...: f94ed2f9d7a672fe3ff8bf077289b2d5
SHA1..: 2f78a296e1267ae1cf9ebd5c18de5b8d241c1306
- j2_t895.jar - Result: 0/42 (0%)
File size: 211 bytes
MD5...: 4b34618a0499a99e9c98e03aa79d53cf
SHA1..: d109babf78ec48ba8d7798bce784097ed26757db
- movie.exe - Result: 40/42 (95.24%)
File size: 64866 bytes
MD5...: 801f9fa958192b6714a5a4c2e2f92f07
SHA1..: 241bc9d7540d9d53cc1578e3d57c44be9931e418
- tst.exe - Result: 35/42 (83.34%)
File size: 356352 bytes
MD5...: b0ed4701af13f11089de850a1273d24f
SHA1..: 5e98000b60d0ca0b2adbd837feaf05f439f95c87
- wsc.exe - Result: 37/42 (88.1%)
File size: 24576 bytes
MD5...: 80427b754b11de653758dd5e1ba3de1c
SHA1..: 554e1331fdc050bd603f6f3628285008a91cba37
HOSTS file modification:
AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
89.149.210.109 www.google.com
89.149.210.109 www.google.de
89.149.210.109 www.google.fr
89.149.210.109 www.google.co.uk
89.149.210.109 www.google.com.br
89.149.210.109 www.google.it
89.149.210.109 www.google.es
89.149.210.109 www.google.co.jp
89.149.210.109 www.google.com.mx
89.149.210.109 www.google.ca
89.149.210.109 www.google.com.au
89.149.210.109 www.google.nl
89.149.210.109 www.google.co.za
89.149.210.109 www.google.be
89.149.210.109 www.google.gr
89.149.210.109 www.google.at
89.149.210.109 www.google.se
89.149.210.109 www.google.ch
89.149.210.109 www.google.pt
89.149.210.109 www.google.dk
89.149.210.109 www.google.fi
89.149.210.109 www.google.ie
89.149.210.109 www.google.no
89.149.210.109 search.yahoo.com
89.149.210.109 us.search.yahoo.com
89.149.210.109 uk.search.yahoo.com
- rc.exe - Result: 41/42 (97.62%)
File size: 2560 bytes
MD5...: 9362a3aee38102dde68211ccb63c3e07
SHA1..: 8758679540f48feba82d2b022b8d71756eb935e7
HOSTS file modification:
AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
89.149.249.196 www.google.com
89.149.249.196 www.google.de
89.149.249.196 www.google.fr
89.149.249.196 www.google.co.uk
89.149.249.196 www.google.com.br
89.149.249.196 www.google.it
89.149.249.196 www.google.es
89.149.249.196 www.google.co.jp
89.149.249.196 www.google.com.mx
89.149.249.196 www.google.ca
89.149.249.196 www.google.com.au
89.149.249.196 www.google.nl
89.149.249.196 www.google.co.za
89.149.249.196 www.google.be
89.149.249.196 www.google.gr
89.149.249.196 www.google.at
89.149.249.196 www.google.se
89.149.249.196 www.google.ch
89.149.249.196 www.google.pt
89.149.249.196 www.google.dk
89.149.249.196 www.google.fi
89.149.249.196 www.google.ie
89.149.249.196 www.google.no
89.149.249.196 www.google.co.in
89.149.249.196 search.yahoo.com
89.149.249.196 us.search.yahoo.com
89.149.249.196 uk.search.yahoo.com
- installer.0028.exe - Result: 9/42 (21.43%)
File size: 43735 bytes
MD5...: a6d7073b8b9bc0dc539605914c853da2
SHA1..: 1940b6a6b2f93b44633ef04eab900e0a9dc6fa64
HOSTS file modification:
AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
84.16.244.60 www.google.com
84.16.244.60 us.search.yahoo.com
84.16.244.60 uk.search.yahoo.com
84.16.244.60 search.yahoo.com
84.16.244.60 www.google.com.br
84.16.244.60 www.google.it
84.16.244.60 www.google.es
84.16.244.60 www.google.co.jp
84.16.244.60 www.google.com.mx
84.16.244.60 www.google.ca
84.16.244.60 www.google.com.au
84.16.244.60 www.google.nl
84.16.244.60 www.google.co.za
84.16.244.60 www.google.be
84.16.244.60 www.google.gr
84.16.244.60 www.google.at
84.16.244.60 www.google.se
84.16.244.60 www.google.ch
84.16.244.60 www.google.pt
84.16.244.60 www.google.dk
84.16.244.60 www.google.fi
84.16.244.60 www.google.ie
84.16.244.60 www.google.no
84.16.244.60 www.google.de
84.16.244.60 www.google.fr
84.16.244.60 www.google.co.uk
84.16.244.60 www.bing.com
- installer.0022.exe - Result: 9/42 (21.43%)
File size: 43731 bytes
MD5...: 62464b9e367a9edb06541a2a90931157
SHA1..: 425c859a883900ccf5cf7b8a6a5f6bc9279d763c
HOSTS file modification:
AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
84.16.244.15 www.google.com
84.16.244.15 us.search.yahoo.com
84.16.244.15 uk.search.yahoo.com
84.16.244.15 search.yahoo.com
84.16.244.15 www.google.com.br
84.16.244.15 www.google.it
84.16.244.15 www.google.es
84.16.244.15 www.google.co.jp
84.16.244.15 www.google.com.mx
84.16.244.15 www.google.ca
84.16.244.15 www.google.com.au
84.16.244.15 www.google.nl
84.16.244.15 www.google.co.za
84.16.244.15 www.google.be
84.16.244.15 www.google.gr
84.16.244.15 www.google.at
84.16.244.15 www.google.se
84.16.244.15 www.google.ch
84.16.244.15 www.google.pt
84.16.244.15 www.google.dk
84.16.244.15 www.google.fi
84.16.244.15 www.google.ie
84.16.244.15 www.google.no
84.16.244.15 www.google.de
84.16.244.15 www.google.fr
84.16.244.15 www.google.co.uk
84.16.244.15 www.bing.com
The payment gateway structure+related domains for the scareware campaigns:
