The Lizamoon mass SQL injection attacks gang is continuing to efficiently inject malicious code on hundreds of thousands of legitimate sites, for the purpose of serving fake security software -- also known as scareware -- and client-side exploits.
The latest round of the campaign is serving client-side exploits through multiple redirections taking place once the end user loads the malicious script embedded on legitimate sites. In comparison, in the past the gang used to monetize the hijacked traffic by serving scareware and bogus Adobe Flash Players.
What are some of the currently SQL injected malicious domains? How does the redirection take place? Did they take into consideration basic QA (quality assurance) tactics into place? Let's find out.
Currrently injected malicious domains are parked at 31.210.100.242 (AS42926, RADORE Hosting), with the following domains currently responding to that IP:
skdjui.com/r.php - Email: jamesnorthone@hotmailbox.com
njukol.com/r.php - Email: jamesnorthone@hotmailbox.com
hnjhkm.com/r.php - Email: jamesnorthone@hotmailbox.com
nikjju.com/r.php - Email: jamesnorthone@hotmailbox.com
hgbyju.com/r.php - Email: jamesnorthone@hotmailbox.com
uhjiku.com/r.php - Email: jamesnorthone@hotmailbox.com
uhijku.com/r.php - Email: jamesnorthone@hotmailbox.com
werlontally.net/r.php - Email: jamesnorthone@hotmailbox.com
March's round of malicious domains was hosted at 91.226.78.148 (AS56697, LISIK-AS OOO “Byuro Remontov “FAST”).
The redirection takes us to these two domains: www3.topcumaster.com - 75.102.21.120 (AS23352, SERVERCENTRAL)
Parked at 75.102.21.120 are also the following domains:
www3.personal-scanera.com - Email: benji.rubes@yahoo.com
www3.personalvoguard.com - Email: benji.rubes@yahoo.com
www3.hard-zdsentinel.com - Email: benji.rubes@yahoo.com
www3.bestbxcleaner.com - Email: benji.rubes@yahoo.com
www3.topcumaster.com - Email: benji.rubes@yahoo.com
www3.safe-defensefu.com - Email: benji.rubes@yahoo.com
and www1.safe-wnmaster.it.cx - 217.23.8.123 (AS49981, WorldStream)
Parked on 217.23.8.123 are also the following client-side exploits serving domains part of the Lizamoon mass SQL injection attacks:
www1.thebestscannerdc.it.cx/i.html
www1.safebh-defense.it.cx/i.html
www1.strongdkdefense.it.cx/i.html
www2.best-czsuite.it.cx/i.html
www1.smartmasterf.it.cx/i.html
www1.simplescanerei.it.cx/i.html
www1.bestic-network.it.cx/i.html
www1.topqonetwork.it.cx/i.html
www2.topasnetwork.it.cx/i.html
www1.powerynetwork.it.cx/i.html
www1.simplemasterzk.it.cx/i.html
www1.powerneholder.it.cx/i.html
www1.personalkochecker.it.cx/i.html
www1.smarthdschecker.it.cx/i.html
www1.safebacleaner.it.cx/i.html
www1.strongzkcleaner.it.cx/i.html
www1.topumcleaner.it.cx/i.html
www1.topgdscanner.it.cx/i.html
www1.smartwoscanner.it.cx/i.html
www1.safe-wnmaster.it.cx/i.html
www1.powervmaster.it.cx/i.html
www1.top-armyvs.it.cx/i.html
www2.saveocsoft.it.cx/i.html
www1.top-zjsoft.it.cx/i.html
www1.powerdefensekt.it.cx/i.html
www1.best-scanersw.it.cx/i.html
www1.powermb-security.it.cx/i.html
www1.strongxd-security.it.cx/i.html
www1.strongbtsecurity.it.cx/i.html
Client side exploits, CVE-2010-0188 and CVE-2012-0507 in particular are served through the i.html file located on these hosts. In order for the client-side exploitation process to take place, the redirection chain must be correct, if not the server will return a "404 Error Message" when requesting a specific file part of the campaign. There are no HTTP referrer checks in place, at least for the time being. What's particularly interesting about the current campaign, is that during a period of time, it will on purposely serve a "404 Error Message" no matter what happens.
Updates will be posted, as soon as new developments emerge.
