In this post, I will perform an OSINT analysis, exposing one of the key botnet masters behind the infamous Koobface botnet, that I have been extensively profiling and infiltrating since day one. I will include photos of the botnet master, his telephone numbers, multiple email addresses, license plate for a BMW, and directly connect him with the infrastructure -- now offline or migrated to a different place -- of Koobface 1.0.
The analysis is based on a single mistake that the botnet master made - namely using his personal email for registering a domain parked within Koobface's command and control infrastructure, that at a particular moment in time was directly redirecting to the ubiquitous fake Youtube page pushed by the Koobface botnet.
Let's start from the basics. Here's an excerpt from a previous research conducted on the Koobface botnet:
However, what the Koobface gang did was to register a new domain and use it as Koobface C&C again parked at the same IP, which remains active - zaebalinax.com Email: krotreal@gmail.com - 78.110.175.15 - in particular zaebalinax.com/the/?pid=14010 which is redirecting to the Koobface botnet. Two more domains were also registered and parked there, u15jul .com and umidsummer .com - Email: 2009polevandrey@mail.ru which remain in stand by mode at least for the time being.
The Koobface botnet master's biggest mistake is using the Koobface infrastructure for hosting a domain that was registered with the botnet master's personal email address. In this case that zaebalinax.com and krotreal@gmail.com. zaebalinax.com is literally translated to "Gave up on Linux". UPDATED: Multiple readers have to contacted me to point out that zaebalinax is actually translated to "f*ck you all" or "you all are p*ssing me off".
The same email krotreal@gmail.com was used to advertise the sale of Egyptian Sphynx kittens on 05.09.2007:
The following telephone belonging to Anton was provided - +79219910190. The interesting part is that the same telephone was also used in another advertisement, this time for the sale of a BMW:
Photos of the BMW, offered for sale, by the same Anton that was using the Koobface infrastructure to host zaebalinax.com Email: krotreal@gmail.com:
Upon further analysis, it becomes evident that his real name is Anton Nikolaevich Korotchenko (Антон Николаевич Коротченко). Here are more details of this online activities:
Real name: Anton Nikolaevich Korotchenko (Антон Николаевич Коротченко)
City of origin: St. Petersburg
Primary address: Omskaya st. 26-61; St. Petersburg; Leningradskaya oblast,197343
Associated phone numbers obtained through OSINT analysis, not whois records:
+79219910190
+380505450601
050-545-06-01
ICQ - 444374
Emails: krotreal@yahoo.com
krotreal@gmail.com
krotreal@mail.ru
krotreal@livejournal.com
newfider@rambler.ru
WM identification (WEB MONEY) : 425099205053
Twitter account: @KrotReal; @Real_Koobface
Flickr account: KrotReal
Vkontakte.ru Account: KrotReal; tonystarx
Foursquare Account: KrotReal
Also, a chat log from 2003, identifies KrotReal while he's using the following IP - krotreal@ip-534.dialup.cl.spb.ru
How do you trigger a change that would ultimately affect the entire cybercrime ecosystem? By personalizing cybercrime.
Go through previous research conducted on the Koobface botnet:
Koobface Redirectors and Scareware Campaigns Now Hosted in Moldova
The Koobface Gang Wishes the Industry "Happy Holidays"
Koobface Gang Responds to the "10 Things You Didn't Know About the Koobface Gang Post"
10 things you didn't know about the Koobface gang
How the Koobface Gang Monetizes Mac OS X Traffic
Koobface Botnet's Scareware Business Model - Part Two
Koobface Botnet's Scareware Business Model
From the Koobface Gang with Scareware Serving Compromised Site
Koobface Botnet Starts Serving Client-Side Exploits
Koobface-Friendly Riccom LTD - AS29550 - (Finally) Taken Offline
Dissecting Koobface Gang's Latest Facebook Spreading Campaign
Koobface - Come Out, Come Out, Wherever You Are
Dissecting Koobface Worm's Twitter Campaign
Koobface Botnet Redirects Facebook's IP Space to my Blog
Koobface Botnet Dissected in a TrendMicro Report
Massive Scareware Serving Blackhat SEO, the Koobface Gang Style
Movement on the Koobface Front - Part Two
Movement on the Koobface Front
Dissecting the Koobface Worm's December Campaign
The Koobface Gang Mixing Social Engineering Vectors
Dissecting the Latest Koobface Facebook Campaign
In the overwhelming sea of information, access to timely, insightful and independent open-source intelligence (OSINT) analyses is crucial for maintaining the necessary situational awareness to stay on the top of emerging security threats. This blog covers trends and fads, tactics and strategies, intersecting with third-party research, speculations and real-time CYBERINT assessments, all packed with sarcastic attitude
Monday, October 31, 2011
Exposing the Market for Stolen Credit Cards Data
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Thursday, October 20, 2011
Dissecting the Ongoing Mass SQL Injection Attack
The ongoing mass SQL injection attack, has already affected over a million web sites. Cybercriminals performing active search engines reconnaissance have managed to inject a malicious script into ASP ASP.NET websites.
From client-side exploits to bogus Adobe Flash players, the campaign is active and ongoing. In this intelligence brief, we'll dissect the campaign and establish a direct connection between the campaign and last March's Lizamoon mass SQL injection attack.
SQL injected domains -- thanks to Dasient's Tufan Demir for the ping:
nbnjki.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
jjghui.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookzula.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookgusa.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
dfrgcc.com/ur.php - Email: jamesnorthone@hotmailbox.com
statsl.com/ur.php - 111.22.111.111 - Email: jamesnorthone@hotmailbox.com
milapop.com/ur.php - Email: jamesnorthone@hotmailbox.com
jhgukn.com/ur.php - Email: jamesnorthone@hotmailbox.com
vovmml.com/ur.php - Email: jamesnorthone@hotmailbox.com
bookvivi.com/ur.php - Email: jamesnorthone@hotmailbox.com
Responding to 146.185.248.3 is also file-dl.com; bookfula.com and bookvila.com - Email: jamesnorthone@hotmailbox.com
Detection rate for urchin.js:
urchin.js - Trojan.JS.Redirector - 17/42 (40.5%)
MD5 : 4387f9be5af4087d21c4b44b969a870f
SHA1 : 8a47842ccf6d642043ee8db99d0530336eef6b99
SHA256: 975e62fe1d9415b9fa06e8f826f776ef851bd030c2c897bc3fbee207519f8351
The redirections take place as follows:
- bookzula.com/ur.php -> www3.topasarmy.in/?w4q593n= - Email: bill.swinson@yahoo.com -> firstrtscaner.rr.nu
- nbnjkl.com/urchin.js -> power-wfchecker.in/?1dlia916= - Email: bill.swinson@yahoo.com
uberble-safe.in
uberate-safe.in
best-jsentinel.in
topantivir-foru.in
personalscannerlg.in
rideusfor.in
hardbsy-network.in
enablesecureum.in
hardynauchecker.in
best-jsentinel.in
smartklhdefense.in
smartaasecurity.in
personal-scan-4u.in
unieve-safe.in
safe-solutionsoft.in
hugeble-cure.in
topsecuritykauu.in
personalcleansoft.in
powerscanercis.in
topksfsecurity.in
hard-antivirbjb.in
strong-guardbxz.in
smart-suiteguard.in
thebestkrearmy.in
smart-guardianro.in
freeopenscanerpo.in
best-networkqjo.in
hard-antivirbjb.in
smartantivir-scanner.in
most-popularsoftcontent.in
bester-msecuriity.in
doneahme.in
strong-checkerwrt.in
safepowerforu.in
safe-securityarmy.in
personal-bpsentinel.in
personalcleansoft.in
ostestsystemri.in
saveinternet-guard.in
just-perfectprotection.in
firstholdermvq.in
just-perfectprotection.in
allcle-safe.in
brawaidme.in
uniind-safe.in
moreaz-fine.in
trueeox-safe.in
safexanet.in
personal-internet-foryou.in
For the time being, the campaing is redirecting to a fake YouTube page enticing users into downloading a bogus Adobe Flash player in order to view the video.
Detection rate for the bogus Adobe Flash player:
scandisk.exe - Backdoor:Win32/Simda.A - 8/43 (18.6%)
MD5 : fb4c93935346d2d8605598535528506e
SHA1 : 0ff7ccd785c0582e33c22f9b21156929ba7abaeb
SHA256: b204586cbac1606637361dd788b691f342cb1c582d10690209a989b040dab632
Upon execution the sample phones back to:
209.212.147.141/chrome/report.html
98.142.243.64/chrome/report.html
update.19runs10q3.com - 65.98.83.115
The same phone back locations have been used in a variety of related malware -- thanks to Kaspersky's David Jacoby for the ping. For instance, in this malware sample that's also phoning back to the same URLs, we have active HOSTS file modification as follows:
See related post: Sampling Malicious Activity Inside Cybercrime-Friendly Search Engines
www.google.com.=87.125.87.99;
google.com.=87.125.87.103;
google.com.au.=87.125.87.104;
www.google.com.au.=87.125.87.147;
google.be.=77.125.87.148;
www.google.be.=77.125.87.149;
google.com.br.=77.125.87.109;
www.google.com.br.=77.125.87.150;
google.ca.=77.125.87.152;
www.google.ca.=77.125.87.153;
google.ch.=77.125.87.155;
www.google.ch.=77.125.87.158;
google.de.=77.125.87.160;
www.google.de.=77.125.87.161;
google.dk.=92.125.87.123;
www.google.dk.=92.125.87.160;
google.fr.=92.125.87.154;
www.google.fr.=92.125.87.134;
google.ie.=92.125.87.170;
www.google.ie.=92.125.87.177;
google.it.=92.125.87.173;
www.google.it.=92.125.87.147;
google.co.jp.=92.125.87.103;
www.google.co.jp.=84.125.87.147;
google.nl.=84.125.87.103;
www.google.nl.=84.125.87.147;
google.no.=84.125.87.103;
www.google.no.=84.125.87.147;
google.co.nz.=84.125.87.103;
www.google.co.nz.=84.125.87.147;
google.pl.=84.125.87.103;
www.google.pl.=64.125.87.147;
google.se.=64.125.87.103;
www.google.se.=64.125.87.147;
google.co.uk.=64.125.87.103;
www.google.co.uk.=64.125.87.147;
google.co.za.=64.125.87.103;
www.google.co.za.=64.125.87.147;
www.google-analytics.com.=64.125.87.101;
www.bing.com.=92.123.68.97;
search.yahoo.com.=72.30.186.249;
www.search.yahoo.com.=72.30.186.249;
uk.search.yahoo.com.=87.248.112.8;
ca.search.yahoo.com.=100.6.239.84;
de.search.yahoo.com.=87.248.112.8;
fr.search.yahoo.com.=87.248.112.8;
au.search.yahoo.com.=87.248.112.8;
ad-emea.doubleclick.net.=64.125.87.101;
www.statcounter.com.=64.125.87.101;
The Lizamoon mass SQL injection connection
The same email used to register the SQL injected domains jamesnorthone@hotmailbox.com has been used to register the Lizamoon mass SQL injection attack domains extensively profiled here - "Dissecting the Massive SQL Injection Attack Serving Scareware".
Related posts:
- SQL Injection Through Search Engines Reconnaissance
- Massive SQL Injections Through Search Engine's Reconnaissance - Part Two
- Massive SQL Injection Attacks - the Chinese Way
- Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
- GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
- Dissecting the WordPress Blogs Compromise at Network Solutions
- Yet Another Massive SQL Injection Spotted in the Wild
- Smells Like a Copycat SQL Injection In the Wild
- Fast-Fluxing SQL Injection Attacks
- Obfuscating Fast-fluxed SQL Injected Domains
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Dissecting the Ongoing Mass SQL Injection Attack
The ongoing mass SQL injection attack, has already affected over a million web sites. Cybercriminals performing active search engines reconnaissance have managed to inject a malicious script into ASP ASP.NET websites.
From client-side exploits to bogus Adobe Flash players, the campaign is active and ongoing. In this intelligence brief, we'll dissect the campaign and establish a direct connection between the campaign and last March's Lizamoon mass SQL injection attack.
SQL injected domains -- thanks to Dasient's Tufan Demir for the ping:
nbnjki.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
jjghui.com/urchin.js - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookzula.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
bookgusa.com/ur.php - 146.185.248.3 - Email: jamesnorthone@hotmailbox.com
dfrgcc.com/ur.php - Email: jamesnorthone@hotmailbox.com
statsl.com/ur.php - 111.22.111.111 - Email: jamesnorthone@hotmailbox.com
milapop.com/ur.php - Email: jamesnorthone@hotmailbox.com
jhgukn.com/ur.php - Email: jamesnorthone@hotmailbox.com
vovmml.com/ur.php - Email: jamesnorthone@hotmailbox.com
bookvivi.com/ur.php - Email: jamesnorthone@hotmailbox.com
Responding to 146.185.248.3 is also file-dl.com; bookfula.com and bookvila.com - Email: jamesnorthone@hotmailbox.com
Detection rate for urchin.js:
urchin.js - Trojan.JS.Redirector - 17/42 (40.5%)
MD5 : 4387f9be5af4087d21c4b44b969a870f
SHA1 : 8a47842ccf6d642043ee8db99d0530336eef6b99
SHA256: 975e62fe1d9415b9fa06e8f826f776ef851bd030c2c897bc3fbee207519f8351
The redirections take place as follows:
- bookzula.com/ur.php -> www3.topasarmy.in/?w4q593n= - Email: bill.swinson@yahoo.com -> firstrtscaner.rr.nu
- nbnjkl.com/urchin.js -> power-wfchecker.in/?1dlia916= - Email: bill.swinson@yahoo.com
uberble-safe.in
uberate-safe.in
best-jsentinel.in
topantivir-foru.in
personalscannerlg.in
rideusfor.in
hardbsy-network.in
enablesecureum.in
hardynauchecker.in
best-jsentinel.in
smartklhdefense.in
smartaasecurity.in
personal-scan-4u.in
unieve-safe.in
safe-solutionsoft.in
hugeble-cure.in
topsecuritykauu.in
personalcleansoft.in
powerscanercis.in
topksfsecurity.in
hard-antivirbjb.in
strong-guardbxz.in
smart-suiteguard.in
thebestkrearmy.in
smart-guardianro.in
freeopenscanerpo.in
best-networkqjo.in
hard-antivirbjb.in
smartantivir-scanner.in
most-popularsoftcontent.in
bester-msecuriity.in
doneahme.in
strong-checkerwrt.in
safepowerforu.in
safe-securityarmy.in
personal-bpsentinel.in
personalcleansoft.in
ostestsystemri.in
saveinternet-guard.in
just-perfectprotection.in
firstholdermvq.in
just-perfectprotection.in
allcle-safe.in
brawaidme.in
uniind-safe.in
moreaz-fine.in
trueeox-safe.in
safexanet.in
personal-internet-foryou.in
For the time being, the campaing is redirecting to a fake YouTube page enticing users into downloading a bogus Adobe Flash player in order to view the video.
Detection rate for the bogus Adobe Flash player:
scandisk.exe - Backdoor:Win32/Simda.A - 8/43 (18.6%)
MD5 : fb4c93935346d2d8605598535528506e
SHA1 : 0ff7ccd785c0582e33c22f9b21156929ba7abaeb
SHA256: b204586cbac1606637361dd788b691f342cb1c582d10690209a989b040dab632
Upon execution the sample phones back to:
209.212.147.141/chrome/report.html
98.142.243.64/chrome/report.html
update.19runs10q3.com - 65.98.83.115
The same phone back locations have been used in a variety of related malware -- thanks to Kaspersky's David Jacoby for the ping. For instance, in this malware sample that's also phoning back to the same URLs, we have active HOSTS file modification as follows:
See related post: Sampling Malicious Activity Inside Cybercrime-Friendly Search Engines
www.google.com.=87.125.87.99;
google.com.=87.125.87.103;
google.com.au.=87.125.87.104;
www.google.com.au.=87.125.87.147;
google.be.=77.125.87.148;
www.google.be.=77.125.87.149;
google.com.br.=77.125.87.109;
www.google.com.br.=77.125.87.150;
google.ca.=77.125.87.152;
www.google.ca.=77.125.87.153;
google.ch.=77.125.87.155;
www.google.ch.=77.125.87.158;
google.de.=77.125.87.160;
www.google.de.=77.125.87.161;
google.dk.=92.125.87.123;
www.google.dk.=92.125.87.160;
google.fr.=92.125.87.154;
www.google.fr.=92.125.87.134;
google.ie.=92.125.87.170;
www.google.ie.=92.125.87.177;
google.it.=92.125.87.173;
www.google.it.=92.125.87.147;
google.co.jp.=92.125.87.103;
www.google.co.jp.=84.125.87.147;
google.nl.=84.125.87.103;
www.google.nl.=84.125.87.147;
google.no.=84.125.87.103;
www.google.no.=84.125.87.147;
google.co.nz.=84.125.87.103;
www.google.co.nz.=84.125.87.147;
google.pl.=84.125.87.103;
www.google.pl.=64.125.87.147;
google.se.=64.125.87.103;
www.google.se.=64.125.87.147;
google.co.uk.=64.125.87.103;
www.google.co.uk.=64.125.87.147;
google.co.za.=64.125.87.103;
www.google.co.za.=64.125.87.147;
www.google-analytics.com.=64.125.87.101;
www.bing.com.=92.123.68.97;
search.yahoo.com.=72.30.186.249;
www.search.yahoo.com.=72.30.186.249;
uk.search.yahoo.com.=87.248.112.8;
ca.search.yahoo.com.=100.6.239.84;
de.search.yahoo.com.=87.248.112.8;
fr.search.yahoo.com.=87.248.112.8;
au.search.yahoo.com.=87.248.112.8;
ad-emea.doubleclick.net.=64.125.87.101;
www.statcounter.com.=64.125.87.101;
The Lizamoon mass SQL injection connection
The same email used to register the SQL injected domains jamesnorthone@hotmailbox.com has been used to register the Lizamoon mass SQL injection attack domains extensively profiled here - "Dissecting the Massive SQL Injection Attack Serving Scareware".
Related posts:
- SQL Injection Through Search Engines Reconnaissance
- Massive SQL Injections Through Search Engine's Reconnaissance - Part Two
- Massive SQL Injection Attacks - the Chinese Way
- Cybercriminals SQL Inject Cybercrime-friendly Proxies Service
- GoDaddy's Mass WordPress Blogs Compromise Serving Scareware
- Dissecting the WordPress Blogs Compromise at Network Solutions
- Yet Another Massive SQL Injection Spotted in the Wild
- Smells Like a Copycat SQL Injection In the Wild
- Fast-Fluxing SQL Injection Attacks
- Obfuscating Fast-fluxed SQL Injected Domains
Tags:
Blackhat SEO,
Botnet,
Fake Adobe Flash Player,
Fake Security Software,
Hacking,
Information Security,
Lizamoon,
Malicious Software,
Scareware,
Search Engine Optimization,
Security,
SQL Injection
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, October 18, 2011
Spamvertised IRS-themed "Last Notice" Emails Serving Malware
Cybercriminals are once again impersonating the Internal Revenue Service (IRS) for malware-serving purposes. In this intelligence brief, we'll dissect the malware campaign.
Spamvertised attachment: IRS_Calculations_#ID6749.zip
Spamvertised message: Notice, There are arrears reckoned on your account over a period of 2010-2011 year. You will find all calculations according to your financial debt, enclosed. You have to pay out the debt by the 17 December 2011. Yours sincerely, IRS.
- Detection rate:
IRS_Calculations.exe - W32/Yakes.B!tr - 34/40 (85.0%)
MD5 : e44eb03582f030d30251e6be384f6b32
SHA1 : eaa3d76534d247d04987b8950965d0142d770b29
SHA256: 18386f49580298eee73688ce5e626a9e332886c25403a991495e0a3250c53e32
Upon execution phones back to:
bitgale.com/404.php?type=stats&affid=574&subid=01&iruns - 31.44.184.42; AS15884 - Email: davidsiddins@gxmailbox.com
shbsharri.com/arkivi_files/574-01.exe - returns "Bandwidth Limit Exceeded" - 74.55.50.202; AS21844 - Email: contact@privacyprotect.org
shbsharri.com/arkivi_files/setup.exe - returns "Bandwidth Limit Exceeded"
shbsharri.com/arkivi_files/sl16.exe - returns "Bandwidth Limit Exceeded"
shbsharri.com/arkivi_files/sssss.exe - returns "Bandwidth Limit Exceeded"
gansgansgroup.ru/true/index.php?cmd=getgrab - Connect to 91.229.90.139 on port 80 ... failed
gansgansgroup.ru/true/index.php?cmd=getproxy - Connect to 91.229.90.139 on port 80 ... failed
gansgansgroup.ru/true/index.php?cmd=getload&login=4117AF14E694E469C&sel=donat&ver=5.1&bits=0&file=1&run=ok
gansgansgroup.ru/true/index.php?cmd=getsocks&login=4117AF14E694E469C&port=11925
gansgansgroup.ru - 91.229.90.139; AS6753 (responding to 91.229.90.139 is also falcononfly2006.ru - Email: makrogerhouse@yandex.ru) - Email: gansgansgroup.ru@allperson.ru
The same email makrogerhouse@yandex.ru, has been linked to a previously spamvertised IRS-themed malware campaign.
Clearly, both campaigns have been launched by the same cybercriminal.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Sunday, October 09, 2011
Spamvertised "IRS notice" Serving Malware
Cybercriminals are spamvertising yet another malware-serving campaign. Impersonating the IRS, malicious attackers are attempting to entice end users into downloading and executing a malicious file attachment.
Spamvertised message: Tax notice, There are arrears reckoned on your account over a period of 2010-2011 year. You will find all calculations according to your financial debt, enclosed. Sincerely, Internal Revenue Service
Detection rate:
Calculations.exe - TrojanDownloader:Win32/Dofoil.D - 33/43 (76.7%)
MD5 : 178bb562d9c0ef2b0a87467dcbd945ee
SHA1 : 9ef75146aeb27102a1e5662284f369a43144225c
SHA256: d1551934d60033c871b377015c8be65d608b33543f149369d1e70361e06dc05e
Upon execution, it phones back to falcononfly2006.ru/blog/task.php?bid=2bfc680038ba2be7&os=5-1-2600&uptime=0&rnd=150156
falcononfly2006.ru - 91.229.90.139, AS6753 - Email: makrogerhouse@yandex.ru
makrogerhouse@yandex.ru is also associated with the following domains:
diamondexchange2011.ru
philippinemoney2011.ru
Bedownloader2011.ru
dolcekomarenoro2011.ru
forsalga102.ru
runescapegpge2011.ru
yomwarayom2001.ru
philippinemoney2011.ru
moneymgmt2011.ru
moneykeep2011.ru
firewallmakeover.ru
czechmoney2011.ru
communityspace2911.ru
brazilianmoney2011.ru
Monitoring of the campaign is ongoing.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, October 04, 2011
Spamvertised "NACHA security nitification" Serving Malware - Historical OSINT
The following intelligence brief will offer historical OSINT on the "NACHA security nitification" -- the typo is intentionally left as this is how the original campaign was spamvertised -- malware campaign.
Spamvertised body:
Dear Valued Client,We strongly believe that your account may have been compromised. Due to this, we cancelled the last ACH transactions:-(ID: 13104924)-(ID: 04804768)-(ID: 37527025)-(ID: 51633547)initiated from your bank account by you or any other person, who might have access to your account.Detailed report on initiated transactions and reasons for cancellation can be found in the attachment.
--------------------------------------------------------------------------------------------
The ACH transaction (ID: 83612541), recently sent from your bank account (by you or any other person), was rejected by the Electronic Payments Association.
###############################################
Canceled transaction
Transaction ID: 83612541
Reason of rejection See details in the report below
Transaction Report report_1409.pdf.zip (ZIP archive, Adobe PDF)
###############################################
13450 Sunrise Valley Drive, Suite 100 Herndon, VA 20171 (703) 561-1100
2011 NACHA - The Electronic Payments Association
Spamvertised attachments: report_1409.pdf.zip; Report-8764.zip
Detection rate:
Report-8764.exe - Gen:Trojan.Heur.FU.bqW@amtJU@oi - 39/43 (90.7%)
MD5 : 7c131fa05e01fc32d8f4efe53aa883d1
SHA1 : 14d52d76dd7ccc595554486027634bf8c9877036
SHA256: 1ad11c1193f0dbcae3766e5cb4094acc137c10430d615e55470cbc41ce6cd03a
Upon execution the sample phones back to:
onemoretimehi.ru/piety.exe - 188.65.208.59; 178.208.91.192 - Email: admin@onemoretimehi.ru
onemoretimehi.ru/ftp/g.php
piety.exe - MD5: 4bd87ecc4423f0bc15e229ecbf33aa2c
onemoretimehi.ru/tops.exe - MD5: f076dbc365ec7bfc438ad3c728702122; 86c7489ac539a0b57a4d075e723075f0
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Summarizing ZDNet's Zero Day Posts for September
The following is a brief summary of all of my posts at ZDNet's Zero Day for September. You can subscribe to my personal RSS feed, Zero Day's main feed, or follow me on Twitter:
01. Spamvertised 'Facebook notification' leads to exploits and malware
02. Google, Mozilla and Microsoft ban the DigiNotar Certificate Authority in their browsers
03. Microsoft themed ransomware variant spotted in the wild
04. 'Man in wheelchair falls down the elevator shaft' scam spreading on Facebook
05. New ransomware variant uses false child porn accusations
06. Russian Embassy in London hit by a DDoS attack
07. uTorrent.com hacked, serving scareware
08. Bank of Melbourne Twitter account hacked, spreading phishing links
09. Malicious spam campaigns proliferating
10. Spamvertised 'We are going to sue you' emails lead to malware
11. XSS bug in Skype for iPhone, iPad allows address book theft
12. Researcher releases details on 6 SCADA vulnerabilities
13. DIY botnet kit spotted in the wild
14. New Mac OS X trojan poses as malicious PDF file
15. Survey: 60 percent of users use the same password across more than one of their online accounts
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Wednesday, September 28, 2011
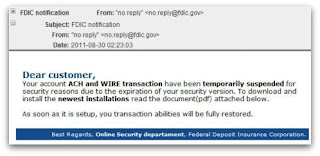
Spamvertised 'Uniform Traffic Ticket' and 'FDIC Notifications' Serving Malware - Historical OSINT
The following intelligence brief will summarize the findings from a brief analysis performed on two malware campaigns from August, namely, the spamvertised Uniform Traffic Tickets and the FDIC Notification.
_Uniform Traffic Tickets
Spamvertised attachments - Ticket-728-2011.zip; Ticket-064-211.zip; Ticket-728-2011.zip
Detection rates:
Ticket.exe - Gen:Trojan.Heur.FU.bqW@aK9ebrii - Detection rate: 37/43 (86.0%)
MD5 : 6361d4a40485345c18473f3c6b4b6609
SHA1 : 50b09bb2e0044aa139a84c2e445a56f01d70c185
SHA256: ca67a14bfed2a7bc2ac8be9c01cb17d5da12b75320b4bad4fe8d8a6759ad9725
Ticket1.exe - Trojan-Downloader.Win32.Small.ccxz - Detection rate: 36/44 (81.8%)
MD5 : e2a2d67b8a52ae655f92779bec296676
SHA1 : ed3df72b4e073ffba7174ebc8cb77b2b7d012cbf
SHA256: 50b104c5f8314327e03b01e7f7c2535d8de7cd9f73f8e16d1364c7fd021a90cc
Upon execution the samples phone back to:
sdkjgndfjnf.ru/pusk3.exe - 91.220.0.55 (responding to the same IP is also survey-providers.info) - AS51630 - Email: admin@sdkjgndfjnf.ru
rattsillis.com/ftp/g.php - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
rattsillis.com/pusk3.exe - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
DNS emulation of ns1.lemanbrostm.info reveals two domains belidiskalom.com - 178.208.76.175 - Email: admin@belidiskalom.com and lemanbrostm.info - Email: coz@yahoo.com using the same name server.
Known MD5 modifications for pusk3.exe at rattsillis.com:
c6dab856705b5dfd09b2adbe10701b05
f167213c6a79f2313995e80a8ac29939
f4764cce5c3795b1d63a299a5329d2e2
dae9e7653573478a6b41a62f7cb99c12
69c983c9dfaf37e346004c9aaf54a3d0
d875b8e32a231405c7fa96b810e9b361
628270c6e44b0fa21ef8e87c6bc36f57
9b69dabd876e967bcd2eb85465175e3b
0434c084dba8626df980c7974d5728e1
Related binaries and associated MD5 modifications:
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
rattsillis.com/pusk.exe - MD5: 55d8e25bc373a98c5c29284c989953ab; 368c86556e827d898f043a4d5f378fa0; 7411d0d29db91f2625ee36d438eb6ac4; 3ea4e9fd297b3058ebbb360c1581aaac;
rattsillis.com/pusk2.exe - MD5: dae9e7653573478a6b41a62f7cb99c12; b73705c097c9be9779730d801ad098e0; d7952c1e77d7bb250cdfa88e157fb5a8
Known MD5 modifications for pusk3.exe at sdkjgndfjnf.ru: 8672f021e7705b6a8132b7dfc21617cf
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8; ebf7278a7239378e7d70d426779962ce
sdkjgndfjnf.ru/pusk2.exe - MD5: d9e36e25a3181f574fd5d520cb501d3a
sdkjgndfjnf.ru/pusk.exe - MD5: fce04f7681283207d585561ed91e77b4
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8
Detection rate for blood.exe:
blood.exe - Trojan-Spy.Win32.Zbot - 25/44 (56.8%)
MD5 : 577cf0b7ca3d5bcbe35764024f241fa8
SHA1 : 30f542a44d06d9125cdfbdd38d79de778e4c0791
SHA256: 1741ef5d24641ee99b5d78a68109162bebc714c3d19abc37e3d4472f3dcd6f18
_FDIC Notification
Spamvertised attachments: FDIC_Document.zip
Detection rate:FDIC_Document.exe - Gen:Trojan.Heur.FU.bqW@a45Fklbi - 35/44 (79.5%)
Upon execution phones back to:
rattsillis.com/ftp/g.php
rattsillis.com/blood.exe
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
What's particularly interesting is the fact that both campaigns have been launched by the same cybercriminal, with the same C&C - rattsillis.com also seen in the spamvertised ACH Payment Canceled campaign.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
_Uniform Traffic Tickets
Spamvertised attachments - Ticket-728-2011.zip; Ticket-064-211.zip; Ticket-728-2011.zip
Detection rates:
Ticket.exe - Gen:Trojan.Heur.FU.bqW@aK9ebrii - Detection rate: 37/43 (86.0%)
MD5 : 6361d4a40485345c18473f3c6b4b6609
SHA1 : 50b09bb2e0044aa139a84c2e445a56f01d70c185
SHA256: ca67a14bfed2a7bc2ac8be9c01cb17d5da12b75320b4bad4fe8d8a6759ad9725
Ticket1.exe - Trojan-Downloader.Win32.Small.ccxz - Detection rate: 36/44 (81.8%)
MD5 : e2a2d67b8a52ae655f92779bec296676
SHA1 : ed3df72b4e073ffba7174ebc8cb77b2b7d012cbf
SHA256: 50b104c5f8314327e03b01e7f7c2535d8de7cd9f73f8e16d1364c7fd021a90cc
Upon execution the samples phone back to:
sdkjgndfjnf.ru/pusk3.exe - 91.220.0.55 (responding to the same IP is also survey-providers.info) - AS51630 - Email: admin@sdkjgndfjnf.ru
rattsillis.com/ftp/g.php - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
rattsillis.com/pusk3.exe - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
DNS emulation of ns1.lemanbrostm.info reveals two domains belidiskalom.com - 178.208.76.175 - Email: admin@belidiskalom.com and lemanbrostm.info - Email: coz@yahoo.com using the same name server.
Known MD5 modifications for pusk3.exe at rattsillis.com:
c6dab856705b5dfd09b2adbe10701b05
f167213c6a79f2313995e80a8ac29939
f4764cce5c3795b1d63a299a5329d2e2
dae9e7653573478a6b41a62f7cb99c12
69c983c9dfaf37e346004c9aaf54a3d0
d875b8e32a231405c7fa96b810e9b361
628270c6e44b0fa21ef8e87c6bc36f57
9b69dabd876e967bcd2eb85465175e3b
0434c084dba8626df980c7974d5728e1
Related binaries and associated MD5 modifications:
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
rattsillis.com/pusk.exe - MD5: 55d8e25bc373a98c5c29284c989953ab; 368c86556e827d898f043a4d5f378fa0; 7411d0d29db91f2625ee36d438eb6ac4; 3ea4e9fd297b3058ebbb360c1581aaac;
rattsillis.com/pusk2.exe - MD5: dae9e7653573478a6b41a62f7cb99c12; b73705c097c9be9779730d801ad098e0; d7952c1e77d7bb250cdfa88e157fb5a8
Known MD5 modifications for pusk3.exe at sdkjgndfjnf.ru: 8672f021e7705b6a8132b7dfc21617cf
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8; ebf7278a7239378e7d70d426779962ce
sdkjgndfjnf.ru/pusk2.exe - MD5: d9e36e25a3181f574fd5d520cb501d3a
sdkjgndfjnf.ru/pusk.exe - MD5: fce04f7681283207d585561ed91e77b4
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8
Detection rate for blood.exe:
blood.exe - Trojan-Spy.Win32.Zbot - 25/44 (56.8%)
MD5 : 577cf0b7ca3d5bcbe35764024f241fa8
SHA1 : 30f542a44d06d9125cdfbdd38d79de778e4c0791
SHA256: 1741ef5d24641ee99b5d78a68109162bebc714c3d19abc37e3d4472f3dcd6f18
_FDIC Notification
Spamvertised attachments: FDIC_Document.zip
Detection rate:FDIC_Document.exe - Gen:Trojan.Heur.FU.bqW@a45Fklbi - 35/44 (79.5%)
| MD5 : 7b5a271c58c6bb18d79cd48353127ff6 |
| SHA1 : 6526b6097df42f93bee25d7ea73f95d2fcc24d3a |
| SHA256: a09165c71a8dd2a1338b2bd0c92ae07495041ae15592e3432bd50600e6ef2af0 |
Upon execution phones back to:
rattsillis.com/ftp/g.php
rattsillis.com/blood.exe
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
What's particularly interesting is the fact that both campaigns have been launched by the same cybercriminal, with the same C&C - rattsillis.com also seen in the spamvertised ACH Payment Canceled campaign.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Spamvertised 'Uniform Traffic Ticket' and 'FDIC Notifications' Serving Malware - Historical OSINT
The following intelligence brief will summarize the findings from a brief analysis performed on two malware campaigns from August, namely, the spamvertised Uniform Traffic Tickets and the FDIC Notification.
_Uniform Traffic Tickets
Spamvertised attachments - Ticket-728-2011.zip; Ticket-064-211.zip; Ticket-728-2011.zip
Detection rates:
Ticket.exe - Gen:Trojan.Heur.FU.bqW@aK9ebrii - Detection rate: 37/43 (86.0%)
MD5 : 6361d4a40485345c18473f3c6b4b6609
SHA1 : 50b09bb2e0044aa139a84c2e445a56f01d70c185
SHA256: ca67a14bfed2a7bc2ac8be9c01cb17d5da12b75320b4bad4fe8d8a6759ad9725
Ticket1.exe - Trojan-Downloader.Win32.Small.ccxz - Detection rate: 36/44 (81.8%)
MD5 : e2a2d67b8a52ae655f92779bec296676
SHA1 : ed3df72b4e073ffba7174ebc8cb77b2b7d012cbf
SHA256: 50b104c5f8314327e03b01e7f7c2535d8de7cd9f73f8e16d1364c7fd021a90cc
Upon execution the samples phone back to:
sdkjgndfjnf.ru/pusk3.exe - 91.220.0.55 (responding to the same IP is also survey-providers.info) - AS51630 - Email: admin@sdkjgndfjnf.ru
rattsillis.com/ftp/g.php - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
rattsillis.com/pusk3.exe - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
DNS emulation of ns1.lemanbrostm.info reveals two domains belidiskalom.com - 178.208.76.175 - Email: admin@belidiskalom.com and lemanbrostm.info - Email: coz@yahoo.com using the same name server.
Known MD5 modifications for pusk3.exe at rattsillis.com:
c6dab856705b5dfd09b2adbe10701b05
f167213c6a79f2313995e80a8ac29939
f4764cce5c3795b1d63a299a5329d2e2
dae9e7653573478a6b41a62f7cb99c12
69c983c9dfaf37e346004c9aaf54a3d0
d875b8e32a231405c7fa96b810e9b361
628270c6e44b0fa21ef8e87c6bc36f57
9b69dabd876e967bcd2eb85465175e3b
0434c084dba8626df980c7974d5728e1
Related binaries and associated MD5 modifications:
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
rattsillis.com/pusk.exe - MD5: 55d8e25bc373a98c5c29284c989953ab; 368c86556e827d898f043a4d5f378fa0; 7411d0d29db91f2625ee36d438eb6ac4; 3ea4e9fd297b3058ebbb360c1581aaac;
rattsillis.com/pusk2.exe - MD5: dae9e7653573478a6b41a62f7cb99c12; b73705c097c9be9779730d801ad098e0; d7952c1e77d7bb250cdfa88e157fb5a8
Known MD5 modifications for pusk3.exe at sdkjgndfjnf.ru: 8672f021e7705b6a8132b7dfc21617cf
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8; ebf7278a7239378e7d70d426779962ce
sdkjgndfjnf.ru/pusk2.exe - MD5: d9e36e25a3181f574fd5d520cb501d3a
sdkjgndfjnf.ru/pusk.exe - MD5: fce04f7681283207d585561ed91e77b4
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8
Detection rate for blood.exe:
blood.exe - Trojan-Spy.Win32.Zbot - 25/44 (56.8%)
MD5 : 577cf0b7ca3d5bcbe35764024f241fa8
SHA1 : 30f542a44d06d9125cdfbdd38d79de778e4c0791
SHA256: 1741ef5d24641ee99b5d78a68109162bebc714c3d19abc37e3d4472f3dcd6f18
_FDIC Notification
Spamvertised attachments: FDIC_Document.zip
Detection rate:FDIC_Document.exe - Gen:Trojan.Heur.FU.bqW@a45Fklbi - 35/44 (79.5%)
Upon execution phones back to:
rattsillis.com/ftp/g.php
rattsillis.com/blood.exe
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
What's particularly interesting is the fact that both campaigns have been launched by the same cybercriminal, with the same C&C - rattsillis.com also seen in the spamvertised ACH Payment Canceled campaign.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
_Uniform Traffic Tickets
Spamvertised attachments - Ticket-728-2011.zip; Ticket-064-211.zip; Ticket-728-2011.zip
Detection rates:
Ticket.exe - Gen:Trojan.Heur.FU.bqW@aK9ebrii - Detection rate: 37/43 (86.0%)
MD5 : 6361d4a40485345c18473f3c6b4b6609
SHA1 : 50b09bb2e0044aa139a84c2e445a56f01d70c185
SHA256: ca67a14bfed2a7bc2ac8be9c01cb17d5da12b75320b4bad4fe8d8a6759ad9725
Ticket1.exe - Trojan-Downloader.Win32.Small.ccxz - Detection rate: 36/44 (81.8%)
MD5 : e2a2d67b8a52ae655f92779bec296676
SHA1 : ed3df72b4e073ffba7174ebc8cb77b2b7d012cbf
SHA256: 50b104c5f8314327e03b01e7f7c2535d8de7cd9f73f8e16d1364c7fd021a90cc
Upon execution the samples phone back to:
sdkjgndfjnf.ru/pusk3.exe - 91.220.0.55 (responding to the same IP is also survey-providers.info) - AS51630 - Email: admin@sdkjgndfjnf.ru
rattsillis.com/ftp/g.php - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
rattsillis.com/pusk3.exe - 195.189.226.109; 178.208.77.247; 195.189.226.107; 195.189.226.108 - AS41018 - Email: admin@jokelimo.com
DNS emulation of ns1.lemanbrostm.info reveals two domains belidiskalom.com - 178.208.76.175 - Email: admin@belidiskalom.com and lemanbrostm.info - Email: coz@yahoo.com using the same name server.
Known MD5 modifications for pusk3.exe at rattsillis.com:
c6dab856705b5dfd09b2adbe10701b05
f167213c6a79f2313995e80a8ac29939
f4764cce5c3795b1d63a299a5329d2e2
dae9e7653573478a6b41a62f7cb99c12
69c983c9dfaf37e346004c9aaf54a3d0
d875b8e32a231405c7fa96b810e9b361
628270c6e44b0fa21ef8e87c6bc36f57
9b69dabd876e967bcd2eb85465175e3b
0434c084dba8626df980c7974d5728e1
Related binaries and associated MD5 modifications:
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
rattsillis.com/pusk.exe - MD5: 55d8e25bc373a98c5c29284c989953ab; 368c86556e827d898f043a4d5f378fa0; 7411d0d29db91f2625ee36d438eb6ac4; 3ea4e9fd297b3058ebbb360c1581aaac;
rattsillis.com/pusk2.exe - MD5: dae9e7653573478a6b41a62f7cb99c12; b73705c097c9be9779730d801ad098e0; d7952c1e77d7bb250cdfa88e157fb5a8
Known MD5 modifications for pusk3.exe at sdkjgndfjnf.ru: 8672f021e7705b6a8132b7dfc21617cf
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8; ebf7278a7239378e7d70d426779962ce
sdkjgndfjnf.ru/pusk2.exe - MD5: d9e36e25a3181f574fd5d520cb501d3a
sdkjgndfjnf.ru/pusk.exe - MD5: fce04f7681283207d585561ed91e77b4
sdkjgndfjnf.ru/blood.exe - MD5: 577cf0b7ca3d5bcbe35764024f241fa8
Detection rate for blood.exe:
blood.exe - Trojan-Spy.Win32.Zbot - 25/44 (56.8%)
MD5 : 577cf0b7ca3d5bcbe35764024f241fa8
SHA1 : 30f542a44d06d9125cdfbdd38d79de778e4c0791
SHA256: 1741ef5d24641ee99b5d78a68109162bebc714c3d19abc37e3d4472f3dcd6f18
_FDIC Notification
Spamvertised attachments: FDIC_Document.zip
Detection rate:FDIC_Document.exe - Gen:Trojan.Heur.FU.bqW@a45Fklbi - 35/44 (79.5%)
| MD5 : 7b5a271c58c6bb18d79cd48353127ff6 |
| SHA1 : 6526b6097df42f93bee25d7ea73f95d2fcc24d3a |
| SHA256: a09165c71a8dd2a1338b2bd0c92ae07495041ae15592e3432bd50600e6ef2af0 |
Upon execution phones back to:
rattsillis.com/ftp/g.php
rattsillis.com/blood.exe
rattsillis.com/blood.exe - MD5: 23795cb9b2f5e19eff0df0cf2fba9247; 82b6f18b130a1f0ce1ce928d0980fab0
What's particularly interesting is the fact that both campaigns have been launched by the same cybercriminal, with the same C&C - rattsillis.com also seen in the spamvertised ACH Payment Canceled campaign.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
Tags:
Botnet,
FDIC,
Hacking,
Information Security,
Malicious Software,
Security,
Spam,
Spam Campaign,
Spam Operations
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Tuesday, September 27, 2011
Summarizing ZDNet's Zero Day Posts for August
The following is a brief summary of all of my posts at ZDNet's Zero Day for August. You can subscribe to my personal RSS feed, Zero Day's main feed, or follow me on Twitter:
01. Study: Rootkits target pirated copies of Windows XP
02. 56 percent of enterprise users using vulnerable Adobe Reader plugins
03. New malware attack circulating on Facebook
04. Kaspersky: 12 different vulnerabilities detected on every PC
05. Spamvertised Uniform traffic tickets and invoices lead to malware
06. Latest version of Skype susceptible to malicious code injection flaw
07. Spamvertised 'Scan from a Xerox WorkCentre Pro' leads to malware
08. Malware Watch: FDIC and Western Union themed emails lead to malware
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
01. Study: Rootkits target pirated copies of Windows XP
02. 56 percent of enterprise users using vulnerable Adobe Reader plugins
03. New malware attack circulating on Facebook
04. Kaspersky: 12 different vulnerabilities detected on every PC
05. Spamvertised Uniform traffic tickets and invoices lead to malware
06. Latest version of Skype susceptible to malicious code injection flaw
07. Spamvertised 'Scan from a Xerox WorkCentre Pro' leads to malware
08. Malware Watch: FDIC and Western Union themed emails lead to malware
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Sunday, September 11, 2011
Summarizing 3 Years of Research Into Cyber Jihad
On this very special day, I'd like to honor the fallen by summarizing my research into cyber jihad, a topic I'm still highly passionate about. Enjoy and share it with your social circle!
- Tracking Down Internet Terrorist Propaganda
- Arabic Extremist Group Forum Messages' Characteristics
- Cyber Terrorism Communications and Propaganda
- A Cost-Benefit Analysis of Cyber Terrorism
- Current State of Internet Jihad
- Analysis of the Technical Mujahid - Issue One
- Full List of Hezbollah's Internet Sites
- Steganography and Cyber Terrorism Communications
- Hezbollah's DNS Service Providers from 1998 to 2006
- Mujahideen Secrets Encryption Tool
- Analyses of Cyber Jihadist Forums and Blogs
- Cyber Traps for Wannabe Jihadists
- Inshallahshaheed - Come Out, Come Out Wherever You Are
- GIMF Switching Blogs
- GIMF Now Permanently Shut Down
- GIMF - "We Will Remain"
- Wisdom of the Anti Cyber Jihadist Crowd
- Cyber Jihadist Blogs Switching Locations Again
- Electronic Jihad v3.0 - What Cyber Jihad Isn't
- Electronic Jihad's Targets List
- Teaching Cyber Jihadists How to Hack
- A Botnet of Infected Terrorists?
- Infecting Terrorist Suspects with Malware
- The Dark Web and Cyber Jihad
- Cyber Jihadist Hacking Teams
- Two Cyber Jihadist Blogs Now Offline
- Characteristics of Islamist Websites
- Cyber Traps for Wannabe Jihadists
- Mujahideen Secrets Encryption Tool
- An Analysis of the Technical Mujahid - Issue Two
- Terrorist Groups' Brand Identities
- A List of Terrorists' Blogs
- Jihadists' Anonymous Internet Surfing Preferences
- Sampling Jihadists' IPs
- Cyber Jihadists' and TOR
- A Cyber Jihadist DoS Tool
- GIMF Now Permanently Shut Down
- Mujahideen Secrets 2 Encryption Tool Released
- Terror on the Internet - Conflict of Interest
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Monday, August 29, 2011
Keeping Money Mule Recruiters on a Short Leash - Part Eleven
The following intelligence brief is part of the Keeping Money Mule Recruiters on a Short Leash series. In it, I'll expose currently active money mule recruitment domains, their domain registration details, currently responding IPs, and related ASs.
