I've decided to resume posting posts part of my upcoming blog post series called "In Retrospective" where my aim is to share interesting findings from across the cybercrime ecosystem in the context of new malicious software releases and various other cybercrime ecosystem underground market propositions with the idea to offer a unique peek inside today's modern cybercrime ecosystem.
Case in point is the Anthena DDoS bot which as a variety of unique features and should be considered a quite recent release in the context of having users buy it and actually use it to build botnets and launch new DDoS attacks against their victims.
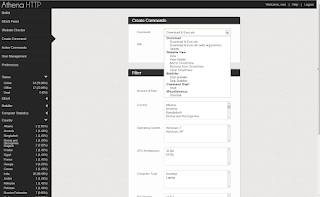
Sample screenshot of the malicious software in action:
It should be fairly easy to conclude that every time the bad guys launch a new DDoS bot on the market the actual lifecycle of the malicious software release is prone to grow and extend to the point where it's lifecycle is proportion with the general availability of new features including various ways in which antivirus solutions might fail to detect the new malicious software release including possibly a well documented source code which could be offered for sale potentially improving the lifecycle of the malicious software including the actual introduction of new features courtesy of third-parties which also include the general public including malicious software authors who might be interested in possibly introducing new features largely thanks to a publicly accessible source code.

About Dancho Danchev
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com








0 Comments: