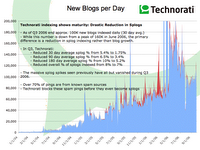
Very good article on various geopolitical issues related to the Middle East vs the West, and most importantly an overview of the
current state of online jihad. Excluding webcasts, video howto's, and video games as a commodity in the big picture, what's left at the bottom line is easily accessible open source intelligence, and tactical warfare practices such as this one :
"
Some of the techniques of evasion are disarmingly simple. Rather than send emails, some jihadists simply write and save draft emails, storing them in an account with a password that's known to other members of the cell. Because they are never actually sent, they can't be detected by intelligence agencies."
Can you intercept an email that's never been sent? And what if a legitimate user's account end up as a dead box? Moreover, the article points out to the recently released
Technical Mujahid magazine :
"
Raisman points to a recent publication by the al-Fajr group, another communications arm of al-Qaeda and its fellow travellers. He said it contained a very sophisticated manual on internet security, how to avoid hackers, secure personal files and ensure any computer that is captured is of little value to Western authorities."
Going through the magazine itself as I indeed obtained a copy and will publish a summary of it anytime now, there's nothing really that very sophisticated to be afraid of, unless you know nothing about installing a virtual machine, or what triangulation is all about.
A handy summary of the article and things to keep in mind :
- There are over 5000 militant Islamic websites, up from less than a dozen in 1998 -- these are only the static ones compared to hundreds more temporary campaign ones
- They are an extremely effective way for terrorist groups to plan operations, recruit followers, raise funds and distribute propaganda -- centralization of forces and services is exactly what a terrorist organization isn't into. Diversification and autonomous management for the sake of improving the continuity of the site in operation is what really matter, namely you'll have the propaganda platform spreading online details on how to donate cash on a site that's been set up for this purpose only. By the time there's been a leak in the "good guys"
covert competitive intelligence efforts, the donation site will dissapear and reappear somewhere else, while the central propaganda platform remains fully active. Take the other perspective, if the "bad guys" are aware the "good guys" are reading, they may logically leave a decoy to later on analyze how it's being processed and disinform on what may seem a very decent first-hand information gathered through open source intelligence.
- Their mastery of the web could extend to cyber-terrorism, such as disabling the communication systems that underpin key sectors such as banking and energy -- any government's single biggest mistake is
stereotyping about cyberterrorism, namely that it's the
offensive use of cyberterrorism to worry about, whereas the defensive, or passive concepts are already maturing.
- Western agencies are almost powerless to stop the jihadists' internet activities -- of course they aren't, and stopping compared to monitoring is totally wrong, the enemy's location you know is better than the enemy's location you don't know.
- Western governments have been very slow to respond and are only now turning their attention to combating the potent "story" promulgated over the internet -- they wouldn't be that very slow in responding if they actually knew how many people read and got brainwashed by it, thus what conversion rate can we talk about from a reader, to collaborator, to wannabe terrorist, come up with metrics and raise eyebrows.
 Well, well, well. What do we got here? Couple of interesting domains hosting phishing sites of multiple banks for you to take a look at, or at the cached versions to be precise. What's worth mentioning is the rise of phishing sites using the much more easily and anonymously registered .biz ; .info ; .name domains. However, the first part of these is related to 211.137.13.131 :
Well, well, well. What do we got here? Couple of interesting domains hosting phishing sites of multiple banks for you to take a look at, or at the cached versions to be precise. What's worth mentioning is the rise of phishing sites using the much more easily and anonymously registered .biz ; .info ; .name domains. However, the first part of these is related to 211.137.13.131 :
























 Mother Nature
Mother Nature
 Outstanding project
Outstanding project
 Interactive slideshow
Interactive slideshow


 Informative
Informative
 Last week, the Internet Haganah
Last week, the Internet Haganah