Exposing Aleksandr Zhukov from the Media Methane Rogue Fraudulent and Malicious Advertising Enterprise - An OSINT Analysis
0
Following the recent revelations and actual U.S DoJ bust and lawsuit against Aleksandr Zhukov from Media Methane responsible for the MethBrowser ad-fraud scheme I've decided to take a little bit deeper look inside its online infrastructure and actually elaborate more on the fraudulent practices applied by the group including to offer practical and relevant actionable intelligence in terms of exposing the group's online infrastructure.
Stay tuned!
In this post I'll discuss the group's online infrastructure and elaborate more on some of the key individuals behind the gang with the idea to empower the security community and U.S Law Enforcement with the necessary data and information to track down and prosecute the cybercriminals behind these campaigns.
Rogue Company Name: Media Methane
Rogue Company Product: MethBrowser
Rogue online infrastructure provider:
host1plus / DIGITAL ENERGY TECHNOLOGIES
inetnum: 179.61.128/17
inetnum: 181.41.192/19
inetnum: 181.214/15
inetnum: 191.96/16
inetnum: 191.101/16
Speed Home Internet LTD
US online LTD
Dallas online LTD
Home Internet Orang LTD
ATOL Intertnet
CH wireless
SecureShield LLC
HomeChicago Int
AmOL wireless Net
Verison Home Provider LTD
Rogue netblocks known to have been involved in the campaign:
45.33.224.0/20
45.43.128.0/21
45.43.136.0/22
45.43.140.0/23
45.43.144.0/20
45.43.160.0/19
64.137.0.0/20
64.137.16.0/21
64.137.24.0/22
64.137.30.0/23
64.137.32.0/20
64.137.48.0/21
64.137.60.0/22
64.137.64.0/18
104.143.224.0/19
104.222.160.0/19
104.233.0.0/18
104.238.0.0/19
104.239.0.0/19
104.239.32.0/20
104.239.48.0/21
104.239.56.0/23
104.239.60.0/22
104.239.64.0/18
104.243.192.0/20
104.248.0.0/16
104.249.0.0/18
104.250.192.0/19
160.184.0.0/16
161.8.128.0/17
165.52.0.0/14
168.211.0.0/16
179.61.129.0/24
179.61.137.0/24
179.61.196.0/24
179.61.202.0/24
179.61.208.0/24
179.61.216.0/24
179.61.218.0/23
179.61.229.0/24
179.61.230.0/23
179.61.233.0/24
179.61.234.0/23
179.61.237.0/24
179.61.239.0/24
179.61.242.0/24
181.41.199.0/24
181.41.200.0/24
181.41.202.0/24
181.41.204.0/24
181.41.206.0/23
181.41.208.0/24
181.41.213.0/24
181.41.215.0/24
181.41.216.0/24
181.41.218.0/24
181.214.5.0/24
181.214.7.0/24
181.214.9.0/24
181.214.11.0/24
181.214.13.0/24
181.214.15.0/24
181.214.17.0/24
181.214.19.0/24
181.214.21.0/24
181.214.23.0/24
181.214.25.0/24
181.214.27.0/24
181.214.29.0/24
181.214.31.0/24
181.214.39.0/24
181.214.41.0/24
181.214.43.0/24
181.214.45.0/24
181.214.47.0/24
181.214.49.0/24
181.214.57.0/24
181.214.71.0/24
181.214.72.0/21
181.214.80.0/21
181.214.88.0/23
181.214.94.0/23
181.214.96.0/19
181.214.160.0/21
181.214.168.0/22
181.214.172.0/23
181.214.175.0/24
181.214.176.0/20
181.214.192.0/21
181.214.200.0/22
181.214.214.0/23
181.214.216.0/21
181.214.224.0/20
181.214.240.0/22
181.215.5.0/24
181.215.7.0/24
181.215.9.0/24
181.215.11.0/24
181.215.13.0/24
181.215.15.0/24
181.215.17.0/24
181.215.19.0/24
181.215.21.0/24
181.215.23.0/24
181.215.25.0/24
181.215.27.0/24
181.215.29.0/24
181.215.31.0/24
181.215.33.0/24
181.215.35.0/24
181.215.37.0/24
181.215.39.0/24
181.215.41.0/24
181.215.43.0/24
181.215.45.0/24
181.215.47.0/24
181.215.50.0/23
181.215.52.0/22
181.215.56.0/21
181.215.64.0/20
181.215.80.0/21
188.42.0.0/21
191.96.0.0/24
191.96.16.0/24
191.96.18.0/24
191.96.21.0/24
191.96.23.0/24
191.96.29.0/24
191.96.30.0/24
191.96.39.0/24
191.96.40.0/23
191.96.43.0/24
191.96.44.0/22
191.96.50.0/23
191.96.52.0/22
191.96.56.0/22
191.96.60.0/23
191.96.62.0/24
191.96.69.0/24
191.96.70.0/23
191.96.72.0/23
191.96.74.0/24
191.96.76.0/22
191.96.80.0/21
191.96.88.0/22
191.96.92.0/24
191.96.94.0/24
191.96.96.0/23
191.96.108.0/23
191.96.110.0/24
191.96.113.0/24
191.96.114.0/24
191.96.116.0/23
191.96.119.0/24
191.96.120.0/23
191.96.122.0/24
191.96.124.0/22
191.96.133.0/24
191.96.134.0/24
191.96.138.0/24
191.96.140.0/24
191.96.145.0/24
191.96.148.0/24
191.96.150.0/24
191.96.152.0/21
191.96.160.0/22
191.96.164.0/24
191.96.168.0/24
191.96.170.0/24
191.96.172.0/24
191.96.174.0/24
191.96.177.0/24
191.96.178.0/23
191.96.182.0/24
191.96.185.0/24
191.96.186.0/23
191.96.189.0/24
191.96.190.0/24
191.96.193.0/24
191.96.194.0/24
191.96.196.0/22
191.96.200.0/23
191.96.203.0/24
191.96.210.0/24
191.96.212.0/23
191.96.214.0/24
191.96.221.0/24
191.96.222.0/23
191.96.226.0/23
191.96.232.0/24
191.96.234.0/23
191.96.236.0/23
191.96.239.0/24
191.96.244.0/24
191.96.246.0/24
191.101.25.0/24
191.101.36.0/22
191.101.40.0/21
191.101.128.0/22
191.101.132.0/23
191.101.134.0/24
191.101.146.0/23
191.101.148.0/23
191.101.176.0/23
191.101.182.0/24
191.101.184.0/22
191.101.188.0/23
191.101.192.0/22
191.101.196.0/23
191.101.204.0/22
191.101.216.0/22
191.101.220.0/24
191.101.222.0/23
196.62.0.0/16
204.52.96.0/20
204.52.112.0/22
204.52.116.0/23
204.52.120.0/23
204.52.122.0/24
204.52.124.0/22
206.124.104.0/21
209.192.128.0/19
216.173.64.0/18
Rogue domains known to have been involved in the campaign:
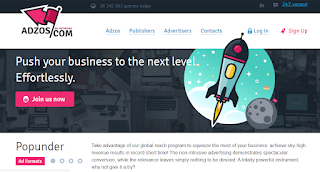
adzos.com
clickandia.com
webvideocore.com
clickservers.net
clickmediallc.net
mobapptrack.com
rtbclick.net
xmlsearchresult.com
Sample personal email address accounts known to have been involved in the campaign:
adw0rd.yandex.ru@gmail.com
clickandia@yahoo.com
Rogue Facebook profiles belonging to company employees include:
https://www.facebook.com/oleksandr.beletskyi
https://www.facebook.com/rowan.villaluz
















0 Comments: