In the overwhelming sea of information, access to timely, insightful and independent open-source intelligence (OSINT) analyses is crucial for maintaining the necessary situational awareness to stay on the top of emerging security threats. This blog covers trends and fads, tactics and strategies, intersecting with third-party research, speculations and real-time CYBERINT assessments, all packed with sarcastic attitude
Thursday, August 01, 2013
Summarizing Webroot's Threat Blog Posts for July
The following is a brief summary of all of my posts at Webroot's Threat Blog for July, 2013. You can subscribe to Webroot's Threat Blog RSS Feed, or follow me on Twitter:
01. Cybercriminals experiment with Tor-based C&C, ring-3-rootkit empowered, SPDY form grabbing malware bot
02. Deceptive ads targeting German users lead to the ‘W32/SomotoBetterInstaller’ Potentially Unwanted Application (PUA)
03. Newly launched underground market service harvests mobile phone numbers on demand
04. Novel ransomware tactic locks users’ PCs, demands that they participate in a survey to get the unlock code
05. Spamvertised ‘Export License/Invoice Copy’ themed emails lead to malware
06. Cybercriminals spamvertise tens of thousands of fake ‘Your Booking Reservation at Westminster Hotel’ themed emails, serve malware
07. New commercially available mass FTP-based proxy-supporting doorway/malicious script uploading application spotted in the wild
08. Fake ‘iGO4 Private Car Insurance Policy Amendment Certificate’ themed emails lead to malware
09. Tens of thousands of spamvertised emails lead to the Win32/PrimeCasino PUA (Potentially Unwanted Application)
10. Spamvertised ‘Vodafone U.K MMS ID/Fake Sage 50 Payroll’ themed emails lead to (identical) malware
11. New commercially available Web-based WordPress/Joomla brute-forcing tool spotted in the wild
12. Rogue ads targeting German users lead to Win32/InstallBrain PUA (Potentially Unwanted Application)
13. Yet another commercially available stealth Bitcoin/Litecoin mining tool spotted in the wild
14. Deceptive ‘Media Player Update’ ads expose users to the rogue ‘Video Downloader/Bundlore’ Potentially Unwanted Application (PUA)
15. Newly launched ‘HTTP-based botnet setup as a service’ empowers novice cybercriminals with bulletproof hosting capabilities
16. Fake ‘Copy of Vodafone U.K Contract/Your Monthly Vodafone Bill is Ready/New MMS Received’ themed emails lead to malware
17. Rogue ads lead to the ‘Free Player’ Win32/Somoto Potentially Unwanted Application (PUA)
18. How much does it cost to buy one thousand Russian/Eastern European based malware-infected hosts?
19. Custom USB sticks bypassing Windows 7/8's AutoRun protection measure going mainstream
20. DIY commercially-available ‘automatic Web site hacking as a service’ spotted in the wild
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, July 23, 2013
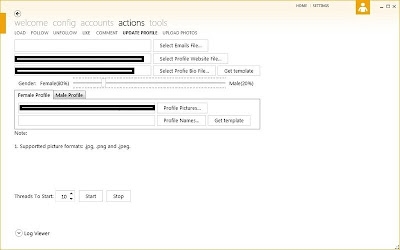
Instagram Under Fire as Cybercriminals Release New DIY Fake Account Registration/Management/Promotion Tool
In 2013, CAPTCHAs represent an outdated approach for a Web site wanting to prevent the efficient and systematic abuse of its services.
This fact, largely driven by the rise of cost-effective CAPTCHA solving solutions offered by low-waged individuals internationally over the last couple of years, continues to empower virtually anyone possessing the right cybercrime-friendly tools, with the ability to abuse any major Web property in a potentially fraudulent or malicious way.
In this post, I'll profile one of the most recently released DIY fake account registration/management/promoting tool, targeting Instagram, highlight its core features, as well as emphasize on the true impact that these tools are having on some of the world's most popular Web properties.
Sample screenshots of the tool in action:
Some of its core features are:
Known cases of abuse of legitimate infrastructure for fraudulent/malicious purposes over the years include:
Bogus "Shocking Video" Content at Scribd Exposes Malware Monetization Scheme Through Parked Domains
Fake Codec Serving Domains from Digg.com's Comment Spam Attack
Bogus LinkedIn Profiles Redirect to Malware and Rogue Security Software
Dissecting the Bogus LinkedIn Profiles Malware Campaign
From Ukraine with Scareware Serving Tweets, Bogus LinkedIn/Scribd Accounts, and Blackhat SEO Farms
Celebrity-Themed Scareware Campaign Abusing DocStoc and Scribd
Celebrity-Themed Scareware Campaign Abusing DocStoc
From Ukraine with Bogus Twitter, LinkedIn and Scribd Accounts
Pharmaceutical Spammers Targeting LinkedIn
This fact, largely driven by the rise of cost-effective CAPTCHA solving solutions offered by low-waged individuals internationally over the last couple of years, continues to empower virtually anyone possessing the right cybercrime-friendly tools, with the ability to abuse any major Web property in a potentially fraudulent or malicious way.
In this post, I'll profile one of the most recently released DIY fake account registration/management/promoting tool, targeting Instagram, highlight its core features, as well as emphasize on the true impact that these tools are having on some of the world's most popular Web properties.
Sample screenshots of the tool in action:
Some of its core features are:
- support for multi-threads
- set number ot accounts to generate using a single proxy (malware-infected host)
- randomization of the posted bogus content to avoid easy detection of the pattern
- male/female fake account creating capabilities
- mass account validity checking capabilities
- CAPTCHA-solving integration with third-party CAPTCHA solving services
Known cases of abuse of legitimate infrastructure for fraudulent/malicious purposes over the years include:
Bogus "Shocking Video" Content at Scribd Exposes Malware Monetization Scheme Through Parked Domains
Fake Codec Serving Domains from Digg.com's Comment Spam Attack
Bogus LinkedIn Profiles Redirect to Malware and Rogue Security Software
Dissecting the Bogus LinkedIn Profiles Malware Campaign
From Ukraine with Scareware Serving Tweets, Bogus LinkedIn/Scribd Accounts, and Blackhat SEO Farms
Celebrity-Themed Scareware Campaign Abusing DocStoc and Scribd
Celebrity-Themed Scareware Campaign Abusing DocStoc
From Ukraine with Bogus Twitter, LinkedIn and Scribd Accounts
Pharmaceutical Spammers Targeting LinkedIn
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Instagram Under Fire as Cybercriminals Release New DIY Fake Account Registration/Management/Promotion Tool
In 2013, CAPTCHAs represent an outdated approach for a Web site wanting to prevent the efficient and systematic abuse of its services.
This fact, largely driven by the rise of cost-effective CAPTCHA solving solutions offered by low-waged individuals internationally over the last couple of years, continues to empower virtually anyone possessing the right cybercrime-friendly tools, with the ability to abuse any major Web property in a potentially fraudulent or malicious way.
In this post, I'll profile one of the most recently released DIY fake account registration/management/promoting tool, targeting Instagram, highlight its core features, as well as emphasize on the true impact that these tools are having on some of the world's most popular Web properties.
Sample screenshots of the tool in action:
Some of its core features are:
24/7/365.
Known cases of abuse of legitimate infrastructure for fraudulent/malicious purposes over the years include:
This fact, largely driven by the rise of cost-effective CAPTCHA solving solutions offered by low-waged individuals internationally over the last couple of years, continues to empower virtually anyone possessing the right cybercrime-friendly tools, with the ability to abuse any major Web property in a potentially fraudulent or malicious way.
In this post, I'll profile one of the most recently released DIY fake account registration/management/promoting tool, targeting Instagram, highlight its core features, as well as emphasize on the true impact that these tools are having on some of the world's most popular Web properties.
Sample screenshots of the tool in action:
Some of its core features are:
- support for multi-threads
- set number ot accounts to generate using a single proxy (malware-infected host)
- randomization of the posted bogus content to avoid easy detection of the pattern
- male/female fake account creating capabilities
- mass account validity checking capabilities
- CAPTCHA-solving integration with third-party CAPTCHA solving services
24/7/365.
Known cases of abuse of legitimate infrastructure for fraudulent/malicious purposes over the years include:
- Bogus "Shocking Video" Content at Scribd Exposes Malware Monetization Scheme Through Parked Domains
- Fake Codec Serving Domains from Digg.com's Comment Spam Attack
- Bogus LinkedIn Profiles Redirect to Malware and Rogue Security Software
- Dissecting the Bogus LinkedIn Profiles Malware Campaign
- From Ukraine with Scareware Serving Tweets, Bogus LinkedIn/Scribd Accounts, and Blackhat SEO Farms
- Celebrity-Themed Scareware Campaign Abusing DocStoc and Scribd
- Celebrity-Themed Scareware Campaign Abusing DocStoc
- From Ukraine with Bogus Twitter, LinkedIn and Scribd Accounts
- Pharmaceutical Spammers Targeting LinkedIn
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Friday, July 19, 2013
A Peek Inside a Managed OTP/ATS/TAN Token Bypassing/Hijacking/Blocking System as a (Licensed) Service
One of the most common questions that I get during Q&A sessions after a PPT, or in a face-to-face conversation is - "Hello, my name is [name], I represent [random financial institution]. Are we being targeted based on your situational awareness?"
For years, virtually every company, every brand, every financial institution has been targeted, largely thanks to the rise of Crimeware-as-a-Service underground market propositions offering standardized and cybercrime-release friendly 'Web Injects', the result of active pre-sale reconnaissance performed on the E-banking service of the targeted institution. The business model is fairly simple - next to 'pushing' a pre-defined set of 'Web Injects' for some of the largest and well known financial institutions in the World, 'Web Injects' for virtually any SSL/Two-Factor Authentication enabled Web site, can be requested and produced on demand, usually for a static amount of money.
"But we issue two-factor authentication tokens to our customers. Isn't this making any change?"
Sophisticated cybercriminals possessing 'innovative' underground market disrupting forces, have been undermining two-factor authentication for years. An uncomfortable truth that your financial institution of choice wouldn't necessarily want you to know about, as it would most commonly risk-forward the responsibility to you, under a contractual agreement, or actually possess an industry-accepted certification for the operation of such online services, thanks to the introduction of two-factor authentication, and the internal security measures preventing a direct compromise of the financial institution's infrastructure.
With source code for the ZeuS crimeware, as well as Carberp, publicly available for virtually anyone to download, it shouldn't be surprising that cybercriminals have started to release more crimeware, using these prominent releases, in an attempt to quickly capitalize on the source code that's been contributing to a huge percentage of the profitability of the cybercrime ecosystem in general.
What are some of the latest 'innovations" in the world of Cybercrime-as-a-Service, in particular the market segment for "Web Injects"? Are cybercriminals striving to produce ZeuS/Carberp like underground market "products", or are they attempting to disrupt the entire cybercrime ecosystem by offering a standardizing E-banking Web site reconnaissance services, that would work on virtually any publicly obtainable/leaked source code based crimeware/malware release?
That's exactly what the cybercriminal whose underground market proposition I'm about to profile, is doing - offering crimeware-independent standardized on demand "Web Injects", in particular OTP (One-Time-Password), ATS (Automatic Transfer Service), TAN (Transaction Authentication Number) bypassing/hijacking/blocking system, or in those cases where the customer demands - offer "finished crimeware products"?
Sample automatically translated underground market proposition:
I am writing to inject custom-made as well as offer finished products.
The main provisions of the Service:
1. Tools manufactures both private and public products.
1.1 Under the private means software products manufactured "in one hand" with the full right to transfer and resale. The client of the right to require the source code private product. Support for the private software somewhere executed in priority order.
1.2 If the "privacy" of the product is not stipulated in advance that product becomes the default public service and the right to sell it to other customers.
1.3 Prices for private products involve premium of 50% to the price of the underlying / social product.
1.4 Distribution / Transmission of any parts of the code or of the products purchased on the basis of the public, will result in a denial of service on all products purchased from third-party service, followed by filing a complaint in section Black List.1.5 Public products are delivered on an "as is," and do not include its value of any additions or changes.
1.5.1 Any changes to the products are made public as an additional order and measured in accordance with the workload.
1.6 Service does not run on the lease terms. Only a piecework basis!1.7 Service does not give advice about cross-translation, relevance or affine those topics. For providing information about banks / cantor Service is not responsible.2. Service is responsible for the performance of the paid code for the negotiated period.
2.1 If the period of service is not verbalized it enters into force standard warranty period is 10 days from the date of issue of working product.
3. Warranties:
3.1 The Service shall recover from the purchased products for a specified warranty period, for that is technically possible. Free of charge - during the warranty period, and the charge on the expiration of the warranty period. Prices for the repair of products range from $ 10 up to the full cost of the product and depend directly on the volume of the work.
3.2. Service is not responsible for the failure of performance caused by the code:
3.2.1 The introduction of third-party software which prevents full operation. (Rapport)
3.2.2 The introduction of sms / email notifications that can not be disabled by means of injection.
3.2.3 The introduction of this activity exhibiting malicious code (without the possibility of elimination)
3.2.4 The other changes in the source code of banks / sites prevent recovery of the product.
3.3 The Service does not guarantee a return to work ordered acquired products, but only can guarantee the performance of the software according to the negotiated terms of reference.
4. Approximate prices for soft (public foundation)grabber balance of $ 10 (1 unit)popup $ 70 Fake full page from $ 150 repleyser from $ 450 (3 units each include an additional $ 50 .. 100) grabbers data from 150 $ Automated OTP/ATS/TAN from $ 2500
Sample explanation of the service in action, courtesy of the cybercriminal behind it:
Sample screenshots of the service in action:
Sample screenshot of the ATSEngine in action targeting HSBC:
Some of the most recent updates to the system include:
01/11/2012 - Sets fullinfo grabbers for AU (37 banks) / CA (30 banks) / US (40 banks). Data on Holder to SSN / MMN / DOB / DL / DL exp / VBV ...
01/11/2012 - Grabbers CC + VBV (paypal, ebay, amazon, facebook)
01/11/2012 - The system change number and Grabing necessary disk imaging (input issues, balance sheets) for the Gulf santander.co.uk (instant on UK to 10kGBP)
02/11/2012 - Grabber additional data for paypal (DE / UK / AU / with the possibility to add other countries). Collects: Name Holder, Balance, Status (verif / neverif), Account Type, Time of the last entry, as well as rooms full of affection card and / or bank accounts for the AU and the UK, and questions with answers for DE
13/11/2012 - Grabber TANs to ipko.pl
23/11/2012 - Avtozaliv on hsbc.co.uk
23/11/2012 - Grabber cc + cvv + exp + pin. works on all pages on which the algorithm finds on LUHN10 card number and exp field and collects requests PIN
11/29/2012 - intercept system / bypass token to fnb.co.za
Two-factor authentication - indeed, an additional layer of security for your E-banking account, however, everything changes on a crimeware-infected host, and sadly, it changes in favor of the cybercriminal that compromised it.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside a Managed OTP/ATS/TAN Token Bypassing/Hijacking/Blocking System as a (Licensed) Service
One of the most common questions that I get during Q&A sessions after a PPT, or in a face-to-face conversation is - "Hello, my name is [name], I represent [random financial institution]. Are we being targeted based on your situational awareness?"
For years, virtually every company, every brand, every financial institution has been targeted, largely thanks to the rise of Crimeware-as-a-Service underground market propositions offering standardized and cybercrime-release friendly 'Web Injects', the result of active pre-sale reconnaissance performed on the E-banking service of the targeted institution. The business model is fairly simple - next to 'pushing' a pre-defined set of 'Web Injects' for some of the largest and well known financial institutions in the World, 'Web Injects' for virtually any SSL/Two-Factor Authentication enabled Web site, can be requested and produced on demand, usually for a static amount of money.
"But we issue two-factor authentication tokens to our customers. Isn't this making any change?"
Sophisticated cybercriminals possessing 'innovative' underground market disrupting forces, have been undermining two-factor authentication for years. An uncomfortable truth that your financial institution of choice wouldn't necessarily want you to know about, as it would most commonly risk-forward the responsibility to you, under a contractual agreement, or actually possess an industry-accepted certification for the operation of such online services, thanks to the introduction of two-factor authentication, and the internal security measures preventing a direct compromise of the financial institution's infrastructure.
With source code for the ZeuS crimeware, as well as Carberp, publicly available for virtually anyone to download, it shouldn't be surprising that cybercriminals have started to release more crimeware, using these prominent releases, in an attempt to quickly capitalize on the source code that's been contributing to a huge percentage of the profitability of the cybercrime ecosystem in general.
What are some of the latest 'innovations" in the world of Cybercrime-as-a-Service, in particular the market segment for "Web Injects"? Are cybercriminals striving to produce ZeuS/Carberp like underground market "products", or are they attempting to disrupt the entire cybercrime ecosystem by offering a standardizing E-banking Web site reconnaissance services, that would work on virtually any publicly obtainable/leaked source code based crimeware/malware release?
That's exactly what the cybercriminal whose underground market proposition I'm about to profile, is doing - offering crimeware-independent standardized on demand "Web Injects", in particular OTP (One-Time-Password), ATS (Automatic Transfer Service), TAN (Transaction Authentication Number) bypassing/hijacking/blocking system, or in those cases where the customer demands - offer "finished crimeware products"?
Sample automatically translated underground market proposition:
I am writing to inject custom-made as well as offer finished products.
The main provisions of the Service:
1. Tools manufactures both private and public products.
1.1 Under the private means software products manufactured "in one hand" with the full right to transfer and resale. The client of the right to require the source code private product. Support for the private software somewhere executed in priority order.
1.2 If the "privacy" of the product is not stipulated in advance that product becomes the default public service and the right to sell it to other customers.
1.3 Prices for private products involve premium of 50% to the price of the underlying / social product.
1.4 Distribution / Transmission of any parts of the code or of the products purchased on the basis of the public, will result in a denial of service on all products purchased from third-party service, followed by filing a complaint in section Black List.1.5 Public products are delivered on an "as is," and do not include its value of any additions or changes.
1.5.1 Any changes to the products are made public as an additional order and measured in accordance with the workload.
1.6 Service does not run on the lease terms. Only a piecework basis!1.7 Service does not give advice about cross-translation, relevance or affine those topics. For providing information about banks / cantor Service is not responsible.2. Service is responsible for the performance of the paid code for the negotiated period.
2.1 If the period of service is not verbalized it enters into force standard warranty period is 10 days from the date of issue of working product.
3. Warranties:
3.1 The Service shall recover from the purchased products for a specified warranty period, for that is technically possible. Free of charge - during the warranty period, and the charge on the expiration of the warranty period. Prices for the repair of products range from $ 10 up to the full cost of the product and depend directly on the volume of the work.
3.2. Service is not responsible for the failure of performance caused by the code:
3.2.1 The introduction of third-party software which prevents full operation. (Rapport)
3.2.2 The introduction of sms / email notifications that can not be disabled by means of injection.
3.2.3 The introduction of this activity exhibiting malicious code (without the possibility of elimination)
3.2.4 The other changes in the source code of banks / sites prevent recovery of the product.
3.3 The Service does not guarantee a return to work ordered acquired products, but only can guarantee the performance of the software according to the negotiated terms of reference.
4. Approximate prices for soft (public foundation)grabber balance of $ 10 (1 unit)popup $ 70 Fake full page from $ 150 repleyser from $ 450 (3 units each include an additional $ 50 .. 100) grabbers data from 150 $ Automated OTP/ATS/TAN from $ 2500
Sample explanation of the service in action, courtesy of the cybercriminal behind it:
Sample screenshots of the service in action:
Sample screenshot of the ATSEngine in action targeting HSBC:
Some of the most recent updates to the system include:
01/11/2012 - Sets fullinfo grabbers for AU (37 banks) / CA (30 banks) / US (40 banks). Data on Holder to SSN / MMN / DOB / DL / DL exp / VBV ...
01/11/2012 - Grabbers CC + VBV (paypal, ebay, amazon, facebook)
01/11/2012 - The system change number and Grabing necessary disk imaging (input issues, balance sheets) for the Gulf santander.co.uk (instant on UK to 10kGBP)
02/11/2012 - Grabber additional data for paypal (DE / UK / AU / with the possibility to add other countries). Collects: Name Holder, Balance, Status (verif / neverif), Account Type, Time of the last entry, as well as rooms full of affection card and / or bank accounts for the AU and the UK, and questions with answers for DE
13/11/2012 - Grabber TANs to ipko.pl
23/11/2012 - Avtozaliv on hsbc.co.uk
23/11/2012 - Grabber cc + cvv + exp + pin. works on all pages on which the algorithm finds on LUHN10 card number and exp field and collects requests PIN
11/29/2012 - intercept system / bypass token to fnb.co.za
Two-factor authentication - indeed, an additional layer of security for your E-banking account, however, everything changes on a crimeware-infected host, and sadly, it changes in favor of the cybercriminal that compromised it.
Tags:
ATS,
Botnet,
Cybercrime,
Hacking,
Information Security,
Malicious Software,
OTP,
Security,
TAN,
Two-Factor Authentication,
Web Inject
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Subscribe to:
Comments (Atom)