Related posts:
SQL Injection Through Search Engines Reconnaissance
Massive SQL Injections Through Search Engine's Reconnaissance - Part Two
Massive SQL Injection Attacks - the Chinese Way
Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
Dissecting the WordPress Blogs Compromise at Network Solutions
Yet Another Massive SQL Injection Spotted in the Wild
Smells Like a Copycat SQL Injection In the Wild
Fast-Fluxing SQL Injection Attacks
Obfuscating Fast-fluxed SQL Injected Domains
In the overwhelming sea of information, access to timely, insightful and independent open-source intelligence (OSINT) analyses is crucial for maintaining the necessary situational awareness to stay on the top of emerging security threats. This blog covers trends and fads, tactics and strategies, intersecting with third-party research, speculations and real-time CYBERINT assessments, all packed with sarcastic attitude
Showing posts with label SQL Injection. Show all posts
Showing posts with label SQL Injection. Show all posts
Tuesday, May 08, 2012
Dissecting the Ongoing Client-Side Exploits Serving Lizamoon Mass SQL Injection Attacks
Tags:
Botnet,
Client-Side Exploits,
Client-Side Vulnerabilities,
Exploits,
Fake Security Software,
Hacking,
Information Security,
Lizamoon,
Scareware,
Security,
SQL Injection,
Vulnerabilities
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Thursday, October 20, 2011
Dissecting the Ongoing Mass SQL Injection Attack
The ongoing mass SQL injection attack, has already affected over a million web sites. Cybercriminals performing active search engines reconnaissance have managed to inject a malicious script into ASP ASP.NET websites.
From client-side exploits to bogus Adobe Flash players, the campaign is active and ongoing. In this intelligence brief, we'll dissect the campaign and establish a direct connection between the campaign and last March's Lizamoon mass SQL injection attack.
SQL injected domains -- thanks to Dasient's Tufan Demir for the ping:
nbnjki.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
jjghui.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookzula.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookgusa.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
dfrgcc.com/ur.php - Email: jamesnorthone@hotmailbox.com
statsl.com/ur.php - 111.22.111.111 - Email: jamesnorthone@hotmailbox.com
milapop.com/ur.php - Email: jamesnorthone@hotmailbox.com
jhgukn.com/ur.php - Email: jamesnorthone@hotmailbox.com
vovmml.com/ur.php - Email: jamesnorthone@hotmailbox.com
bookvivi.com/ur.php - Email: jamesnorthone@hotmailbox.com
Responding to 146.185.248.3 is also file-dl.com; bookfula.com and bookvila.com - Email: jamesnorthone@hotmailbox.com
Detection rate for urchin.js:
urchin.js - Trojan.JS.Redirector - 17/42 (40.5%)
MD5 : 4387f9be5af4087d21c4b44b969a870f
SHA1 : 8a47842ccf6d642043ee8db99d0530336eef6b99
SHA256: 975e62fe1d9415b9fa06e8f826f776ef851bd030c2c897bc3fbee207519f8351
The redirections take place as follows:
- bookzula.com/ur.php -> www3.topasarmy.in/?w4q593n= - Email: bill.swinson@yahoo.com -> firstrtscaner.rr.nu
- nbnjkl.com/urchin.js -> power-wfchecker.in/?1dlia916= - Email: bill.swinson@yahoo.com
uberble-safe.in
uberate-safe.in
best-jsentinel.in
topantivir-foru.in
personalscannerlg.in
rideusfor.in
hardbsy-network.in
enablesecureum.in
hardynauchecker.in
best-jsentinel.in
smartklhdefense.in
smartaasecurity.in
personal-scan-4u.in
unieve-safe.in
safe-solutionsoft.in
hugeble-cure.in
topsecuritykauu.in
personalcleansoft.in
powerscanercis.in
topksfsecurity.in
hard-antivirbjb.in
strong-guardbxz.in
smart-suiteguard.in
thebestkrearmy.in
smart-guardianro.in
freeopenscanerpo.in
best-networkqjo.in
hard-antivirbjb.in
smartantivir-scanner.in
most-popularsoftcontent.in
bester-msecuriity.in
doneahme.in
strong-checkerwrt.in
safepowerforu.in
safe-securityarmy.in
personal-bpsentinel.in
personalcleansoft.in
ostestsystemri.in
saveinternet-guard.in
just-perfectprotection.in
firstholdermvq.in
just-perfectprotection.in
allcle-safe.in
brawaidme.in
uniind-safe.in
moreaz-fine.in
trueeox-safe.in
safexanet.in
personal-internet-foryou.in
For the time being, the campaing is redirecting to a fake YouTube page enticing users into downloading a bogus Adobe Flash player in order to view the video.
Detection rate for the bogus Adobe Flash player:
scandisk.exe - Backdoor:Win32/Simda.A - 8/43 (18.6%)
MD5 : fb4c93935346d2d8605598535528506e
SHA1 : 0ff7ccd785c0582e33c22f9b21156929ba7abaeb
SHA256: b204586cbac1606637361dd788b691f342cb1c582d10690209a989b040dab632
Upon execution the sample phones back to:
209.212.147.141/chrome/report.html
98.142.243.64/chrome/report.html
update.19runs10q3.com - 65.98.83.115
The same phone back locations have been used in a variety of related malware -- thanks to Kaspersky's David Jacoby for the ping. For instance, in this malware sample that's also phoning back to the same URLs, we have active HOSTS file modification as follows:
See related post: Sampling Malicious Activity Inside Cybercrime-Friendly Search Engines
www.google.com.=87.125.87.99;
google.com.=87.125.87.103;
google.com.au.=87.125.87.104;
www.google.com.au.=87.125.87.147;
google.be.=77.125.87.148;
www.google.be.=77.125.87.149;
google.com.br.=77.125.87.109;
www.google.com.br.=77.125.87.150;
google.ca.=77.125.87.152;
www.google.ca.=77.125.87.153;
google.ch.=77.125.87.155;
www.google.ch.=77.125.87.158;
google.de.=77.125.87.160;
www.google.de.=77.125.87.161;
google.dk.=92.125.87.123;
www.google.dk.=92.125.87.160;
google.fr.=92.125.87.154;
www.google.fr.=92.125.87.134;
google.ie.=92.125.87.170;
www.google.ie.=92.125.87.177;
google.it.=92.125.87.173;
www.google.it.=92.125.87.147;
google.co.jp.=92.125.87.103;
www.google.co.jp.=84.125.87.147;
google.nl.=84.125.87.103;
www.google.nl.=84.125.87.147;
google.no.=84.125.87.103;
www.google.no.=84.125.87.147;
google.co.nz.=84.125.87.103;
www.google.co.nz.=84.125.87.147;
google.pl.=84.125.87.103;
www.google.pl.=64.125.87.147;
google.se.=64.125.87.103;
www.google.se.=64.125.87.147;
google.co.uk.=64.125.87.103;
www.google.co.uk.=64.125.87.147;
google.co.za.=64.125.87.103;
www.google.co.za.=64.125.87.147;
www.google-analytics.com.=64.125.87.101;
www.bing.com.=92.123.68.97;
search.yahoo.com.=72.30.186.249;
www.search.yahoo.com.=72.30.186.249;
uk.search.yahoo.com.=87.248.112.8;
ca.search.yahoo.com.=100.6.239.84;
de.search.yahoo.com.=87.248.112.8;
fr.search.yahoo.com.=87.248.112.8;
au.search.yahoo.com.=87.248.112.8;
ad-emea.doubleclick.net.=64.125.87.101;
www.statcounter.com.=64.125.87.101;
The Lizamoon mass SQL injection connection
The same email used to register the SQL injected domains jamesnorthone@hotmailbox.com has been used to register the Lizamoon mass SQL injection attack domains extensively profiled here - "Dissecting the Massive SQL Injection Attack Serving Scareware".
Related posts:
- SQL Injection Through Search Engines Reconnaissance
- Massive SQL Injections Through Search Engine's Reconnaissance - Part Two
- Massive SQL Injection Attacks - the Chinese Way
- Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
- GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
- Dissecting the WordPress Blogs Compromise at Network Solutions
- Yet Another Massive SQL Injection Spotted in the Wild
- Smells Like a Copycat SQL Injection In the Wild
- Fast-Fluxing SQL Injection Attacks
- Obfuscating Fast-fluxed SQL Injected Domains
Tags:
Blackhat SEO,
Botnet,
Fake Adobe Flash Player,
Fake Security Software,
Hacking,
Information Security,
Lizamoon,
Malicious Software,
Scareware,
Search Engine Optimization,
Security,
SQL Injection
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Thursday, March 31, 2011
Dissecting the Massive SQL Injection Attack Serving Scareware
A currently ongoing massive SQL injection attack has affected hundreds of thousands of web pages across the Web, to ultimately monetize the campaign through a scareware affiliate program. Such massive SQL injection attempts are usually conducted using mass vulnerability scanning tools, with the help of search engines which have already crawled the vulnerable sites.
What's particularly interesting about this campaign, is the fact that the used domains are all responding to the same IPs, including the portfolios of scareware domains, which the cybercriminals naturally rotate on a periodic basis. Let's dissect the campaign, expose the domain portfolios and the entire campaign structure.
UPDATED: Related SQL injected URLs courtsesy of WebSense:
online-stats201.info/ur.php - Email: tik0066@gmail.com
stats-master111.info/ur.php - Email: tik0066@gmail.com
agasi-story.info/ur.php - 91.217.162.45 - Email: tik0066@gmail.com
general-st.info/ur.php - Email: tik0066@gmail.com
extra-service.info/ur.php - Email: tik0066@gmail.com
sol-stats.info/ur.php - Email: tik0066@gmail.com
google-stats49.info/ur.php - Email: tik0066@gmail.com
google-stats45.info/ur.php - Email: tik0066@gmail.com
google-stats50.info/ur.php - Email: tik0066@gmail.com
google-server43.info/ur.php - Email: tik0066@gmail.com
stats-master88.info/ur.php - Email: tik0066@gmail.com
eva-marine.info/ur.php - 109.236.81.28 - Email: tik0066@gmail.com
stats-master99.info/ur.php - Email: tik0066@gmail.com
tzv-stats.info/ur.php - Email: tik0066@gmail.com
milapop.com/ur.php - Email: jamesnorthone@hotmailbox.com
SQL injected URLs:
lizamoon.com/ur.php (67,500 results) - 91.220.35.151 (AS3721); 91.213.29.182 (AS51786); 95.64.9.18 (AS50244) - Email: jamesnorthone@hotmailbox.com
alexblane.com/ur.php (3,920 results) - Email: jamesnorthone@hotmailbox.com
alisa-carter.com/ur.php (220,000 results) - Email: jamesnorthone@hotmailbox.com
alexblane.com/ur.php (3,920 results) - Email: jamesnorthone@hotmailbox.com
t6ryt56.info/ur.php (18 results) - Email: support@ruler-domains.com
tadygus.com/ur.php (100 results) - Email: jamesnorthone@hotmailbox.com
worid-of-books.com/ur.php (334,000 results) - Email: tik0066@gmail.com
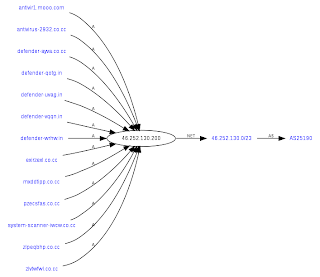
Upon successful redirection, the campaign attempts to load the scareware domains defender-nibea.in/scan1b/237 - 46.252.130.200 - Email: jimwei2969@gmail.com
Detection rate:
freesystemscan.exe - Trojan/Win32.FakeAV - Result: 9/ 41 (22.0%)
MD5 : 815d77f8fca509dde1abeafabed30b65
SHA1 : 1b3c35afb76c53cd9507fffee46fb58c29e72bc1
SHA256: cd902b92042435c2d70d4bf59acc2de8229bfc367626961f76c03f75dcd7e95c
antivirus-1091.co.cc
antivirus-1574.co.cc
antivirus-2051.co.cc
antivirus-2525.co.cc
antivirus-2932.co.cc
antivirus-3654.co.cc
antivirus-3833.co.cc
antivirus-4063.co.cc
antivirus-418.co.cc
antivirus-4303.co.cc
antivirus-4749.co.cc
antivirus-495.co.cc
antivirus-5216.co.cc
antivirus-5676.co.cc
antivirus-5802.co.cc
antivirus-6437.co.cc
antivirus-6703.co.cc
antivirus-7081.co.cc
antivirus-713.co.cc
antivirus-728.co.cc
antivirus-7357.co.cc
antivirus-8072.co.cc
antivirus-9009.co.cc
antivirus-9638.co.cc
antivirus-9667.co.cc
defender-aabv.in - Email: leonflanagan7681@gmail.com
defender-aqeu.co.cc
defender-asng.co.cc
defender-atio.in - Email: terriduverger3239@gmail.com
defender-atxo.in - Email: celineiebba9266@gmail.com
defender-bcvs.in - Email: martinefinklea5375@gmail.com
defender-bwuy.co.cc
defender-cron.in - Email: lisasuresh9147@gmail.com
defender-ddbr.in - Email: selenajohansson9195@gmail.com
defender-dteo.in - Email: giovannaraggio5417@gmail.com
defender-eahy.co.cc
defender-eklq.in - Email: sebastiensheppard8680@gmail.com
defender-endl.in - Email: adamgaylard1113@gmail.com
defender-ewum.co.cc
defender-eyde.co.cc
defender-fmof.in - Email: kamillamartin1237@gmail.com
defender-fola.co.cc
defender-gnva.in - Email: ananddaher7294@gmail.com
defender-grlt.in - Email: anthonygaylard9887@gmail.com
defender-hipw.in - Email: angiejohansen9730@gmail.com
defender-hjlk.in - Email: jennwrayford2124@gmail.com
defender-hmfu.in - Email: lynnbone8026@gmail.com
defender-hsug.in - Email: moniquetkarnopp3596@gmail.com
defender-htlu.in - Email: jerihamann4163@gmail.com
defender-iibk.co.cc
defender-iies.co.cc
defender-iksl.in - Email: amarasanders9974@gmail.com
defender-isde.co.cc
defender-iyrc.co.cc
defender-jgnl.in - Email: caseyalzen3316@gmail.com
defender-jihv.co.cc
defender-keod.in - Email: khashayarbirss4814@gmail.com
defender-kuts.in - Email: rogerfrancis3322@gmail.com
defender-kwwh.in - Email: tobyboisseau6505@gmail.com
defender-kzwu.co.cc
defender-labm.in - Email: gregorybradford1520@gmail.com
defender-lcoh.in - Email: timothythomas6924@gmail.com
defender-nhei.co.cc
defender-nrpr.in - Email: burtonalba8156@gmail.com
defender-ojbr.in - Email: fucknielsen8675@gmail.com
defender-osbi.in - Email: fidelslattum2159@gmail.com
defender-pakc.in - Email: sabrinawheelock7642@gmail.com
defender-ppdw.in - Email: divinakempton5670@gmail.com
defender-qfdx.in - Email: hokyeongyancey6369@gmail.com
defender-qotg.in - Email: franchescaili9704@gmail.com
defender-qpwo.in - Email: carlaadams@gmail.com
defender-qsko.co.cc
defender-qumf.in - Email: carlaadams@gmail.com
defender-rlag.in - Email: carmichaelmail@gmail.com
defender-rrin.in - Email: kevincharoenset5321@gmail.com
defender-thga.in - Email: youngantonio6055@gmail.com
defender-ueuv.co.cc
defender-uqko.in - Email: christinakaaikati5574@gmail.com
defender-vflq.in - Email: terriacuna2081@gmail.com
defender-vlmj.in - Email: lauriefreeman9930@gmail.com
defender-vqqn.in - Email: chrisjames4421@gmail.com
defender-vxgh.in - Email: griseldavelez5369@gmail.com
defender-wkiw.in - Email: otisvaladez7778@gmail.com
defender-wqga.in - Email: christodoulosglidden8856@gmail.com
defender-wrhw.in - Email: bradsuresh1406@gmail.com
defender-wtln.co.cc
defender-xcre.in - Email: pavelmayer4891@gmail.com
defender-xnnx.in - Email: pavelmayer4891@gmail.com
defender-ykym.co.cc
movie-iirg.in - Email: misslynn8546@gmail.com
movie-pblv.in - Email: judgewright4021@gmail.com
movies-live-tube-jeyq.co.cc
movie-tkhk.in - Email: terrymeally1288@gmail.com
movie-tube-beym.co.cc
movie-tube-juie.co.cc
movie-ueep.in - Email: celinekevin6179@gmail.com
movieway2011.com - Email: contact@privacyprotect.org
movie-xbtb.in - Email: sanfordross9242@gmail.com
movie-xxnl.in - Email: ianbalitsaris3201@gmail.com
softway2011.com - Email: contact@privacyprotect.org
system-scanner-boep.co.cc
system-scanner-eill.co.cc
system-scanner-eopa.co.cc
system-scanner-ewqq.co.cc
system-scanner-iaap.co.cc
system-scanner-ieyx.co.cc
system-scanner-lcyo.co.cc
system-scanner-ouny.co.cc
system-scanner-oypx.co.cc
system-scanner-qeap.co.cc
system-scanner-racv.co.cc
system-scanner-ryes.co.cc
system-scanner-tzii.co.cc
system-scanner-uemo.co.cc
system-scanner-uotu.co.cc
system-scanner-uyxt.co.cc
system-scanner-vpoo.co.cc
system-scanner-xtoi.co.cc
system-scanner-yoyx.co.cc
system-scanner-ytut.co.cc
Rotated scareware domains involved in the campaign, responding to 84.123.115.228 (AS6739; ONO-AS Cableuropa - ONO):
defender-thga.in - Email: youngantonio6055@gmail.com
defender-wqga.in - Email: christodoulosglidden8856@gmail.com
defender-gnva.in - Email: ananddaher7294@gmail.com
defender-rlob.in - Email: vasikaranfreudenburg2690@gmail.com
defender-abcc.in - Email: rubysmart5057@gmail.com
defender-pakc.in - Email: sabrinawheelock7642@gmail.com
defender-keod.in - Email: khashayarbirss4814@gmail.com
defender-xcre.in - Email: pavelmayer4891@gmail.com
defender-qumf.in - Email: rachelalba1891@gmail.com
defender-fmof.in - Email: kamillamartin1237@gmail.com
defender-uvag.in - Email: espenkeck7682@gmail.com
defender-hsug.in - Email: moniquetkarnopp3596@gmail.com
defender-vxgh.in - Email: griseldavelez5369@gmail.com
defender-lcoh.in - Email: timothythomas6924@gmail.com
defender-kwwh.in - Email: tobyboisseau6505@gmail.com
defender-osbi.in - Email: fidelslattum2159@gmail.com
defender-wbui.in - Email: carlosbuntschu1238@gmail.com
defender-vlmj.in - Email: lauriefreeman9930@gmail.com
defender-hjlk.in - Email: lauriefreeman9930@gmail.com
defender-endl.in - Email: adamgaylard1113@gmail.com
defender-jgnl.in - Email: caseyalzen3316@gmail.com
defender-iksl.in - Email: marasanders9974@gmail.com
defender-labm.in - Email: gregorybradford1520@gmail.com
defender-rrin.in - Email: kevincharoenset5321@gmail.com
defender-sxin.in - Email: taloupavlinovich7166@gmail.com
defender-cron.in - Email: lisasuresh9147@gmail.com
defender-vqqn.in - Email: chrisjames4421@gmail.com
defender-dteo.in - Email: giovannaraggio5417@gmail.com
defender-uqko.in - Email: christinakaaikati5574@gmail.com
defender-qpwo.in - Email: carlaadams@gmail.com
defender-atxo.in - Email: celineiebba9266@gmail.com
defender-rlfp.in - Email: latanyamuscatell9507@gmail.com
defender-vflq.in - Email: terriacuna2081@gmail.com
defender-eklq.in - Email: sebastiensheppard8680@gmail.com
defender-ddbr.in - Email: selenajohansson9195@gmail.com
defender-ojbr.in - Email: fucknielsen8675@gmail.com
defender-drnr.in - Email: sumanvcasquez2008@gmail.com
defender-nrpr.in - Email: burtonalba8156@gmail.com
defender-kuts.in - Email: rogerfrancis3322@gmail.com
defender-bcvs.in - Email: martinefinklea5375@gmail.com
defender-grlt.in - Email: anthonygaylard9887@gmail.com
defender-hmfu.in - Email: lynnbone8026@gmail.com
defender-htlu.in - Email: jerihamann4163@gmail.com
defender-aabv.in - Email: leonflanagan7681@gmail.com
defender-ppdw.in - Email: divinakempton5670@gmail.com
defender-wrhw.in - Email: bradsuresh1406@gmail.com
defender-wkiw.in - Email: otisvaladez7778@gmail.com
defender-hipw.in - Email: angiejohansen9730@gmail.com
defender-qfdx.in - Email: hokyeongyancey6369@gmail.com
defender-xnnx.in - Email: sylviawulff2140@gmail.com
defender-xkox.in - Email: ryanmartin7607@gmail.com
The scareware domains have been registered using automatically registered email accounts at Gmail, as a precaution in an attempt to make it harder to expose the campaign by using a single email only.
Monitoring of the campaign is ongoing.
Related posts:
- SQL Injection Through Search Engines Reconnaissance
- Massive SQL Injections Through Search Engine's Reconnaissance - Part Two
- Massive SQL Injection Attacks - the Chinese Way
- Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
- GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
- Dissecting the WordPress Blogs Compromise at Network Solutions
- Yet Another Massive SQL Injection Spotted in the Wild
- Smells Like a Copycat SQL Injection In the Wild
- Fast-Fluxing SQL Injection Attacks
- Obfuscating Fast-fluxed SQL Injected Domains
Tags:
Blackhat SEO,
Cybercrime,
Fake Security Software,
Hacking,
Information Security,
Scareware,
Search Engine Optimization,
Security,
SQL Injection
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Subscribe to:
Comments (Atom)