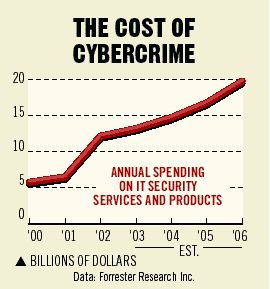
 At the end of 2005, a rather contradictive statement was made, namely, that the costs of cybercrime
have surpassed those of drug smuggling? And while I feel it has been
made in order to highlight the threats posed by today's cyber
insecurities, I find it a bit of an unrealistic one.
At the end of 2005, a rather contradictive statement was made, namely, that the costs of cybercrime
have surpassed those of drug smuggling? And while I feel it has been
made in order to highlight the threats posed by today's cyber
insecurities, I find it a bit of an unrealistic one.Mainly because of :
- the lack of centralized database and approach to keep track of, and measure the costs of cyber crime
Centralization is useful sometimes, and so is standardization. My point is that, doesn't matter how many metrics I go through on a monthly basis. They all have had different approaches while gathering their data. Estimated or projected loses are a tricky thing the way Donald Trump's valuation is largely based on his name brand. In this very same way, if we were to quantify the losses of a worldwide worm outbreak posed by direct attacks of the availability and integrity of networks and hosts, it would always be rather unrealistic, yet hopefully scientifically justified to a certain extend!
I feel it's about time the industry appoints a watchdog with an in-depth understanding of the concept. A watchdog that has the open source intelligence attitude, and the law enforcement backup to diffentiate online identity theft next to dumpest diving, and both, soft and hard dollar losses out of an event.
- the flawed approaches towards counting the TOC costs
"We had out network hit by a worm attack, where 200 out of 1000 desktops got successfully infected resulting in 4 hours downtime of the 200 desktops, and with the department's $15 hourly rate it resulted in direct loss of productivity." Rather common approach these days, what isn't included is the time the IT/Security department spent fixing the problem, the eventually
increased infosec budget (given the department takes advantage of the momentum and asks for more), and and potential law suits that may follow by other companies whose systems have been attacked by any of the 200 infected ones. A security incident shouldn't be isolated when it comes to costs, yet it's the best approach to bring some accountability, though, it's totally unrealistic. The butterfly effect has its word in both the real, and the financial world as well.
- the hard to quantify intellectual property theft
Continuing my thoughts from the abovementioned opinion, if we were to count the IT/Security department's associated costs, as well as the loss of productivity next to the hourly rate, especially when there's been a theft of intellectual property is easy, yet, untrue. If we were to
even estimate the potential dollar losses of intellectual property theft due to security breaches, it would surpass the U.S budget's deficit and reach levels of a developing economy's GDP, I bet that! The current inability of the industry to successfully quantify the costs of intellectual property theft, results in a mare estimation of the real costs of the cyber crime act. In this case, it's more complex that some want to believe.
- lack of disclosure enforcement
More and more states(U.S only, painfully true but the world is lacking behind) are adopting breach disclosure laws with the idea to prevent successful use of the information, seek accountability from the organizations/enterprises, and, hopefully result in even more clear metrics on what exactly is going on in the wild. However, the lack of acceptance, and sometimes,
even the awareness of being hacked is resulting into the highly underestimated, and actual picture in respect to the real state of cyber crime today. The more disclosure enforcement, and actual awareness of the breaches, the better the metrics, understanding of where the threats are going, and accountability for the organizations themselves.
- survey and metrics should always be a subject to question
The way a research company gathers survey and metrics data should always be a subject to questions. Even highly respected law enforcement agencies surveys and research, clearly indicate similarities, though when it comes to financial losses, every organization has a different measurement approaches and understanding of the concept. That is why, in the majority of cases, they aren't even aware of the actual long-term, or soft dollar losses directly posed by a single security breach. Evaluating assets, and assigning dollar values to intellectual property is tricky, and it could both, provide a more realistic picture of the actual losses, or overestimate
them due ot the company "falling in love" with the intellectual value of its breached information.
- companies fearing shame do not report the most relevant events today, online extortion or DDoS attacks
No company would publicly admit complying with online extortionists, and no matter how unprofessional it may sound, a LOT of companies pay not to have their reputation damaged, and it's not just public companies I'm talking about. How should a company react in such a situation, fight back, have it's web site shut down resulting in direct $ losses outpacing the sum requested by extortionists, or complying with the request, to later on having to deal with issue again? How much value would a company gain for fighting back, or for publicly stating of having such a problem, and complying with it? What's more, should quantifying a successful DDoS attack on a E-shop also include the downtime effect for the ISP's customers, given they don't null route
the site of course? And who's counting all these counts, and how far would their impact actually reach?
- the umatelized sales of people avoiding shopping online
A topic that is often neglected when it comes to E-commerce, is the HUGE number of people that aren't interested in participating(though they have the E-ability to do so), mainly because of the fear posed by cyber crime, having their credit card data stolen etc. The current revenues of E-commerce in my point of view, are nothing compared to what they could be given the industry's leaders gently unite in order to build awareness on their actions towards improving security. I also consider these people as a cost due to cyber crime!
At the bottom line, drug addicts don't exist because of drugs, but because of the society, and it may be easier to execute phishing attacks than smuggle cocaine from Mexico to the U.S, but this is where the real $$$ truly is from my point of view - drugzZzZzZzZ...................:)
Technorati tags :
cybercrime,security,information security,ROSI











RSS Feed