Dissecting the Xerox WorkCentre Pro Scanned Document Themed Campaign
0Over the weekend, a "Scan from a Xerox WorkCentre Pro" themed malware campaign relying on zip archives, was actively spamvertised by cybecriminals seeking to infect gullible end/corporate users.
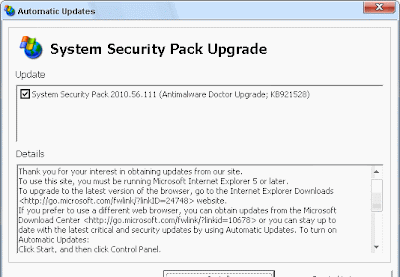
What's particularly interesting about this campaign, is the cocktail of malware dropped on infected hosts, including Asprox sample (Money Mule Recruiters use ASProx's Fast Fluxing Services), and two separate samples of Antimalware Doctor.
- Sample subject: Scan from a Xerox WorkCentre Pro $9721130
- Sample message: "Please open the attached document. It was scanned and sent to you using a Xerox WorkCentre Pro.
Sent by: Guest
Number of Images: 1
Attachment File Type: ZIP [DOC]
WorkCentre Pro Location: machine location not set Device Name: XRX2090AA7ACDB45466972. For more information on Xerox products and solutions, please visit http://www.xerox.com"
- Detection rates:
- Xerox_doc1.exe - Trojan.Win32.Jorik.Oficla.bb - Result: 34/42 (80.96%)
File size: 30926 bytes
MD5...: 1d378a6bc94d5b5a702026d31c21e242
SHA1..: 545e83f547d05664cd6792e254b87539fba24eb9
- Xerox_doc2.exe - Trojan.Win32.Jorik.Oficla.ba - Result: 34/42 (80.96%)
File size: 43520 bytes
MD5...: 829c86d4962f186109534b669ade47d7
SHA1..: 5d3d02d0f6ce87cd96a34b73dc395460d623616e
The samples then phone back to the Oficla/Sasfis C&Cs at hulejsoops.ru/images/bb.php?v=200&id=554905388&b=avpsales&tm=3 - 91.216.215.66, AS51274 - Email: mxx3@yandex.ru which periodically rotates three different executables using the following URLs:
0815.ch /pic/view.exe
curseri.ch /pictures/securedupdaterfix717.exe
regionalprodukte-beo.ch /about/cgi.exe
Backup URLS:
leeitpobbod.ru/image/bb.php - 59.53.91.195, AS4134 - Email: mxx3@yandex.ru - dead response
loloohuildifsd.ru/image/bb.php - 68.168.222.158 - Email: mxx3@yandex.ru - dead response
nemohuildifsd.ru/image/bb.php - 59.53.91.195 (nemohuildiin.ru, russianmomds.ru), AS4134 - Email: mxx3@yandex.ru - dead response
Let's take a peek at the samples found within the C&C.
view.exe - Trojan.Win32.Jorik.Aspxor.e - Result: 11/42 (26.2%)
File size: 79360 bytes
MD5...: 5d296fe1ef7bf67f36fe9adb209398ee
SHA1..: 41b45bcd241cd97b72d7866d13c4a0eb6bf6a0ee
Upon execution, the sample phones back to well known Asprox C&Cs:
cl63amgstart.ru: 80/board.php - 91.213.217.4, AS42473 - Email: ssa1@yandex.ru
hypervmsys.ru: 80/board.php - 89.149.223.232 (hostagents.ru), AS28753 - Email: vadim.rinatovich@yandex.ru
Previously, all of the following ASPRox domains used exclusively for massive SQL injections, used to respond to 91.213.217.4:
webservicesbba.ru - Email: anrnews@mail.ru
webservicelupa.ru - Email: anrnews@mail.ru
webserivcekota.ru - Email: anrnews@mail.ru
webservicesrob.ru - Email: anrnews@mail.ru
webserivcezub.ru - Email: anrnews@mail.ru
webserviceforward.ru - Email: anrnews@mail.ru
webserivcessh.ru - Email: anrnews@mail.ru
webservicesmulti.ru - Email: anrnews@mail.ru
webservicezok.ru - Email: anrnews@mail.ru
webservicebal.ru - Email: anrnews@mail.ru
webservicefull.ru - Email: anrnews@mail.ru
webservicessl.ru - Email: anrnews@mail.ru
webserviceaan.ru - Email: anrnews@mail.ru
webservicedevlop.ru - Email: anrnews@mail.ru
webserviceftp.ru - Email: anrnews@mail.ru
hypervmsys.ru - Email: anrnews@mail.ru
webserviceget.ru - Email: anrnews@mail.ru
webserviceskot.ru - Email: anrnews@mail.ru
cl63amgstart.ru - Email: ssa1@yandex.ru
ml63amgstart.ru - Email: ssa21@yandex.ru
webservicesttt.ru - Email: anrnews@mail.ru
webservicenow.ru - Email: anrnews@mail.ru
webservicekuz.ru - Email: anrnews@mail.ru
Currently, the gang's migrating this infrastructure to 109.196.134.58, AS39150, VLTELECOM-AS VLineTelecom LLC Moscow, Russia.
All of these domains+subdomains sharing the same js.js directory structure, which upon visiting loads URLs such as (accesspad.ru :8080/index.php?pid=6) with the rest of the domains sharing the same infrastructure as the ones profiled in "Spamvertised Amazon "Verify Your Email", "Your Amazon Order" Malicious Emails" post:
access.webservicebal.ru
admin.webserivcekota.ru
api.webserivcessh.ru
app.webserviceforward.ru
app.webservicesrob.ru
base.webserviceftp.ru
batch.webserviceaan.ru
batch.webservicebal.ru
bios.webservicesbba.ru
block.webserviceaan.ru
block.webservicesrob.ru
cache.webservicesbba.ru
cache.webservicesmulti.ru
chk.webservicezok.ru
cmdid.webserivcezub.ru
code.webservicesbba.ru
com.webserivcekota.ru
com.webservicedevlop.ru
ddk.webservicesrob.ru
default.webservicezok.ru
diag.webserviceftp.ru
direct.webserviceftp.ru
dll.webservicelupa.ru
drv.webservicebal.ru
drv.webservicesrob.ru
encode.webservicefull.ru
err.webserivcessh.ru
export.webservicedevlop.ru
ext.webserviceaan.ru
ext.webservicesbba.ru
file.webserivcekota.ru
file.webserivcessh.ru
filter.webservicedevlop.ru
font.webservicelupa.ru
gdi.webserviceftp.ru
get.webservicesbba.ru
go.webserivcekota.ru
go.webservicefull.ru
guid.webserivcezub.ru
hostid.webservicesbba.ru
hostid.webservicesmulti.ru
http.webserviceforward.ru
icmp.webservicesbba.ru
id.webserivcezub.ru
inf.webserviceaan.ru
info.webservicedevlop.ru
ini.webservicesrob.ru
ioctl.webservicedevlop.ru
kernel.webservicezok.ru
lan.webservicefull.ru
lan.webservicesbba.ru
lib.webservicebal.ru
lib.webserviceftp.ru
libid.webservicelupa.ru
load.webservicebal.ru
locate.webservicelupa.ru
log.webservicelupa.ru
log.webservicezok.ru
log-in.webservicessl.ru
manage.webservicesbba.ru
map.webserivcezub.ru
map.webservicedevlop.ru
media.webserviceftp.ru
mode.webservicelupa.ru
net.webservicebal.ru
netapi.webserviceaan.ru
netmsg.webserivcezub.ru
ns1.webservicelupa.ru
ns2.webservicelupa.ru
ntdll.webservicessl.ru
ntio.webservicelupa.ru
ntio.webservicezok.ru
obj.webservicesbba.ru
object.webserivcessh.ru
object.webservicesmulti.ru
oem.webservicebal.ru
offset.webservicefull.ru
ole.webservicesbba.ru
org.webservicesrob.ru
page.webserviceaan.ru
parse.webservicebal.ru
peer.webserviceaan.ru
pic.webservicesbba.ru
pool.webservicelupa.ru
port.webservicebal.ru
port.webservicesbba.ru
port.webservicessl.ru
proc.webserviceaan.ru
proc.webservicessl.ru
rdir.webserviceftp.ru
redir.webservicedevlop.ru
refer.webserivcezub.ru
reg.webserviceaan.ru
remote.webservicessl.ru
run.webserivcekota.ru
script.webserivcezub.ru
sdk.webserivcezub.ru
search.webserviceaan.ru
search.webservicedevlop.ru
setup.webserivcezub.ru
setup.webservicezok.ru
snmp.webserviceforward.ru
snmp.webservicesrob.ru
sslcom.webserivcessh.ru
sslcom.webservicesrob.ru
sslid.webserivcekota.ru
sslnet.webservicedevlop.ru
svc.webservicedevlop.ru
tag.webservicebal.ru
tag.webservicessl.ru
tid.webserviceftp.ru
time.webservicelupa.ru
udp.webserviceftp.ru
udp.webservicezok.ru
update.webserviceftp.ru
update.webservicefull.ru
url.webservicesbba.ru
url.webservicezok.ru
vba.webservicesrob.ru
vbs.webservicelupa.ru
ver.webserivcekota.ru
webserivcekota.ru
webserivcessh.ru
webserivcezub.ru
webserviceaan.ru
webservicebal.ru
webservicedevlop.ru
webserviceforward.ru
webserviceftp.ru
webservicefull.ru
webserviceget.ru
webservicelupa.ru
webservicesmulti.ru
webservicesrob.ru
webservicessl.ru
webservicezok.ru
win.webservicezok.ru
xml.webservicefull.ru
Getting back to the samples rotated by the original campaign binary, and their detection rates, network interactions.
- Detection rates:
- securedupdaterfix717.exe - Trojan.Win32.FakeYak - Result: 22/42 (52.39%)
File size: 36864 bytes
MD5...: cd16d4c998537248e6d4d0a3d51ca6de
SHA1..: 7e36ef0ce85fac18ecffd5a82566352ce0322589
Phones back to:
s.ldwn.in/inst.php?fff=7071710000&saf=ru - 91.188.60.236 (updget.in; wordmeat.in), AS6851 - Email: feliciachappell@ymail.com
bootfree.in/ MainModule717release10000.exe - 194.8.250.207 (flowload.in; lessown.in; sstats.in), AS43134 - Email: feliciachappell@ymail.com
s.wordmeat.in/install.php?coid= - 91.188.60.236, AS6851 - Email: feliciachappell@ymail.com
- Detection rate for MainModule717release10000.exe
- MainModule717release10000.exe - Trojan:Win32/FakeYak - Result: 26/42 (61.90%)
File size: 1043968 bytes
MD5...: 3c30c62e9981bd86c5897447cb358235
SHA1...: 36bfc285a61bcb67f2867dd303ac3cefa0e490a0
Phones back to:
wordmeat.in - 91.188.60.236 - Email: feliciachappell@ymail.com
vismake.in - 91.188.60.236 - Email: keelingelizabeth@ymail.com
- Detection rate for the 3rd binary rotated in the original C&C:
- cgi.exe - Trojan.Inject.8960 - Result: 6/42 (14.29%)File size: 62976 bytes
MD5...: 45c062490e0fc262c181efc323cb83ba
SHA1..: bff90630f2064d7bcc82b7389c2b8525ff960870
Phones back to:
musiceng.ru /music/forum/index1.php - 91.212.127.40, AS49087 - Email: ol.feodosoff@yandex.ru
The whole campaign, is a great example of what cybercrime underground multitasking is all about. Moreover, it illustrates the interactions between the usual suspects, with the not so surprising appearance of the already profiled AS6851, BKCNET, Sagade Ltd.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.






0 Comments: