Following last month's "Dissecting Koobface Gang's Latest Facebook Spreading Campaign" Koobface gang coverage, it's time to summarize some of their botnet spreading activities, from the last couple of days.
Immediately after the suspension of their automatically registered Blogspot accounts, the gang once again proved that it has contingency plans in place, and started pushing links to compromises sites, in a combination with an interesting "visual social engineering trick", across Facebook, which sadly works pretty well, in the sense that it completely undermines the "don't click on links pointing to unknown sites" type of security tips.
- Recommended reading: 10 things you didn't know about the Koobface gang
This active use of the "trusted reputation chain", just like the majority of social engineering centered tactics of the gang, aim to exploit the ubiquitous weak link in the face of the average Internet user. Here's an example of the most recent campaign.
The spreading of fully working links such as the following ones across Facebook:
facebook.com/l/6e7e5;bit.ly/9QjjSk
facebook.com/l/cdfb;bit.ly/9QjjSk
facebook.com/l/f3c29;bit.ly/9QjjSk
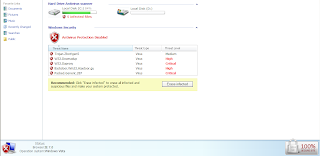
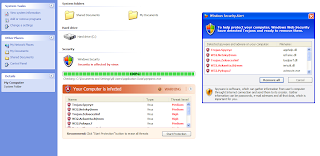
aims to trick the infected user's friends, that this is a Facebook.com related link. Clicking on this link inside Facebook leads to the "Be careful" window showing just the bit.ly redirector, to finally redirect to 198.65.28.86/swamt/ where a Koobface bogus video has already been seen by 2,601 users which have already clicked on the link.
The scareware redirectors/actual serving domains are parked at 195.5.161.126, AS31252, STARNET-AS StarNet Moldova:
1nasa-test.com - Email: test@now.net.cn
1online-test.com - Email: test@now.net.cn
1www2scanner.com - Email: test@now.net.cn
2a-scanner.com - Email: test@now.net.cn
2nasa-test.com - Email: test@now.net.cn
2online-test.com - Email: test@now.net.cn
2www2scanner.com - Email: test@now.net.cn
3a-scanner.com - Email: test@now.net.cn
3nasa-test.com - Email: test@now.net.cn
3online-test.com - Email: test@now.net.cn
3www2scanner.com - Email: test@now.net.cn
4a-scanner.com - Email: test@now.net.cn
4check-computer.com - Email: test@now.net.cn
4nasa-test.com - Email: test@now.net.cn
4online-test.com - Email: test@now.net.cn
4www2scanner.com - Email: test@now.net.cn
5a-scanner.com - Email: test@now.net.cn
5nasa-test.com - Email: test@now.net.cn
5online-test.com - Email: test@now.net.cn
6a-scanner.com - Email: test@now.net.cn
defence-status6.com - Email: test@now.net.cn
defence-status7.com - Email: test@now.net.cn
mega-scan2.com - Email: test@now.net.cn
protection-status2.com - Email: test@now.net.cn
protection-status4.com - Email: test@now.net.cn
protection-status6.com - Email: test@now.net.cn
security-status1.com - Email: test@now.net.cn
security-status3.com - Email: test@now.net.cn
security-status4.com - Email: test@now.net.cn
security-status6.com - Email: test@now.net.cn
securitystatus7.com - Email: test@now.net.cn
securitystatus8.com - Email: test@now.net.cn
securitystatus9.com - Email: test@now.net.cn
security-status9.com - Email: test@now.net.cn
Detection rates:
- setup.exe - Mal/Koobface-E; W32/VBTroj.CXNF - Result: 7/41 (17.08%)
- RunAV_312s2.exe - VirTool.Win32.Obfuscator.hg!b (v); High Risk Cloaked Malware - Result: 4/41 (9.76%)
The scareware sample phones back to:
- windows32-sys.com/download/winlogo.bmp - 91.213.157.104, AS13618 CARONET-ASN - Email: contact@privacy-protect.cn
- sysdllupdates.com/?b=312s2 - 87.98.134.197, AS16276, OVH Paris - Email: contact@privacy-protect.cn
The complete list of compromised sites distributed by Koobface-infected Facebook users:
02f32e3.netsolhost.com /o492dc/
abskupina.si /cclq/
adi-agencement.fr /8r2twm/
agilitypower.dk /ko2/
aguasdomondego.com /d5yodi/
alabasta.homeip.net /e8/
alankaye.info /2cgg/
alpenhaus.com.ar /al5zvf5/
animationstjo.fr /5c/
artwork.drayton.co.uk /k5wz/
beachfishingwa.org.au /u8g98ai/
bildtuben.se /l9jg/
chalet.se /srb/
charlepoeng.be /i0twbt/
christchurchgastonia.org /1hkq/
chunkbait.com /gb4i6ak/
cityangered.se /besttube/
clarkecasa.net /rhk6/
clr.dsfm.mb.ca /2964/
codeditor.awardspace.biz /uncensoredclip/
coloridellavita.com /sc/
cpvs.org /6eobh0n/
danieletranchita.com /yourvids/
dennis-leah.zzl.org /m95/
doctorsorchestra.com /qw/
dueciliguria.it /zircu/
ediltermo.com /p4zhvj0/
emmedici.net /2pg46mk/
eurobaustoff.marketing-generator.de /52649an/
euskorock.es /p4zm/
explicitflavour.freeiz.com /qk3r/
f9phx.net /svr/
fatucci.it /l04s8m2/
forwardmarchministries.org /1bc/
fotoplanet.it /bnog6s/
frenchbean.co.uk /zwr/
furius.comoj.com /1azl/
geve.be /oj4ex4/
gite-maison-pyrenees-luchon.com /jox/
googleffffffffa0ac4d9f.omicronrecords.com /me/
gosin.be /ist63z/
grimslovsms.se /cutetube/
guest.worldviewproduction.com /m2f/
hanssen-racing.com /j15/
helpbt.com /nqo40uq/
helpdroid.omicronrecords.com /7h/
hoganjobs.com /jrepsp/
holustravel.cz /5j5/
hoperidge.com /fltwizy/
hottesttomato.com /6b/
iglesiabetania1.com /7y7/
ihostu.co.uk /jic9v/
ilterrazzoallaveneziana.it /4vxaq5/
integratek.omicronrecords.com /to4u2bd/
irisjard.o2switch.net /lb/
islandmusicexport.com /hbi2ut9/
isteinaudi.it /h2a/
johnphelan.com /uynv4/
jsacm.com /z6/
kabchicago.info /1cgko/
katia-paliotti.com /0baktz/
kennethom.net /l20/
kleppcc.com /aliendemonstration/
klimentglass.cz /vwalp/
kvarteretekorren.se /60/
lanavabadajoz.com /cg/
langstoncorp.com /o2072c/
libermann.phpnet.org /madu8p/
lineapapel.com /8l20up/
longting.nl /6ch/
mainteck-fr.com /qjbo5v/
majesticdance.com /v1g/
mia-nilsson.se /cmc/
microstart.fr /lzu1/
migdal.org.il /y952eo/
mindbodyandsolemt.com /pnbn/
musicomm.ca /a5z/
nassnig.org /z1/
neweed.org /x4t/
nosneezes.com /5hjkdjo/
nottinghamdowns.com /m7ec/
nutman-group.com /92m/
omicronsystems.inc.md /eho0/
on3la.be /bgfhclg/
onlineadmin.net /b7uccx/
ornskoldskatten.se /m1u/
oxhalsobygg.se /amaizingmovies/
- Recommended reading: Dissecting Koobface Gang's Latest Facebook Spreading Campaign
pegasolavoro.it /3l6/
peteknightdays.com /4ok4/
pheromoneforum.org /ds/
pilatescenter.se /bgx8e/
plymouth-tuc.org.uk /xhaq/
popeur.fr /m7yaw/
pro-du-bio.com /af6xtp/
prousaudio.com /4isg/
puertohurraco.org /q3a1gz/
radioluz900am.com /3i993/
reporsenna.netsons.org /zvz/
rhigar.nu /6v/
richmondpowerboat.com /tifax5/
rmg360.co.cc /22i/
roninwines.com /wonderfulvids/
rrmaps.com /j6o/
rvl.it /bv6k/
scarlett-oharas.com /my0333/
secure.tourinrome.org /qyp/
servicehandlaren.se /yq9ahw0/
servicehandlaren.spel-service.com /q9q115/
sgottnerivers.com /y0j16rw/
shofarcall.com /zi/
sirius-expedition.com /x4yab/
slcsc.co.uk /0kem/
soderback.eu /xvg9/
spel-service.com /xm/
sporthal.msolutions.be /vyx3yu/
steelstoneind.com /yzp/
stgeorgesteel.com /ji/
stgeorgesteel.com /ylnwlr/
stubbieholderking.com /dyarx1/
sweet-peasdog.se /0rcjo/
taekwondovelden.nl /mhnskk/
testjustin.comze.com /oafxzy/
the-beehive.com /r8x3cm/
the-beehive.com /weqw7e/
thedallestransmission.com /rjsg2/
therealmagnets.comuv.com /3wn19n/
thestrategicfrog.110mb.com /66vv/
tizianozanella.it/ k2cei/
trustonecorp.com /mabmpp/
unna.nu /6lie/
uroloki.omicronrecords.com /9t/
vaxjoff.com /4fpu/
veerle-frank.be /l01/
verdiverdi.net /3tt/
visionministerial.com /p191/
waffotis.se /yufi3u/
watsonspipingandheating.com /krda/
welplandeast.com /6q/
WESTCOASTPERFORMANCECOATINGS.COM /1tw4/
williamarias.us /na9mq/
woodworksbyjamie.com /90mrjb/
wowparis2000.com /rtsz/
yin-art.be /a75ble/
youniverse.site50.net /4a9r/
Due to the diversity of its cybercrime operations, the Koobface gang is always worth keeping an eye on. Best of all - it's done semi-automatically these days.
The best is yet to come, stay tuned!
Related Koobface gang/botnet research:
Dissecting Koobface Gang's Latest Facebook Spreading Campaign
Koobface Redirectors and Scareware Campaigns Now Hosted in Moldova
10 things you didn't know about the Koobface gang
A Diverse Portfolio of Scareware/Blackhat SEO Redirectors Courtesy of the Koobface Gang
How the Koobface Gang Monetizes Mac OS X Traffic
The Koobface Gang Wishes the Industry "Happy Holidays"
Koobface-Friendly Riccom LTD - AS29550 - (Finally) Taken Offline
Koobface Botnet Starts Serving Client-Side Exploits
Massive Scareware Serving Blackhat SEO, the Koobface Gang Style
Koobface Botnet's Scareware Business Model - Part Two
Koobface Botnet's Scareware Business Model - Part One
Koobface Botnet Redirects Facebook's IP Space to my Blog
New Koobface campaign spoofs Adobe's Flash updater
Social engineering tactics of the Koobface botnet
Koobface Botnet Dissected in a TrendMicro Report
Movement on the Koobface Front - Part Two
Movement on the Koobface Front
Koobface - Come Out, Come Out, Wherever You Are
Dissecting Koobface Worm's Twitter Campaign
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.