A New DIY Grim Android Botnet Spotted in the Wild
0 I just came across to a newly released DIY Android Botnet with some pretty interesting built-in features including the use of mobile-based ransomware device locking capability including to offer the attacker the capability to take full control of the Android device for various purposes.
I just came across to a newly released DIY Android Botnet with some pretty interesting built-in features including the use of mobile-based ransomware device locking capability including to offer the attacker the capability to take full control of the Android device for various purposes.Sample screenshots:
Sample description:
Sending SMS.
Launch USSD.
Application launch.
Change URL admin panel/Redirect.
Get all SMS.
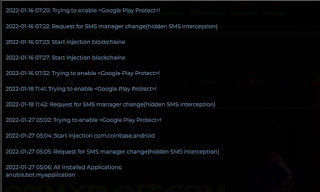
Get all installed apps.
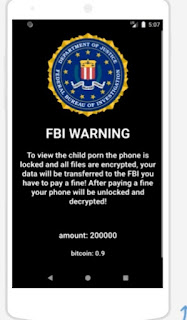
Launch Fake- Locker .
Getting Keyloggera logs.
Getting numbers from the phone book.
Send SMS to your contacts.
Enable Ransomware
Turn off Ransomware
Automatic display of PUSH Notifications.
Show PUSH Notification.
Launch SMS spam.
SMS interception.
Hidden interception of SMS.
Show message box.
Get a list of received permissions.
Request permissions for injections.
Request permissions for Geolocations.
Launch RAT/VNC.
Microphone recording.
View/Manage the File System.
Follow the screen.
Request all rights
Start call forwarding.
Stop call forwarding.
Open link in browser.
Open hidden link in browser.
Delete application.
Launch SOSKS5.
Stop SOSKS5.
Get the bot’s IP.
Enable PUSH.
Disable PUSH.
Auto-delete applications.
Smart lock function.
Works on all versions from 5 to 10.
Hidden SMS interception works from 5 to above.
Injections work on all current versions 5 – 10.
The data between the servers and the bot is encrypted.
Bot deletion blocking.
Lock disabling rights.
Blocking the disablement of the Accessibility Service.
May have several spare domains, for otstuk.
About 600+ injections for all countries/banks/cryptocurrency
Disables Play Protect. Once disabled, it cannot be enabled.
The unique identifier of the bot.
ANDROID version/Smartphone name.
Picture marking.
Country + language that is set in the settings.
The last retreat.
Status of Google Play Protect.
Screen status on/off.
Injection rights state.
Status of the Accessibility Service.
Status of covert interception of SMS.
Status of permissions for geolocations.
Availability of bank logs, mail cards.
List of established banks.
Device IP.
The date the device was infected.
Operator.
phone activity.
Bot time.
The cost of bot licenses.
1 month – $ 500
3 months – $ 1000
12 months – $ 3000








0 Comments: