Anonymous Bulgaria is your typical Anonymous “franchise” Anonymous hackers model where you have a group of people doing web site defacements and compromises of legitimate web sites and infrastructure and actually blame a bigger cause that they don’t really have anything to do with and don’t understand or know anything about it.
The ultimate goal here would be for the group to gain momentum including to attract followers where the ultimate goal would be to spread a message that they don’t often understand or have anything to do with low profile DDoS attacks or cyber attack attempts similar and typical to the Anonymous hackers collective idea.
Is it script kiddies or low profile wannabe hacker groups that basically have one social media account and are capable of launching low profile cyber attack attempts that often make the news or is it a bigger conspiracy where everyone doing the same can outsource their responsibility for doing it to the entire “idea” which basically represents an Anonymous set of people attempting to do low profile cyber attack attempts?
Let’s go for the first part.
The important part when dealing with this type of low profile threat actor is to usually keep track of their activities including social media profiles and activity and look for additional clues in terms of current and ongoing cyber attacks and most importantly look for additional clues such as personally identifiable information which would be later on used in a possible cyber threat actor attribution campaigns including for the actual enrichment of this PII for the purpose of looking for additional clues in terms of doing threat actor infrastructure reconnaissance on your way to look for additional clues such as related malicious and fraudulent including cybercrime activity including domains personally identifiable email address accounts or related social media accounts.
The ultimate goal when collecting these would be yo either build a database of the threat actor in question which could lead to a possible commercial or community driven project venture or to assist fellow researchers and Law Enforcement on its way go track down monitor and prosecute these individuals.
In this article I’ll discuss in-depth the Anonymous Bulgaria hacker franchise that basically just like many other Anonymous franchises across the globe basically represent low profile cyber attack attempts type of threat actors and will provide personally identifiable information on their online whereabouts.
Some of the other Bulgarian Web site defacement groups that are known to work and cooperate with Bulgarian Cyber Army include BG Worm, MTH Soft, Hack3D TeaM and EvilHack and Anonymous Bulgaria.
What’s specifically interesting about Bulgarian Cyber Army is that the group appears to be still and currently active and operational based on some of their latest web site defacement and Facebook activity.
Personally Identifiable Information on Bulgarian Cyber Army:
hxxp://facebook.com/hack3dteam
hxxp://vimeo.com/user16145338/videos
Personally Identifiable Information on Hack3d Team:
MaStErHaCk
Slackera
Tiger
RTFM
Sspdf11
PanteliX
Metalqear
MaStErChO
W!PS
TraferA
3ikmy
r00tkit
The Godfather
razora911
Personally Identifiable Information on EvilHack:
EvilHack[.]hmamail.com
anonyops[.]abv.bg
genadi_100[.]abv.bg
evil_hack[.]abv.bg
evilhack[.]bk.ru
evilhack000[.]gmail.com
clangrf[.]abv.bg
hxxp://anonymous-world.free.bg
hxxp://web-dangerous.free.bg
hxxp://evilhack-official.blogspot.com/
Personally Identifiable Information on Anonymous Bulgaria:
NoTolerance
Hades
PsychoPatternz
rootheR_
hxxp://anonbg.info
Continue reading →In my line of work in specific when doing research and analysis I always stick to a common concept which has to do with the fact that “everything that can be found has already been found somewhere online”. Sticking to this basic methodology the only thing an individual or a researcher has to do is to look up the facts including all the relevant and necessary technical information on the individual or case they’re working on and basically come up with a proper analysis relying on publicly obtainable and publicly accessible information on their topic of interest.
In this rather long OSINT analysis article I’ll do a OSINT roundup of Russia-based high-profile ransomware cybercriminals with the idea to share my research and analysis on the topic and potentially assist other researchers and vendors including U.S Law Enforcement on its way to properly track down and monitor and prosecute these cybercriminals.
\I’ll begin this analysis with an emphasis and actual OSINT research and analysis on the Conti Ransomware Group in the context of demonstrating what real-time OSINT is which a pretty good and decent methodology that I’ve been relying and using over the years which works.
It all began with an internally leaked and made publicly accessible Conti Ransomware Gang’s internal communication where a security researcher or a set of security researchers appear to have compromised their internal server and have been collecting conversation logs between the cybercriminals which they later on made publicly accessible on Twitter in a specific for the purpose account that basically included direct download links to their internal communication.
From an OSINT perspective the first thing a researcher should do is to do their best to obtain access to these conversation logs and attempt to preserve them for current and future use which is something that I did almost immediately considering the possibility to monitor and track down who the actual individuals behind this massive ransomware campaign are.
The results? I’ve managed to successfully identify some of key individuals behind the Conti Ransomware Gang in terms of top management where my believe is that although it was a hired or outsourced “know-how” in the beginning quickly matured into a cybercrime enterprise where everyone who wanted to could join on a “franchise” based model and just do their work and earn fraudulently and maliciously obtained revenue from legitimate companies who are having their networks compromised and sensitive data and information made publicly accessible or basically encrypted in a way making it impossible for the actual organization and company to use.
What is the Conti ransomware gang up to in terms of top management? It appears that the gang’s top management in a way is involved in the fashion industry with the idea that some of the screenshots that I obtained and processed and analyzed which were leaked internally in the form of exchange of URLs between the gang’s members lead me to believe that the gang is involved in either investing in fashion brands or actually working on such with several successful public OSINT analyses on the topic where I’ve managed to identify some of the fashion brands behind the Conti Ransomware Gang’s top management and my goal here is to present the actual findings with the idea to bring this fact to more light in the context of providing information on the activity of the Conti Ransomware Gang’s top management members.
So basically once I came across their internal leaked communication made publicly accessible on Twitter I immediately aimed to obtain access to the leaked internal information of the Conti ransomware gang and preserve it before it goes online so that I can later on work with it and successfully produce the analysis including all the screenshots managed and operated by the Conti ransomware gang and here’s how I did it.
Basically once I obtained access to their internal leaked communication which was made publicly accessible I data mined the internal leaked communication looking for personally identifiable email address accounts and related URLs with success which is where I automatically visited these URLs which I data mined in the Conti ransomware gang’s internal leaked communication and basically grabbed all the live URLs information which is where the analysis and the screenshots including the actual report come from which I produced and have been working on to produce exclusively for fellow researchers and vendors including U.S Law Enforcement in order to assist everyone on their way to properly track down monitor and prosecute.
Sample Internally Leaked URLs Courtesy of the Conti Ransomware Gang Obtained Using Public Sources
There are several other fashion brand themed screenshots which I also managed to obtain which appear to be directly related to the Conti ransomware gang.
Here are some of the “upcoming brands” courtesy of the Conti Ransomware Gang obtained using real-time OSINT and relying on their internally leaked communications proving the gang including its top management is into fashion brands and the industry:
Here’s some personally identifiable information on some of the brands using OSINT and public sources of information:
Leylo
Top Management Includes:
tel:+79126331303
Мария Сергеевна Ермолаева/Maria Ermolaeva (Chudnova)
Birthday: 5 July
hxxp://vk.com/id7326657
Maria Ermolaeva
Birthday: 5 July
г. Екатеринбург, ул. Репина, 95, офис 116
Телефон: +7 (912) 633–13–03
Е-mail: info@leylo.ru
leyloekb@gmail.com
hxxp://leylo.ru/
Danil Ermolaev
hxxp://vk.com/id4874860
Birthday: 7 August 1989
Sample Top Management Photos and Personally Identifiable Information of the Conti Ransomware Gang’s charity fund:
Tamila Kerimova
Conti Ransomware Gang’s Top Management Team
hxxp://impulse-life.ru
Tamila Kerimova
— Birthday: 4 April 1986
— hxxp://vk.com/id6515862
— Planet for beauty and development
— hxxp://irinaverhusha.com
Тел: +7 926 536–63–68
Email: impulse.life2020@gmail.com
Sample Internally Leaked Screenshots Courtesy of the Conti Ransomware Gang:
Sample Conti Ransomware Gang’s Internal Leaked Screenshots
Sample Related Internally Leaked Screenshots Courtesy of the Conti Ransomware Gang:
Sample Conti Ransomware Gang’s Internal Leaked Screenshots
Sample Conti Ransomware Gang’s Internal Leaked XMPP/Jabber Account IDs:
LiamNeeson@jabber.ru
arb_reserved@ubuntu-jabber.de
battletoad@jabbim.sk
begemot_sun@jabber.ru
crazy_digger@jabber.ru
gfh6776@jabb.im
ivanalert@jabber.ru
landslide@jabb.im
new_henry@jabber.cz
scopehope@jabb.im
ugly@1jabber.com
valerius2k@jabber.ru
vdx17@jabber.ru
337788@exploit.im
asteradminn@sure.im
benalen@exploit.im
bio@yax.im
crunch@exploit.im
daiverjm@exploit.im
dmanager@exploit.im
fuckUSAhahaha@exploit.im
fuckusa@exploit.im
gfh6776@jabb.im
goldcoin@exploit.im
jackiedugn@exploit.im
landslide@jabb.im
martiniden123@exploit.im
mr_loki@exploit.im
posi_tron@exploit.im
pravdazanami@exploit.im
rob0660@conversations.im
scopehope@jabb.im
soulst@exploit.im
time_t@exploit.im
trqa23rt@exploit.im
volhvb@exploit.im
yastreb@exploit.im
SamCodeSign@xmpp.jp
alieelu@xmpp.jp
baton@xmpp.jp
batono@xmpp.jp
benalien@xmpp.jp
cosm123@xmpp.jp
graddds@xmpp.jp
guliver@xmpp.sh
liamliam@xmpp.jp
ohmygod728@xmpp.jp
Denis Gennadievich Kulkov
Personal Photo of Denis Gannadievich Kulkov
Among the actual domains known to be part of the Try2Check cybercriminals enterprise include:
hxxp://try2services[.]pm
hxxp://try2services[.]cm
hxxp://try2services[.]vc
including the following domain:
hxxp://just-buy[.]it
including the following two ICQ numbers 855377 and 555724 and let’s don’t forget his personal email address accounts obtained using public sources which are polkas@bk.ru nordexin@ya.ru
and it doesn’t get any better than this as we’ve got a pretty good and informative domain portfolio registered by the same individual based on public information sharing the same domain registration details such as for instance hxxp://worldissuer[.]biz which actually are:
hxxp://cloud-mine[.]me
hxxp://gpucloud[.]org
hxxp://hyperhost[.]info
hxxp://miservers[.]info
hxxp://carterdns[.]com
hxxp://reshipping[.]us
hxxp://keyserv[.]org
hxxp://antmining[.]biz
hxxp://investmentauditor[.]com
hxxp://sunnylogistics[.]us
hxxp://try2services[.]cm
hxxp://greatwallhost[.]net
hxxp://jaqjckugrfffqa[.]com
hxxp://numberoneforyou[.]net
hxxp://getprofitnow[.]biz
hxxp://avsdefender[.]com
hxxp://spyware-defender[.]com
hxxp://beta-dns[.]net
hxxp://mpm-profit-method[.]com
hxxp://public-dns[.]us — related including this
hxxp://adobe-update[.]net — Email: krownymaradonna@onionmail.org related domains known to have been involved in the campaign include — hxxp://amazon-clouds[.]com; hxxp://microsoft-clouds[.]net; hxxp://telenet-cloud[.]com; hxxp://vmware-update[.]com
hxxp://kwitri[.]net
hxxp://dcm-trade[.]com
hxxp://karoospin[.]biz
hxxp://fastvps[.]biz
Evgeniy Mikhaylovich Bogachev
Sample Personal Photos of Evgeniy Mikhaylovich Bogachev:
Slavik’s IM and personal email including responding IP:
bashorg@talking.cc — 112.175.50.220
Personal Address:
Lermontova Str. Anapa, Russian Federation
Instant Messaging account:
lucky12345@jabber.cz
Related name servers:
ns.humboldtec.cz — 88.86.102.49
ns2.humboldtec.cz — 188.165.248.173
Related domains part of a C&C phone-back location:
hxxp://slaviki-res1.com
hxxp://slavik1.com — 91.213.72.115
hxxp://slavik2.com
hxxp://slavik3.com
Slavik’s primary email:
luckycats2008@yahoo.com
Slavik’s ICQ numbers:
ICQ — 42729771
ICQ — 312456
Related emails known to have participated in the campaign:
alexgarbar-chuck@yahoo.com
bollinger.evgeniy@yandex.ru
charajiang16@gmail.com
Related domains known to have participated in the campaign:
hxxp://visitcoastweekend.com — 103.224.182.253; 70.32.1.32; 192.184.12.62; 141.8.224.93; 69.43.160.163
hxxp://incomeet.com — 192.186.226.71; 66.199.248.195
hxxp://work.businessclub.so
Real Name: Galdziev Chingiz
Related domains known to have participated in the campaign:
hxxp://fizot.org
hxxp://fizot.com — 50.63.202.35; 184.168.221.33
hxxp://poymi.ru — 109.206.190.54
Related name servers known to have participated in the campaign:
ns1.fizot.com — 35.186.238.101
ns2.fizot.com
Related domain including an associated email using the same name server:
hxxp://averfame.org — harold@avereanoia.org
Google Analytics ID: UA-3816538
Related domains known to have participated in the campaign:
hxxp://awmproxy.com
hxxp://pornxplayer.com
Related emails known to have participated in the campaign:
fizot@mail.ru
xtexgroup@gmail.com
xtexcounter@bk.ru
Related domains known to have responded to the same malicious and fraudulent IP — 178.162.188.28:
hxxp://dnevnik.cc
hxxp://xvpn.ru
hxxp://xsave.ru
hxxp://anyget.ru
hxxp://nezayti.ru
hxxp://proproxy.ru
hxxp://hitmovies.ru
hxxp://appfriends.ru
hxxp://naraboteya.ru
hxxp://naraboteya.ru
hxxp://awmproxy.com
hxxp://zzyoutube.com
hxxp://pornxplayer.com
hxxp://awmproxy.net
hxxp://checkerproxy.net
Related domains known to have participated in the campaign:
hxxp://fizot.livejournal.com/
hxxp://russiaru.net/fizot/
Instant Messaging Account:
ICQ — 795781
Related personally identifiable information of Galdziev Chingiz:
hxxp://phpnow.ru
ICQ — 434929
Email: info@phpnow.ru
Related domains known to have participated in the campaign:
hxxp://filmv.net
hxxp://finance-customer.com
hxxp://firelinesecrets.com
hxxp://fllmphpxpwqeyhj.net
hxxp://flsunstate333.com
Related individuals known to have participated in the campaign:
Slavik, Monstr, IOO, Nu11, nvidiag, zebra7753, lexa_Mef, gss, iceIX, Harderman, Gribodemon, Aqua, aquaSecond, it, percent, cp01, hct, xman, Pepsi, miami, miamibc, petr0vich, Mr. ICQ, Tank, tankist, Kusunagi, Noname, Lucky, Bashorg, Indep, Mask, Enx, Benny, Bentley, Denis Lubimov, MaDaGaSka, Vkontake, rfcid, parik, reronic, Daniel, bx1, Daniel Hamza, Danielbx1, jah, Jonni, jtk, Veggi Roma, D frank, duo, Admin2010, h4x0rdz, Donsft, mary.J555, susanneon, kainehabe, virus_e_2003, spaishp, sere.bro, muddem, mechan1zm, vlad.dimitrov, jheto2002, sector.exploits
Related Instant Messaging accounts and emails known to have participated in the campaign:
iceix@secure-jabber.biz
shwark.power.andrew@gmail.com
johnlecun@gmail.com
gribodemon@pochta.ru,
glazgo-update-notifier@gajim.org
gribo-demon@jabber.ru
aqua@incomeet.com
miami@jabbluisa.com
um@jabbim.com
hof@headcounter.org
theklutch@gmail.com
niko@grad.com
Johnny@guru.bearin.donetsk.au
petr0vich@incomeet.com
mricq@incomeet.com
T4ank@ua.fm
tank@incomeet.com
getreadysafebox.ru
john.mikleymaiI.com
aIexeysafinyahoo.corn
rnoscow.berlin@yahoo.com
cruelintention@email.ru,
bind@ernail.ru
firstmen17@rarnbler.ru
benny@jabber.cz
airlord1988@gmail.com
bxl@hotmail.com
i_amhere@hotmail.fr
daniel.h.b@universityofsutton.com
princedelune@hotmail.fr
bxl_@msn.com
danibxl@hotmail.fr
danieldelcore@hotmail.com.
d.frank@jabber.jp
d.frank@0nl1ne.at
duo@jabber.cn
fering99@yahoo.com
secustar@mail.ru
h4x0rdz@hotmail.com
Donsft@hotmail.com
mary.j555@hotmail.com
susanneon@googlemail.com
kainehabe@hotmail.com
virus_e_2003@hotmail.com
spanishp@hotmail.com
sere.bro@hotmail.com
lostbuffer@hotmail.com
lostbuffer@gmail.com
vlad.dimitrov@hotmail.com
jheto2002@gmail.com
sector.exploits@gmail.com
Aleksei Belan
Sample Personal Photo of Aleksei Belan
Sample domains known to have been involved in the campaign:
Sample personally identifiable email address accounts known to have been involved in the campaign:
moy.yawik@gmail.com
moy-yawik@bk.ru
Sample known responding IPs known to have been involved in the campaign include:
77.221.159.235
62.76.182.72
62.76.190.68
185.50.25.13
104.18.41.143
198.54.117.212
104.18.40.143
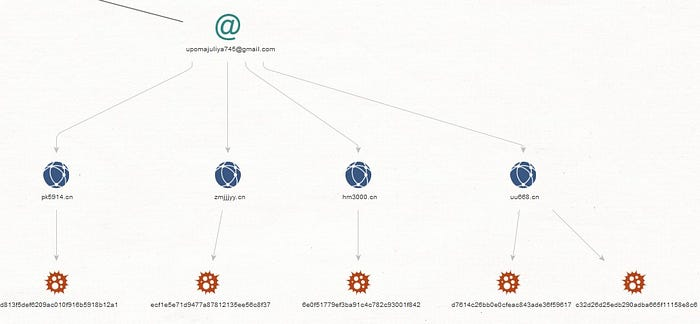
Mykhaylo Sergiyovich Rytikov
Sample Personal Photo of Mykhaylo Sergiyovich Rytikov
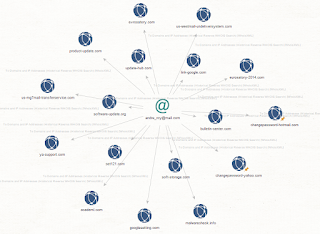
Known domains affiliated with AbdAllah Internet Hizmetleri:
hxxp://tiket[.]cc
hxxp://abdulla[.]cc
hxxp://privateforum[.]cn — upomajuliya745@gmail.com; xpj88kf@gmail.com; 316411856@qq.com
Related known domains affiliated with AbdAllah Internet Hizmetleri:
hxxp://ns1[.]srv4u[.]biz
hxxp://bulletproof-service[.]com — Email: support@hosting-offshore.biz — 202.83.212.250
hxxp://tarahost[.]net — Email: konstantin@karyaev.com — 89.108.73.93
Related domains known to have been registered by the same domain registrant:
hxxp://all-mafia[.]net
hxxp://shampanskoe[.]info
hxxp://mashost[.]org
hxxp://flexi-domains[.]com
hxxp://5pagess[.]net
hxxp://extrasoft[.]biz
hxxp://golovolomka[.]info
hxxp://optical-coatings[.]info
hxxp://polevoi[.]info
hxxp://belorussia[.]info
hxxp://3alab[.]com
hxxp://prezervativ[.]org
hxxp://brodyaga[.]net
hxxp://skramedia[.]com
hxxp://tarafree[.]com
hxxp://mp3-mmf[.]com
hxxp://myproga[.]net
hxxp://extrahost[.]su
hxxp://garanthost[.]com
hxxp://grand-host[.]net
hxxp://technormativ[.]info
hxxp://xp-hosting[.]net
hxxp://kredits[.]cn
hxxp://tarahost[.]biz
hxxp://tarahost[.]org
hxxp://optical-coatings-design[.]info
hxxp://extrasoft-outsourcing[.]info
hxxp://pm-tost[.]net
hxxp://pm-sotovik[.]net
hxxp://pm-ranlix[.]net
hxxp://pm-holland[.]net
hxxp://swlu[.]info
hxxp://valdiss[.]info
hxxp://karyaev[.]com
hxxp://x450[.]info
hxxp://grand-host[.]biz
hxxp://flexi-classifieds[.]com
hxxp://flexi-sitebuilder[.]com
hxxp://flexi-projects[.]com
hxxp://bloggast[.]info
hxxp://pereezd-pro[.]info
hxxp://eduaction[.]info
hxxp://wmnakovalnya[.]com
hxxp://retro80x[.]com
hxxp://tarafree[.]net
hxxp://skramedia[.]org
hxxp://oldactors[.]net
hxxp://tarahost[.]net
hxxp://janimation[.]net
hxxp://tarahost[.]com
hxxp://skramedia[.]biz
hxxp://vv-want[.]info
hxxp://skramedia[.]net
hxxp://olimp-sport[.]com
hxxp://youhouse[.]biz
hxxp://kroleki[.]com
hxxp://extrasoft-projects[.]info
hxxp://zelenaya[.]com
hxxp://cazinowm[.]com
hxxp://extrasoft-outsourcing[.]net
Related domains known to have been involved with AbdAllah Internet Hizmetleri:
hxxp://magic-jackpot-cas[.]com
hxxp://euro-vip-casino[.]com
hxxp://royal-casino-vip[.]com
hxxp://sexrusfuck[.]com
hxxp://royal-cas-vip[.]com
hxxp://2400-usd-casino[.]com
hxxp://royalcasino-vip[.]com
hxxp://2400usd-casino[.]net
hxxp://eurocasino-vip[.]com
hxxp://sinlife[.]cn
hxxp://byron-consulting-group[.]com
hxxp://28–07[.]com
hxxp://28–07[.]net
hxxp://job-consults[.]org
hxxp://837–86[.]org
hxxp://expressdeal[.]biz
hxxp://cron[.]li
hxxp://crons[.]cc
hxxp://cronos[.]mn
hxxp://crinc[.]mn
hxxp://crinc[.]li
hxxp://ultrasmoke[.]cn
hxxp://supersmoke[.]cn
hxxp://globalsmoke[.]cn
hxxp://937–86[.]org
hxxp://cronco[.]li
hxxp://tradegroup-ha[.]com
hxxp://ha-tradegroup[.]com
hxxp://crinc[.]jp
hxxp://tradegroup-ha[.]net
hxxp://investmentcron[.]cn
hxxp://glb-soft[.]com
hxxp://croninv[.]cc
hxxp://cronis[.]cn
hxxp://crons[.]ac
hxxp://cronn[.]eu
hxxp://dkebooks[.]com
hxxp://cronoi[.]cc
hxxp://jieod[.]com
hxxp://midgejs[.]com
hxxp://crin[.]ac
hxxp://aoejf[.]com
hxxp://yseac[.]com
hxxp://kaserid[.]com
hxxp://crin[.]cc
hxxp://jekdoe[.]com
hxxp://ujeose[.]com
hxxp://masiwer[.]com
hxxp://reusiwe[.]com
hxxp://kaoeds[.]com
hxxp://iwoser[.]com
hxxp://planet0day[.]biz
hxxp://xeirod[.]com
hxxp://neusoas[.]com
hxxp://geoepd[.]com
hxxp://efuyr[.]com
hxxp://ziude[.]com
hxxp://polsenstanford[.]com
hxxp://heyud[.]com
hxxp://woqkr[.]com
hxxp://seiudr[.]com
hxxp://aosier[.]com
hxxp://dueor[.]com
hxxp://crins[.]ac
hxxp://verbespecially[.]com
hxxp://fivejoy[.]com
hxxp://riverwomen[.]com
hxxp://trianglesentence[.]com
hxxp://floorside[.]com
hxxp://developtail[.]com
hxxp://womanfinish[.]com
hxxp://alwaysfell[.]com
hxxp://differcollect[.]com
hxxp://goodalso[.]com
hxxp://kingbrought[.]com
hxxp://findcharacter[.]com
hxxp://chanceexpect[.]com
hxxp://beardictionary[.]com
hxxp://forwardfield[.]com
hxxp://tinydown[.]com
hxxp://jobwhether[.]com
hxxp://numeralcity[.]com
hxxp://cronin[.]jp
hxxp://equalcatch[.]com
hxxp://streamwho[.]com
hxxp://selectmonth[.]com
hxxp://propercame[.]com
hxxp://grewsoil[.]com
hxxp://townslip[.]com
hxxp://stationheavy[.]com
hxxp://charactereven[.]com
hxxp://milk0soft[.]com
hxxp://goldverb[.]com
hxxp://windowlisten[.]com
hxxp://bqgqnfc[.]cn
hxxp://wrbhnuw[.]cn
hxxp://a9da6[.]org
hxxp://04ccc408[.]org
hxxp://bdb7beb6[.]org
hxxp://scalespread[.]com
hxxp://thencloud[.]com
hxxp://figurespoke[.]com
hxxp://fullfraction[.]com
hxxp://propertytall[.]com
hxxp://beautyfig[.]com
hxxp://hadover[.]com
hxxp://followsalt[.]com
hxxp://staysay[.]com
hxxp://herexcept[.]com
hxxp://thanscore[.]com
hxxp://humanthus[.]com
hxxp://branchfelt[.]com
hxxp://areacountry[.]com
hxxp://meetduring[.]com
hxxp://movestood[.]com
hxxp://stillverb[.]com
hxxp://suggesteye[.]com
hxxp://preparebut[.]com
hxxp://hurrysound[.]com
hxxp://cookcompare[.]com
hxxp://0daycod[.]biz
hxxp://europeansmoke[.]cn
hxxp://sprybog[.]net
hxxp://taybaol[.]com
hxxp://polsenstanford[.]com
hxxp://bconsgroup[.]com
GRU’s Unit 74455 “NotPetya”
Sample screenshots of the GRU’s Unit 74455 “NotPetya” malware gang obtained using public sources:
Igor Dehtyarchuk
Sample Personal Photo of Igor Dehtyarchuk
Sample emails known to have been involved in the campaign include:
abuse@shopsn.su
dimetr801@mail.ru
admin@4server.su
ssg.apple77@gmail.com
Sample domains known to have been involved in the campaign include:
hxxp://4server.su
hxxp://csgoacc.ru
hxxp://marketsales.su
hxxp://zarmo.su
hxxp://4domains.su
hxxp://ebayshop.su
hxxp://globus-base.su
hxxp://broshop.su
hxxp://deer.su
hxxp://shopsn.su
hxxp://cjmarket.net
hxxp://vkaccounts.com
hxxp://cheapaccounts.su
hxxp://ytuber.su
hxxp://vds4u.su
hxxp://4host.su
hxxp://tgshop.su
hxxp://xn — 227-qdd4dec.xn — p1acf
hxxp://4dedic.su
hxxp://time-hack.su
hxxp://4ns.su
Sample screenshot:
Oleksandr Vitalyevich Ieremenko
Sample Personal Photo of Oleksandr Vitalyevich Ieremenko
Handle: Zl0m; Lamarez; Ded.MCz; l@m@rEz
Email: lamarez@mail.ru; uaxakep@gmail.com — xeljanzusa.com — 62.109.25.228 (hxxp://www.secureworks.com/research/point-of-sale-malware-threats); 62.109.1.69
Commpany: 2016 Кзерокс
Phone: +7 951 366 17 17
ICQ: 123424
Web Money: 258807111393
Related URLs:
hxxp://ageline.ru/lamarez.php
hxxp://k0x.ru/md5.salt.tx
hxxp://k0x.ru/_bot.exe — 82.146.60.59
hxxp://k0x.ru/black_energy_31337_/stat.php
hxxp://k0x.ru/siicywu36dswh/addddos.php
hxxp://xtoolz.ru
hxxp://cup.su
hxxp://xwarez.us
hxxp://kinoafisha.ua/news/lamarez-was-here
hxxp://post-tracker.ru
hxxp://zr.ru
hxxp://business-gazeta.ru
hxxp://proshkolu.ru
hxxp://opengost.ru
hxxp://krokha.ru
hxxp://eurolab.ua
hxxp://newsdon.info
hxxp://dirt.ru
hxxp://anime-zone.ru
hxxp://rus.kg
hxxp://badger.ru
hxxp://fedpress.ru
hxxp://carsguru.net
hxxp://findfood.ru
hxxp://beboss.ru
hxxp://vidal.ru
hxxp://reghelp.ru
hxxp://rabotagrad.ru
hxxp://proshkolu.ru
hxxp://muztorg.ru
hxxp://mirf.ru
hxxp://medgorodok.ru
hxxp://dobrota.ru
hxxp://cooksa.ru
hxxp://consmed.ru
hxxp://buro247.ru
hxxp://3dmir.ru
hxxp://novorus.info
hxxp://kidbe.ru
hxxp://eknigi.org
hxxp://2×2.su
Exante LTD — XNT Ltd. — exante.eu
Danil Potekhin
Sample personal Web site: hxxp://agressivex.com
Sample personal email: potekhinl4@bk.ru
Sample MD5 known to have participated in the campaign:
MD5: ecb347518230e54c773646075e2cc5ea269dcf8304ad102cee4aae75524e4736
Happy research!
Continue reading →






































































RSS Feed