Stay tuned!
In the overwhelming sea of information, access to timely, insightful and independent open-source intelligence (OSINT) analyses is crucial for maintaining the necessary situational awareness to stay on the top of emerging security threats. This blog covers trends and fads, tactics and strategies, intersecting with third-party research, speculations and real-time CYBERINT assessments, all packed with sarcastic attitude
Monday, February 06, 2023
A Peek Inside a Mass SQL Injection Scanning and Exploiting IRC Botnet - An Analysis
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside the Spack Web Malware Exploitation Kit - An Analysis
Sample screenshots include:
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside a Milw0rm Syndicating Remote Execution Flaws Exploitable IRC Scanning Botnet - An Analysis
 Who would have thought? An IRC based botnet that's directly syndicating remotely exploitable flaws and actually scanning for them using an IRC based bothet? Takes you back doesn't it? This has been a daily practice since practically 2008 and I've decided to share some sample screenshots of the process in action.
Who would have thought? An IRC based botnet that's directly syndicating remotely exploitable flaws and actually scanning for them using an IRC based bothet? Takes you back doesn't it? This has been a daily practice since practically 2008 and I've decided to share some sample screenshots of the process in action. Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside the Xedant Human Emulator Spam Tool - An Analysis
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside the Xrumer Spam Tool - An Analysis
 Who would have thought? It's an unknown period of time within the cybercrime ecosystem and I've decided to share exclusive screenshots of the infamous Xrumer spam tool which basically used to and continues to dominate the spam marketplace by possessing a variety of advanced and sophisticated features making it easy for everyone to enter the world of spam globally.
Who would have thought? It's an unknown period of time within the cybercrime ecosystem and I've decided to share exclusive screenshots of the infamous Xrumer spam tool which basically used to and continues to dominate the spam marketplace by possessing a variety of advanced and sophisticated features making it easy for everyone to enter the world of spam globally.Sample screenshots include:
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside A Web Malware Exploitation Kit - An Analysis
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside the Zalupko Accounting Data Stealing Malicious Software Botnet - An Analysis
 Who would have thought? Takes you back doesn't it? As I've been going deep inside my old threat intelligence archive circa 2008 I've decided to share with everyone several never published or released before screenshots of the Zalupko accounting data stealing malicious software release botnet with the idea to raise everyone's spirit in the field of fighting cybercrime and doing research and possibly take your research motivation higher.
Who would have thought? Takes you back doesn't it? As I've been going deep inside my old threat intelligence archive circa 2008 I've decided to share with everyone several never published or released before screenshots of the Zalupko accounting data stealing malicious software release botnet with the idea to raise everyone's spirit in the field of fighting cybercrime and doing research and possibly take your research motivation higher. Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Thursday, January 26, 2023
Exposing Russian Business Network's Mykhaylo Sergiyovich Rytikov's AbdAllah Internet Hizmetleri Bulletproof Hosting Provider on U.S Secret Service's Most Wanted Cybercriminals List
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
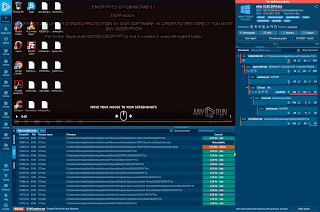
Exposing a Currently Active and Spreading Cobalt Strike Serving Malicious Software Campaign
MD5: d8d8cb60d196a26765261b1ca8604d1e
Sample C&C server IPs known to have been involved in the campaign include:
hxxp://5[.]253[.]234[.]40 -> hxxp://5[.]253[.]234[.]40/activity -> hxxp://5[.]253[.]234[.]40/activity/submit[.]php
Sample geolocation of the known C&C server IP:
hxxp://bpltjykhm[.]online
hxxp://51lqm[.]online
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside a Zunker Botnet C&C Administration Panel - An OSINT Analysis
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, January 17, 2023
Happy Holidays From The (Not) Republic of Bulgaria - An Analysis - Part Two
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Wednesday, December 28, 2022
Exposing a Portfolio of Currently Active Malware Serving Domain and URLs - An Analysis
Interested in finding out the latest and very greatest malicious software download locations for research purposes? Check out the following compilation courtesy of my compiled exclusively using public sources.
Grab the compilation from here.
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, December 27, 2022
Exposing a Portfolio of Fake News Disinformation and Misinformation Web Site Domains - A Compilation
I've decided to share with everyone a currently active domain portfolio of fake news disinformation and misinformation web sites which I obtained using technical collection with the idea to assist everyone in their cyber attack campaign attribution efforts.
Download the compilation here.
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Wednesday, December 21, 2022
My Official 256GB Research Compilation - An Analysis
Hot off the press. Grab the Torrent.
Sample photo:
Stay tuned! Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
The Profile of a Bulgarian Dipshit DANS Agent Vasil Stanev from Troyan Bulgaria - A Case Study on Local Mockery Corruption Kidnapping Robbery and Home Molestation Attempt - An Analysis
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, December 20, 2022
Exposing the "Data Leaks" Paradise - An Analysis
Sample uses of these stolen and compromised databases includes:
- setting the foundation for a successful spear-phishing campaigns
- setting the foundations for successful targeted malware and exploits serving campaigns
- setting the foundations for successful widespread spam and botnet propagation campaigns
- attempting to monetize the stolen database by selling access it to
- attempting to use double layer monetization for the stolen database by attempting to sell access to it including to the actual owners of the database who might be interested in obtaining a copy of it
- biased exclusivity and double layer monetization combination where the attacker might only sell the database to its actual owner and actually get rid of it once they receive the payment
The very notion that cybercriminals including white hat security experts and cybercrime fighters will eventually attempt to obtain access to for instance a compromised cybercrime forum for the purpose of exposing the personal details of its users that also include to possibly track down and geolocate including to actually profile and prosecute some of its members should be definitely considered as an old-fashioned trend in the actual fight against cybercrime online with more users and researchers joining the fight including the actual cybercriminals who might take additional measures to actually protect and prevent possible data leaks including various other OPSEC (Operational Security) type of measures in terms of positioning their cybercrime-friendly forum community as a invite-only or actually launching it in a a vetted and invite-only fashion.
What's should be clearly noted is that with the mainstream media continuing to raise awareness on the existence of high-profile hacking groups and hackers including the rise of the Anonymous crowd it should be clearly noted that wannabe and potential hackers would continue trying to steal the necessary media attention and actual "know-how" from high-profile hacking groups and individual hackers involved in high-profile data leaks and data breaches.
I believe that on the majority of occasions it's just ransomware that's making the headlines including its way into corporate networks thanks to the so called initial access brokers who on the majority of occasions are known to have been also outsourcing their hacking and network compromise needs to third-parties who would basically do an Attack Surface Reconnaissance on the Web and will attempt to find a weak spot into the corporate network of the targeted victim but would also attempt to data mine and harvest publicly accessible and obtainable email address accounts for the purpose of doing active social engineering reconnaissance that also includes the attempt to obtain accounting data belonging to these company individuals including to launch spear phishing attack campaigns against their infrastructure in an attempt to obtain access to their email address accounts home PCs and networks including related services ultimately attempting to compromise the security of the targeted network and the company in question.
Stay tuned!
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com













































.jpg)