Money mule recruitment domains:
ACWOODE-GROUP.COM - 78.46.105.205 - Email: admin@acwoode-group.com
ACWOODE-GROUP.NET - 78.46.105.205 - Email: admin@acwoode-group.net
ART-GAPSON.COM - 78.46.105.205 - Email: admin@art-gapson.com
CONDOR-LLC-UK.NET - Email: admin@condor-llc-uk.net
CONDORLLC-UK.COM - Email: plods@fxmail.net
DE-DVFGROUP.BE
ELENTY-CO.NET - Email: abcs@mailti.com
ELENTY-LLC.COM - 78.46.105.205 - Email: admin@elenty-llc.com
fabia-art.com - 209.190.4.91 - Email: adios@cutemail.org
fine-artgroup.com - 209.190.4.91
GAPSONART.NET - 78.46.105.205 - Email: admin@gapsonart.net
gmd-contracting.com - 194.242.2.56 - Email: admin@gmd-contracting.com
GURU-GROUP.CC - 78.46.105.205 - Email: admin@guru-group.cc
GURU-GROUP.NET - 78.46.105.205 - Email: jj@cutemail.org
INTECHTODEX-GROUP.COM - 78.46.105.205 - Email: uq@mail13.com
ltd-scg.net - 209.190.4.91 - Email: amykylir@yahoo.com
NARTEN-ART.COM - 78.46.105.205 - Email: glamor@fxmail.net
NARTENART.NET - 78.46.105.205 - Email: admin@nartenart.net
panart-llc.com - 78.46.105.205 - Email: admin@panart-llc.com
REFINEMENT-ANTIQUE.COM - 78.46.105.205 - Email: xe@fxmail.net
REFINEMENTUK-LTD.NET - 78.46.105.205 - Email: admin@refinementuk-ltd.net
SKYLINE-ANTIQUE.COM - 78.46.105.205 - Email: blurs@mailae.com
SKYLINE-LTD.NET - 78.46.105.205 - Email: admin@skyline-ltd.net
techce-group.com - 184.168.64.173 - Email: admin@techce-group.com
TODEX-GROUP.NET - 78.46.105.205 - Email: admin@todex-group.net
triad-webs.com - 85.17.24.226
The domains reside within the following ASs: AS24940, HETZNER-AS Hetzner Online AG RZ; AS16265, LeaseWeb B.V. Amsterdam; AS26496, GODADDY .com, Inc.; AS10297, RoadRunner RR-RC-Enet-Columbus.
Name servers of notice:
NS1.MKNS.SU - 85.25.250.244 - Email: mkns@cheapbox.ru
NS2.MKNS.SU - 46.4.148.119
NS3.MKNS.SU - 184.82.158.76
NS1.MNAMEDL.SU - 85.25.250.211 - Email: mnamed@yourisp.ru
NS2.MNAMEDL.SU - 46.4.148.118
NS3.MNAMEDL.SU - 184.82.158.75
NS1.MLDNS.SU - 85.25.145.63 - Email: mldns@free-id.ru
NS2.MLDNS.SU - 46.4.148.74
NS3.MLDNS.SU - 184.82.158.74
NS1.NAMESUKNS.CC - Email: pal@bz3.ru
NS2.NAMESUKNS.CC
NS3.NAMESUKNS.CC
NS1.NAMEUK.AT - Email: admin@nameuk.at
NS2.NAMEUK.AT
NS3.NAMEUK.AT
NS1.UKDNSTART.NET - Email: admin@ukdnstart.ne
NS2.UKDNSTART.NET
NS3.UKDNSTART.NET
Monitoring of ongoing money mule recruitment campaigns is ongoing.
Related posts:
Keeping Money Mule Recruiters on a Short Leash - Part Ten
Keeping Money Mule Recruiters on a Short Leash - Part Nine
Keeping Money Mule Recruiters on a Short Leash - Part Eight - Historical OSINT
Keeping Money Mule Recruiters on a Short Leash - Part Seven
Keeping Money Mule Recruiters on a Short Leash - Part Six
Keeping Money Mule Recruiters on a Short Leash - Part Five
The DNS Infrastructure of the Money Mule Recruitment Ecosystem
Keeping Money Mule Recruiters on a Short Leash - Part Four
Money Mule Recruitment Campaign Serving Client-Side Exploits
Keeping Money Mule Recruiters on a Short Leash - Part Three
Money Mule Recruiters on Yahoo!'s Web Hosting
Dissecting an Ongoing Money Mule Recruitment Campaign
Keeping Money Mule Recruiters on a Short Leash - Part Two
Keeping Reshipping Mule Recruiters on a Short Leash
Keeping Money Mule Recruiters on a Short Leash
Standardizing the Money Mule Recruitment Process
Inside a Money Laundering Group's Spamming Operations
Money Mule Recruiters use ASProx's Fast Fluxing Services
Money Mules Syndicate Actively Recruiting Since 2002
This post has been reproduced from Dancho Danchev's blog.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Keeping Money Mule Recruiters on a Short Leash - Part Eleven
The following intelligence brief is part of the Keeping Money Mule Recruiters on a Short Leash series. In it, I'll expose currently active money mule recruitment domains, their domain registration details, currently responding IPs, and related ASs.
Money mule recruitment domains:
ACWOODE-GROUP.COM - 78.46.105.205 - Email: admin@acwoode-group.com
ACWOODE-GROUP.NET - 78.46.105.205 - Email: admin@acwoode-group.net
ART-GAPSON.COM - 78.46.105.205 - Email: admin@art-gapson.com
CONDOR-LLC-UK.NET - Email: admin@condor-llc-uk.net
CONDORLLC-UK.COM - Email: plods@fxmail.net
DE-DVFGROUP.BE
ELENTY-CO.NET - Email: abcs@mailti.com
ELENTY-LLC.COM - 78.46.105.205 - Email: admin@elenty-llc.com
fabia-art.com - 209.190.4.91 - Email: adios@cutemail.org
fine-artgroup.com - 209.190.4.91
GAPSONART.NET - 78.46.105.205 - Email: admin@gapsonart.net
gmd-contracting.com - 194.242.2.56 - Email: admin@gmd-contracting.com
GURU-GROUP.CC - 78.46.105.205 - Email: admin@guru-group.cc
GURU-GROUP.NET - 78.46.105.205 - Email: jj@cutemail.org
INTECHTODEX-GROUP.COM - 78.46.105.205 - Email: uq@mail13.com
ltd-scg.net - 209.190.4.91 - Email: amykylir@yahoo.com
NARTEN-ART.COM - 78.46.105.205 - Email: glamor@fxmail.net
NARTENART.NET - 78.46.105.205 - Email: admin@nartenart.net
panart-llc.com - 78.46.105.205 - Email: admin@panart-llc.com
REFINEMENT-ANTIQUE.COM - 78.46.105.205 - Email: xe@fxmail.net
REFINEMENTUK-LTD.NET - 78.46.105.205 - Email: admin@refinementuk-ltd.net
SKYLINE-ANTIQUE.COM - 78.46.105.205 - Email: blurs@mailae.com
SKYLINE-LTD.NET - 78.46.105.205 - Email: admin@skyline-ltd.net
techce-group.com - 184.168.64.173 - Email: admin@techce-group.com
TODEX-GROUP.NET - 78.46.105.205 - Email: admin@todex-group.net
triad-webs.com - 85.17.24.226
The domains reside within the following ASs: AS24940, HETZNER-AS Hetzner Online AG RZ; AS16265, LeaseWeb B.V. Amsterdam; AS26496, GODADDY .com, Inc.; AS10297, RoadRunner RR-RC-Enet-Columbus.
Name servers of notice:
NS1.MKNS.SU - 85.25.250.244 - Email: mkns@cheapbox.ru
NS2.MKNS.SU - 46.4.148.119
NS3.MKNS.SU - 184.82.158.76
NS1.MNAMEDL.SU - 85.25.250.211 - Email: mnamed@yourisp.ru
NS2.MNAMEDL.SU - 46.4.148.118
NS3.MNAMEDL.SU - 184.82.158.75
NS1.MLDNS.SU - 85.25.145.63 - Email: mldns@free-id.ru
NS2.MLDNS.SU - 46.4.148.74
NS3.MLDNS.SU - 184.82.158.74
NS1.NAMESUKNS.CC - Email: pal@bz3.ru
NS2.NAMESUKNS.CC
NS3.NAMESUKNS.CC
NS1.NAMEUK.AT - Email: admin@nameuk.at
NS2.NAMEUK.AT
NS3.NAMEUK.AT
NS1.UKDNSTART.NET - Email: admin@ukdnstart.ne
NS2.UKDNSTART.NET
NS3.UKDNSTART.NET
Monitoring of ongoing money mule recruitment campaigns is ongoing.
Related posts:
Keeping Money Mule Recruiters on a Short Leash - Part Ten
Keeping Money Mule Recruiters on a Short Leash - Part Nine
Keeping Money Mule Recruiters on a Short Leash - Part Eight - Historical OSINT
Keeping Money Mule Recruiters on a Short Leash - Part Seven
Keeping Money Mule Recruiters on a Short Leash - Part Six
Keeping Money Mule Recruiters on a Short Leash - Part Five
The DNS Infrastructure of the Money Mule Recruitment Ecosystem
Keeping Money Mule Recruiters on a Short Leash - Part Four
Money Mule Recruitment Campaign Serving Client-Side Exploits
Keeping Money Mule Recruiters on a Short Leash - Part Three
Money Mule Recruiters on Yahoo!'s Web Hosting
Dissecting an Ongoing Money Mule Recruitment Campaign
Keeping Money Mule Recruiters on a Short Leash - Part Two
Keeping Reshipping Mule Recruiters on a Short Leash
Keeping Money Mule Recruiters on a Short Leash
Standardizing the Money Mule Recruitment Process
Inside a Money Laundering Group's Spamming Operations
Money Mule Recruiters use ASProx's Fast Fluxing Services
Money Mules Syndicate Actively Recruiting Since 2002
This post has been reproduced from Dancho Danchev's blog.
Tags:
Cybercrime,
Hacking,
Information Security,
Money Laundering,
Money Mule,
Money Mule Recruitment,
Security
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
A Peek Inside Web Malware Exploitation Kits
With web malware exploitation kits, continuing to represent the attack method of choice for the majority of cybercriminals thanks to the overall susceptibility of end and enterprise users to client-side exploitation attacks, it's always worth taking a peek inside them from the perspective of the malicious attacker.
In this post, we'll take a peek inside three web malware exploitation kits, and discuss what makes them think in terms of infected OSs, browser plugins and client-side exploits.
_Dragon Pack Web Malware Exploitation Kit
What we've got here is a rather modest in terms of activity, web malware exploitation kit admin panel. We've got 45 successful loads based on 588 unique visits, with the JavaRox exploit executed 42 times, successfully infecting 20 Firefox users. The exploits have successfully loaded on Windows XP 14 times, on Windows XP SP2 3 times, on Windows Vista 12 times, and on Windows 7 15 times.
_Dragon Exploit Pack
The Dragon Exploit Pack has 45 successful loads based on 587 unique visitors, with the JavaJDK exploit executed successfully 42 times. The kit is counting 13 successful loads on MSIE 8, and another 20 on Firefox, with 14 successful loads recorded for Windows XP, 2 on Windows XP SP2, 12 on Windows Vista and 15 on Windows 7.
_Katrin Exploit Pack
The Katrin Exploit Pack has 3277 successful loads based on 19933 unique visits, which represents a 17.32% infection rate. The Java JSM exploit has been successfully loaded 535 times, Java SMB has been loaded 576 times, Java OBE has been loaded 914 times, Old 4 PDF has been loaded 87 times, Libtiff PDF has been loaded 726 times, MDAC has been loaded 96 times, Snapshot has been loaded 104 times, and HCP has been loaded 239 times.
The kit is counting 452 successful exploitation attempts against MSIE 5, 786 against MSIE7, 1198 against MSIE 8, 274 against Chrome, 522 against Firefox, 24 against Opera and 14 against Safari. The majority of loads have affected Windows XP installations, with 2107 successful loads targeting the OS, following 625 on Windows Vista, and 503 on Windows 7.
_Liberty Exploit Pack
The Liberty Exploit pack screenshot, is showing the proportion successfully infected web browsers, with total of 555 successful loads based on 3029 unique visitors. 397 loads have affected Internet Explorer 6, 89 Internet Explorer 7, and 54 Firefox.
_Bleeding Life Exploit Pack
In this Bleeding Life web malware exploitation kit, we can clearly seen the dynamics behind the infections taking place. We see 554 successful loads based on 4106 unique visitors. JavaSignedApplet has been executed 161 times, Adobe-90-2010-0188 has been executed 67 times, Adobe-80-2010-0188 has been executed 46 times, Java-2010-0842 has been executed 203 times, Adobe-2008-2992 has been executed 74 times, and Adobe-2010-1297 has been executed 2 times.
The majority of the infected population is based in the U.S, United Kingdom, Qatar, and Malaysia. Windows XP has the highest market share of infected OSs, with 336 successful loads based on 2098 unique visitors. Followed by Windows 7 with 139 loads based on 1256 unique visitors, and 73 unique loads based on 719 unique visitors for Windows Vista.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
In this post, we'll take a peek inside three web malware exploitation kits, and discuss what makes them think in terms of infected OSs, browser plugins and client-side exploits.
_Dragon Pack Web Malware Exploitation Kit
What we've got here is a rather modest in terms of activity, web malware exploitation kit admin panel. We've got 45 successful loads based on 588 unique visits, with the JavaRox exploit executed 42 times, successfully infecting 20 Firefox users. The exploits have successfully loaded on Windows XP 14 times, on Windows XP SP2 3 times, on Windows Vista 12 times, and on Windows 7 15 times.
_Dragon Exploit Pack
The Dragon Exploit Pack has 45 successful loads based on 587 unique visitors, with the JavaJDK exploit executed successfully 42 times. The kit is counting 13 successful loads on MSIE 8, and another 20 on Firefox, with 14 successful loads recorded for Windows XP, 2 on Windows XP SP2, 12 on Windows Vista and 15 on Windows 7.
_Katrin Exploit Pack
The Katrin Exploit Pack has 3277 successful loads based on 19933 unique visits, which represents a 17.32% infection rate. The Java JSM exploit has been successfully loaded 535 times, Java SMB has been loaded 576 times, Java OBE has been loaded 914 times, Old 4 PDF has been loaded 87 times, Libtiff PDF has been loaded 726 times, MDAC has been loaded 96 times, Snapshot has been loaded 104 times, and HCP has been loaded 239 times.
The kit is counting 452 successful exploitation attempts against MSIE 5, 786 against MSIE7, 1198 against MSIE 8, 274 against Chrome, 522 against Firefox, 24 against Opera and 14 against Safari. The majority of loads have affected Windows XP installations, with 2107 successful loads targeting the OS, following 625 on Windows Vista, and 503 on Windows 7.
_Liberty Exploit Pack
The Liberty Exploit pack screenshot, is showing the proportion successfully infected web browsers, with total of 555 successful loads based on 3029 unique visitors. 397 loads have affected Internet Explorer 6, 89 Internet Explorer 7, and 54 Firefox.
_Bleeding Life Exploit Pack
In this Bleeding Life web malware exploitation kit, we can clearly seen the dynamics behind the infections taking place. We see 554 successful loads based on 4106 unique visitors. JavaSignedApplet has been executed 161 times, Adobe-90-2010-0188 has been executed 67 times, Adobe-80-2010-0188 has been executed 46 times, Java-2010-0842 has been executed 203 times, Adobe-2008-2992 has been executed 74 times, and Adobe-2010-1297 has been executed 2 times.
The majority of the infected population is based in the U.S, United Kingdom, Qatar, and Malaysia. Windows XP has the highest market share of infected OSs, with 336 successful loads based on 2098 unique visitors. Followed by Windows 7 with 139 loads based on 1256 unique visitors, and 73 unique loads based on 719 unique visitors for Windows Vista.
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
 Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Independent Security Consultancy, Threat Intelligence Analysis (OSINT/Cyber Counter Intelligence) and Competitive Intelligence research on demand. Insightful, unbiased, and client-tailored assessments, neatly communicated in the form of interactive reports - because anticipating the emerging threatscape is what shapes the big picture at the end of the day. Approach me at dancho.danchev@hush.com
Subscribe to:
Comments (Atom)