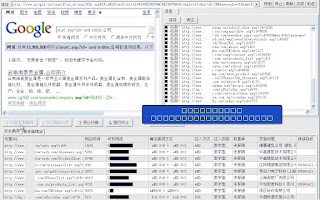
The surprising part? The primary and entire portfolio of these traffic redirection and traffic management domain are parked on 193.106.175.18 - AS50465 - IQHost Ltd where one of the bigger domain farms is parked at hxxp://biggerfun.org.
Independent Contractor. Bitcoin: 15Zvie1j8CjSR52doVSZSjctCDSx3pDjKZ Email: dancho.danchev@hush.com OMEMO: ddanchev@conversations.im | OTR: danchodanchev@xmpp.jp | TOX ID: 2E6FCA35A18AA76B2CCE33B55404A796F077CADA56F38922A1988AA381AE617A15D3D3E3E6F1
Thursday, December 28, 2023
Who's Pushing All The "Fake Updates" Malicious Software Using Redirectors and Traffic Distribution and Redirection Systems and Tools Domains?
The surprising part? The primary and entire portfolio of these traffic redirection and traffic management domain are parked on 193.106.175.18 - AS50465 - IQHost Ltd where one of the bigger domain farms is parked at hxxp://biggerfun.org.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, December 15, 2023
Looking for a Research Sponsorship
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Offering my Laptop for Memorabilia Purposes
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Upcoming Webinar Participation
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
The Most Innovative Cyber Security Leader to Watch in 2023
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Saturday, December 02, 2023
The Conti Ransomware Gang's OSINT Artifacts
hxxp://cc2-btc.cc
hxxp://dyncheck.com
hxxp://luxchecker.pw
hxxp://major.ms
hxxp://securecall.club
hxxp://securecall.top
hxxp://checkzilla.io
Including the following two XMPP/Jabber accounts:
mcduckgroup@exploit.im
uvoice@xmpp.jp
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Typosquatted GMail Malware Domains
Sample domains include:
hxxp://account-disk-gmail[.]com
hxxp://account-mail-my-gmail[.]com
hxxp://account-my-mail-gmail[.]com
hxxp://account-oauth-gmail[.]com
hxxp://accounts-mail-goglemail[.]com
hxxp://accounts-mail-my-gmail[.]com
hxxp://accounts-my-mail-gmail[.]com
hxxp://accounts-oauth-gmail[.]com
hxxp://cloud-accounts-goglemail[.]com
hxxp://cloud-myaccount-goglemail[.]com
hxxp://mail-accounts-my-gmail[.]com
hxxp://mail-my-account-gmail[.]com
hxxp://mail-my-accounts-gmail[.]com
hxxp://mail-myaccount-yahoo[.]com
hxxp://mail-myaccount[.]com
hxxp://mail-myaccounts-gmail[.]com
hxxp://mail-yahoo-my-account[.]com
hxxp://mail-yahoo-myaccount[.]com
hxxp://mail-yahoo-myaccounts[.]com
hxxp://my-account-security-goglemail[.]com
hxxp://my-mail-account-gmail[.]com
hxxp://my-mail-account-yahoo[.]com
hxxp://my-mail-accounts-gmail[.]com
hxxp://my-mail-gmail[.]com
hxxp://my-mail-yahoo-accounts[.]com
hxxp://my-oauth-account-gmail[.]com
hxxp://my-security-goglemail[.]com
hxxp://my-signin-account-gmail[.]com
hxxp://my-signin-accounts-gmail[.]com
hxxp://myaccount-mail-goglemail[.]com
hxxp://myaccount-mail-my-gmail[.]com
hxxp://myaccount-my-mail-gmail[.]com
hxxp://myaccounts-gmail[.]com
hxxp://myaccounts-mail-gmail[.]com
hxxp://myaccounts-mail-my-gmail[.]com
hxxp://myaccounts-mail-yahoo[.]com
hxxp://myaccounts-my-mail-gmail[.]com
hxxp://mysecurity-goglemail[.]com
hxxp://security-accounts-goglemail[.]com
hxxp://security-my-account-goglemail[.]com
hxxp://security-my-accounts-goglemail[.]com
hxxp://security-my-goglemail[.]com
hxxp://security-myaccount-goglemail[.]com
hxxp://security-myaccounts-goglemail[.]com
hxxp://yahoo-oauth-accounts[.]com
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Emennet Pasargad
Sample domains:
eeleyanet.com
eeleyanet.ir
Sample personally identifiable email address accounts:
sidafin@mihanmail.ir
amirhaghighi2014@yahoo.com
safary.mansoor@gmail.com
Rahimi@Live.com
faranakbehjati@yahoo.com
h.boloukat@gmail.com
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, December 01, 2023
Cybercrime-Friendly Forum Communities - Part Two
Cybercrime-friendly forum communities include:
hxxp://crdforum.cc/
hxxp://darkwebmafias.net/
hxxp://darkstash.com/
hxxp://crdpro.cc/
hxxp://www.cardingclub.net/
hxxp://www.russiancarders.se/
hxxp://validmarket.io/
hxxp://cardingforum.cx/
hxxp://carding.sh/
hxxp://bitcarder.com
hxxp://cardingleaks.ws/
hxxp://www.verifiedcarder.net/
hxxp://www.legitcarder.ru/
hxxp://www.crdworld.com/
hxxp://cardingmafia.to/
hxxp://cardingforum.cx
hxxp://crdforum.cc
hxxp://darkstash.com
hxxp://carders.biz
hxxp://crdpro.cc
hxxp://carders.mx
hxxp://carding-forum.com
hxxp://crdclub.su
hxxp://procrd.pw
hxxp://cardmafia.cc
hxxp://cardingforum.info
hxxp://cardingleaks.ws
hxxp://darkpro.net
hxxp://crackingforum.to
hxxp://cardingworld.ru
hxxp://darkwebmafias.ws
hxxp://leetforums.ru
hxxp://legitcarders.ws
hxxp://crdcrew.cc
hxxp://prtship.pro
hxxp://verifiedcarder.net
hxxp://legitcarder.ru
hxxp://carders.zone
hxxp://drdark.ru
hxxp://darknetweb.ru
hxxp://bpcforum.ru
hxxp://wc-club.com
hxxp://cybercarders.com
hxxp://bitorder.pw
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Rewards for Justice - Dancho Danchev
hxxp://school-global.ru
hxxp://youladance.ru
Телефон: +373 775 96666
E-mail: info@morene[.]host
Skype: morene[.]host
Jabber: morene@jabber[.]morene[.]host
ICQ: 700812649 / 702647156
Telegram: @hostmorene
Viber: +373 775 96666
WhatsApp: +373 775 96666
Онлайн-чат: https://morene[.]host
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Full Names of Ashiyane Digital Security Team Members
The following are the full names of Ashiyane Digital Security Team Members:
Keyvan Sedaghati — keivan
Ramin Baz Ghandi — fr0nk
Erfan Zadpoor — PrinceofHacking
Hamid Norouzi — eychenz
Poorya Mohammadrezaei — Hijacker
Omid Norouzi — Sha2ow
Milad Bokharaei — ®Maste
Vahid Maani — WAHID 2
Kaveh Jasri — root3r
Ali Hayati — Zend
Milad Mazaheri — mmilad200
Mohammad Reza — iNJECTOR
Mohammad Mohammadi — Classic
Nima Salehi — Q7X
Milad Jafari — Milad-Bushehr
Shahin Salak Tootonchi — ruiner_blackhat
Amin Bandali — anti206
Mohammad Hadi Nasiri — unique2world
Mahdi Chinichi — Virangar
Amir Hossein Tahmasebi — __amir__
Ashkan Hosseini — Askn
Mohammad Tajik — taghva
Meghdad Mohammadi — M3QD4D
Sina Ahmadi Neshat — Encoder
Behrouz Kamalian — Behrouz_ice)
Farshid Sargheini — Azazel
Armin — n3me3iz
Mahdi K. — r3d.z0nE
Iman Honarvar — iman_taktaz
Ali Seid Nejad — Ali_Eagle
Mohammad Reza Ali Babaei — mzhacker
Navid Naghdi — elvator
Mohammad Reza Dolati — HIDDEN-HUNTER
Mehrab Akherati — AliAkh
Amin Javid — Gladiator
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Cybercrime-Friendly Forum Communities
Sample cybercrime-friendly forum communities include:
hxxp://www.darkteam.se/
hxxp://crdforum.cc/
hxxp://legitcarders.ws/
hxxp://cardingworld.ru
hxxp://carders.biz/
hxxp://carding.cm/
hxxp://cardmafia.cc/
hxxp://cardingforum.cx/
hxxp://carder.market/
hxxp://www.russiancarders.se/
hxxp://darkwebmafias.net/
hxxp://legendzforum.com/