- fast-payments.com/index.php?prodid=antus_02_01&afid= - 91.188.59.27 - Email: jclarke980@gmail.com
- ns1.fastsecurebilling.com - 91.188.59.26 - Email: jclarke980@gmail.com
- easypayments-online.com - 91.188.59.28 - Email: jclarke980@gmail.com
- fast-payments.com - 91.188.59.27 - Email: jclarke980@gmail.com
- billingonline.net - 91.188.59.29 - Email: kevbush@billingonline.net
- billsolutions.net - 91.188.59.25
In respect to the IPs used in HOSTS file modification, one is of particular interest - 89.149.210.109, as it was first profiled in November, 2009's "Koobface Botnet's Scareware Business Model - Part Two" with MD5: 0fbf1a9f8e6e305138151440da58b4f1 modifying HOSTS file using the same IP, and also phoning back to the Koobface gang's 1.0 hardcore C&C - urodinam.net/8732489273.php
When it comes to cybercrime, there's no such thing as a coincidence. What's static is the interaction between the usual suspects, systematically switching hosting providers, introducing new domains, and conveniently denying their monetization tactics.
You wish.
Profiled AS6851, BKCNET/Sagade Ltd. activity:
GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
Dissecting the Mass DreamHost Sites Compromise
Spamvertised iTunes Gift Certificates and CV Themed Malware Campaigns
Dissecting the 100,000+ Scareware Serving Fake YouTube Pages Campaign
Facebook Photo Album Themed Malware Campaign, Mass SQL Injection Attacks Courtesy of AS42560
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, July 13, 2010
Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
Cybercrime ecosystem irony, at its best. Why the irony? Because the cybercrime-friendly proxies service TOS explicitly states that its users cannot launch XSS/SQL injection attacks through it.
A relatively low profile cybercriminal has managed to exploit a remote SQL injection within a popular proxies service, offering access to compromised hosts across the globe for any kind of malicious activities. Based on the video released, he was able to access everyone's password as MD5 hash, next to the emulating of the users of the service, using a trivial flaw in the online.cgi script.
Although his intentions, based on the note left in a readme.txt file featured in the video, was to allow others to use the paid service freely, the potential for undermining the OPSEC of cybercriminals using the service is enormous, as it not only logs their financial transactions, keeps records of their IPs, but most interestingly, allows the "manual feeding" of proxy lists (compromised and freely accessible hosts) within the database.
The service itself, has been in operation since 2004, operating under different brands, with prices starting from $20 to $90 for access to 150, and 1500 hosts on a monthly basis. Some interesting facts from a threat intell/social network analysis perspective, including screenshots (on purposely blurred in order to prevent the ruining of important OSINT sources) of the service obtained from its help file.
- The gang/hacking/script kiddies team operates different business operations online
- They maintain a traffic purchasing program monetizing traffic through cybercrime-friendly search engines
- Whether they are lazy, or just don't care, 4 currently active adult web sites share the same infrastructure as the service itself
- Although the original owners are Russian, they appear to be franchising since once of their brands is offering their services in Indonesian, including a banner for what looks like a Indonesian security conference.
- One of the Indonesian franchisers is known to have been offering root accounts and shells at compromised servers for sale, back in 2007
For years, compromised malware hosts has been widely abused for anything, from direct spamming, to hosting spam/phishing and malware campaigns, but most importantly - to engineer cyber warfare tensions by directly forwarding the responsibility for the malicious actions of the cybercriminal/cyber spy to the host/network/country in question.
Not only do these tactics undermine the currently implemented data retention regulations -- how can you data retain something from a compromised ecosystem that keeps no logs -- but also, they offer a safe heaven for the execution of each and every cybercriminal practice there is.
Related posts:
Should a targeted country strike back at the cyber attackers?
Malware Infected Hosts as Stepping Stones
The Cost of Anonymizing a Cybercriminal's Internet Activities
The Cost of Anonymizing a Cybercriminal's Internet Activities - Part Two
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Subscribe to:
Posts (Atom)