Stay tuned! Continue reading →
Stay tuned! Continue reading →
Sample screenshots include:
Stay tuned! Continue reading →
A Peek Inside a Milw0rm Syndicating Remote Execution Flaws Exploitable IRC Scanning Botnet - An Analysis
0 Who would have thought? An IRC based botnet that's directly syndicating remotely exploitable flaws and actually scanning for them using an IRC based bothet? Takes you back doesn't it? This has been a daily practice since practically 2008 and I've decided to share some sample screenshots of the process in action.
Who would have thought? An IRC based botnet that's directly syndicating remotely exploitable flaws and actually scanning for them using an IRC based bothet? Takes you back doesn't it? This has been a daily practice since practically 2008 and I've decided to share some sample screenshots of the process in action.Stay tuned! Continue reading →
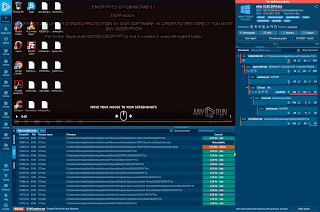
 Who would have thought? It's an unknown period of time within the cybercrime ecosystem and I've decided to share exclusive screenshots of the infamous Xrumer spam tool which basically used to and continues to dominate the spam marketplace by possessing a variety of advanced and sophisticated features making it easy for everyone to enter the world of spam globally.
Who would have thought? It's an unknown period of time within the cybercrime ecosystem and I've decided to share exclusive screenshots of the infamous Xrumer spam tool which basically used to and continues to dominate the spam marketplace by possessing a variety of advanced and sophisticated features making it easy for everyone to enter the world of spam globally.Sample screenshots include:
Stay tuned! Continue reading →
A Peek Inside the Zalupko Accounting Data Stealing Malicious Software Botnet - An Analysis
0 Who would have thought? Takes you back doesn't it? As I've been going deep inside my old threat intelligence archive circa 2008 I've decided to share with everyone several never published or released before screenshots of the Zalupko accounting data stealing malicious software release botnet with the idea to raise everyone's spirit in the field of fighting cybercrime and doing research and possibly take your research motivation higher.
Who would have thought? Takes you back doesn't it? As I've been going deep inside my old threat intelligence archive circa 2008 I've decided to share with everyone several never published or released before screenshots of the Zalupko accounting data stealing malicious software release botnet with the idea to raise everyone's spirit in the field of fighting cybercrime and doing research and possibly take your research motivation higher.Exposing Russian Business Network's Mykhaylo Sergiyovich Rytikov's AbdAllah Internet Hizmetleri Bulletproof Hosting Provider on U.S Secret Service's Most Wanted Cybercriminals List
0Exposing a Currently Active and Spreading Cobalt Strike Serving Malicious Software Campaign
0MD5: d8d8cb60d196a26765261b1ca8604d1e
Sample C&C server IPs known to have been involved in the campaign include:
hxxp://5[.]253[.]234[.]40 -> hxxp://5[.]253[.]234[.]40/activity -> hxxp://5[.]253[.]234[.]40/activity/submit[.]php
Sample geolocation of the known C&C server IP:
hxxp://bpltjykhm[.]online
hxxp://51lqm[.]online
Exposing a Portfolio of Currently Active Malware Serving Domain and URLs - An Analysis
0Interested in finding out the latest and very greatest malicious software download locations for research purposes? Check out the following compilation courtesy of my compiled exclusively using public sources.
Grab the compilation from here.
Stay tuned!
Continue reading →Exposing a Portfolio of Fake News Disinformation and Misinformation Web Site Domains - A Compilation
0I've decided to share with everyone a currently active domain portfolio of fake news disinformation and misinformation web sites which I obtained using technical collection with the idea to assist everyone in their cyber attack campaign attribution efforts.
Download the compilation here.
Stay tuned!
Continue reading →Hot off the press. Grab the Torrent.
Sample photo:
Stay tuned! Continue reading →












































.jpg)

RSS Feed