hxxp://procrax.cx/
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Iran's Afkar System Yazd Co Ransomware
Sample domains known to have been involved in the campaign include:
hxxp://newdesk.top
hxxp://onedriver-srv.ml
hxxp://symantecserver.co
hxxp://microsoft-updateserver.cf
hxxp://msupdate.us
hxxp://service-management.tk
hxxp://aptmirror.eu
hxxp://winstore.us
hxxp://my-logford.ml
hxxp://gupdate.us
hxxp://tcp443.org
Sample email address accounts known to have been involved in the campaign include:
amirbitminer[.]gmail.com
thund3rz[.]protonmail.com
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Email Address Accounts Known To Belong To Owners of E-Shops for Stolen Credit Card Details - Part Two
Sample email address accounts include:
admin@accessltd[.]ru
rubensamvelich@gmail[.]com
rubensamvelich@yahoo[.]com
bulbacc@rocketmail[.]com
bulbacc@yahoo[.]com
ooo.service@yahoo[.]com
dumps.cc@safe-mail[.]net
b2b.maxim@gmail[.]com
lvjiecong@yahoo[.]com[.]cn
roger.sroy@yahoo[.]com
elche011@yahoo[.]com
keikomiyahara@yahoo[.]com
dcb725@gmail[.]com
wattt80@yahoo[.]com
yurtan20@e1[.]ru
vipforexbiz@gmail[.]com
kachanaburi@yahoo[.]com
persiks@online[.]ua
alexandanns@gmail[.]com
bestdumpssu@live[.]com
admin@mycc[.]su
admin@bestdumps[.]biz
tonchang2011@yahoo[.]com
ccstoreru@yahoo[.]com
bdsupport@jabber[.]org
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Email Address Accounts Known To Belong To Owners of E-Shops for Stolen Credit Card Details
Sample domains involved include:
ccmall.cc
track2.name
trackstore.su
magic-numbers.cc
allfresh.us
freshstock.biz
bulba.cc
approven.su
cv2shop.com
vzone.tc
ccStore.ru
dumps.cc
privateservices.ws
perfect-numbers.cc
mega4u.biz
accessltd.ru
pwnshop.cc
bestdumps.su
mycc.su
bestdumps.biz
dumpshop.bz
cardshop.bz
dumpscheck.com
Sample email address accounts involved include:
roger.sroy@yahoo[.]com
keikomiyahara@yahoo[.]com
bulbacc@yahoo[.]com
yurtan20@e1[.]ru
ccstoreru@yahoo[.]com
persiks@online[.]ua
admin@accessltd[.]ru
bestdumpssu@live[.]com
admin@mycc[.]su
admin@bestdumps[.]biz
bdsupport@jabber[.]org
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Monday, November 27, 2023
Dancho Danchev’s Videos
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, November 24, 2023
Compromised CPanel Offered for Sale
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Image Spam Generating Tool
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Crowdsourced Iran DDoS Attack Campaign

 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Rogue Google AdSense Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
SQL Injection Attack Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Managed Spam Service
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
EyeWonder iFrame Injection Attack Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Web Malware Exploitation Kit
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
SQL Injection Attack Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Blackhat SEO Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
SQL Injection Attack Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Chimera Botnet
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Innovative Marketing Scareware Distributor
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
China vs Iran Hacktivism Campaign
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
















.png)




.jpg)