Never trust an AS whose abuse-mailbox is using a Gmail account (
piotrek89@gmail.com), and in particular one that you've come across to during several malware campaigns over the past couple of month. It's
AS6851, BKCNET "SIA" IZZI I'm referring to, also known as
Sagade Ltd.
Let's dissect the currently ongoing malicious activity at that Latvian based AS, expose the exploit/malware/crimeware/scareware serving domain portfolios, sample some of the currently active binaries and emphasize on the hijacking of Google/Yahoo and Bing search engines, as well as take a brief retrospective of AS6851's activities profiled over the past couple of months.
What's so special about AS6851 anyway? It's the numerous times in which the AS popped-up in previously profiled campaigns (
see related posts at the bottom of the post), next to a pretty interesting Koobface gang connection.
An excerpt from a previous post:
"
What's so special about AS6851, BKCNET "SIA" IZZI anyway? It's the Koobface gang connection in the face of urodinam.net, which is also hosted within AS6851, currently responding to 91.188.59.10. More details on urodinam.net: Moreover, on the exact same IP where Koobface gang's urodinam.net is parked, we also have the currently active 1zabslwvn538n4i5tcjl.com - Email: michaeltycoon@gmail.com, serving client side exploits using the Yes Malware Exploitation kit - 91.188.59.10 /temp/cache/PDF.php; admin panel at: 1zabslwvn538n4i5tcjl.com /temp/admin/index.phpThe same michaeltycoon@gmail.com used to register 1zabslwvn538n4i5tcjl.com, was also profiled in the "Diverse Portfolio of Scareware/Blackhat SEO Redirectors Courtesy of the Koobface Gang" assessment."
Related data on AS6851, BKCNET/Sagade Ltd.:netname: ATECH-SAGADE
descr: Sagade Ltd.
descr: Latvia, Rezekne, Darzu 21
descr: +371 20034981
remarks: abuse-mailbox: piotrek89@gmail.com
country: LV
admin-c: JS1449-RIPE
tech-c: JS1449-RIPE
status: ASSIGNED PA
mnt-by: AS6851-MNT
source: RIPE # Filtered
person: Juris Sahurovs
remarks: Sagade Ltd.
address: Latvia, Rezekne, Darzu 21
phone: +371 20034981
abuse-mailbox: piotrek89@gmail.com
nic-hdl: JS1449-RIPE
mnt-by: ATECH-MNT
source: RIPE # Filtered AS6851 advertises 15 prefixes:* 62.84.0.0/19
* 62.84.22.0/23
* 84.38.128.0/20
* 85.234.160.0/19
* 91.123.64.0/20
* 91.188.32.0/19
* 91.188.41.0/24
* 91.188.44.0/23
* 91.188.46.0/24
* 91.188.48.0/23
* 91.188.50.0/24
* 91.188.52.0/23
* 91.188.56.0/24
* 109.110.0.0/19
* 195.244.128.0/20Uplink courtesy of:AS6747, LATTELEKOM Lattelekom
AS5518, TELIALATVIJA Telia Latvija SIA
Currently active exploits/malware/scareware serving domain portfolios within AS6851:
Parked at/responding to
85.234.190.15 are:
anrio.in - Email: Ometovgordey@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cogoo.in - Email: SamatovNail@mail.com
conyx.in - Email: NikitasZoya@mail.com
eboyx.in - Email: NikitasZoya@mail.com
ederm.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
foryx.in - Email: NikitasZoya@mail.com
liuyx.in - Email: NikitasZoya@mail.com
moosd.in - Email: VasilevaSvetlana@mail.com
oserr.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ostom.in - Email: skripnikkseniya@live.com
purnv.in - Email: BajenovOleg@mail.com
ragew.in - Email: vednerovasvetlana@gmail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
sdali.in - Email: VasilevaSvetlana@mail.com
seedw.in - Email: vednerovasvetlana@gmail.com
shkey.in - Email: FirulevAndrey@mail.com
spkey.in - Email: FirulevAndrey@mail.com
thynv.in - Email: BajenovOleg@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
wakey.in - Email: FirulevAndrey@mail.com
yxial.in - Email: GaevAlexandr@mail.com
Parked at/responding to
85.234.190.4 are:
anrio.in - Email: Ometovgordey@mail.com
antsd.in - Email: IvanovEvgeny@mail.com
appsd.in - Email: IvanovEvgeny@mail.com
arsdh.in - Email: shadrenkovavanda@mail.com
barui.in - Email: RijovAlexandr@mail.com
bkpuo.in - Email: erofeevalexey77@gmail.com
bleui.in - Email: RijovAlexandr@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
bryhw.in - Email: matatovayanna@mail.com
butui.in - Email: RijovAlexandr@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cirui.in - Email: RijovAlexandr@mail.com
cogoo.in - Email: RijovAlexandr@mail.com
conuo.in - Email: erofeevalexey77@gmail.com
conyx.in - Email: NikitasZoya@mail.com
cusnv.in - Email: SimakovSergey@mail.com
czkey.in - Email: ZaharcevSergey@mail.com
degoo.in - Email: SamatovNail@mail.com
dugoo.in - Email: SamatovNail@mail.com
ecrio.in - Email: Ometovgordey@mail.com
ectuo.in - Email: erofeevalexey77@gmail.com
ederm.in - Email: EvenkoIvan@mail.com
edger.in - Email: EvenkoIvan@mail.com
edimp.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
elrio.in - Email: Ometovgordey@mail.com
enguo.in - Email: erofeevalexey77@gmail.com
eqrio.in - Email: Ometovgordey@mail.com
fibnv.in - Email: SimakovSergey@mail.com
glouo.in - Email: erofeevalexey77@gmail.com
habsd.in - Email: LomaevaTatyana@mail.com
hecuo.in - Email: erofeevalexey77@gmail.com
hekey.in - Email: ZaharcevSergey@mail.com
hygos.in - Email: Hohlunovanika@live.com
imbos.in - Email: Hohlunovanika@live.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
latuo.in - Email: erofeevalexey77@gmail.com
linuo.in - Email: erofeevalexey77@gmail.com
makey.in - Email: ZaharcevSergey@mail.com
oscog.in - Email: Nigmatovaanastasia@hotmail.com
oserr.in - Email: skripnikkseniya@live.com
osmac.in - Email: skripnikkseniya@live.com
osmot.in - Email: skripnikkseniya@live.com
ospor.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ossio.in - Email: skripnikkseniya@live.com
ostab.in - Email: skripnikkseniya@live.com
ostac.in - Email: skripnikkseniya@live.com
ostio.in - Email: skripnikkseniya@live.com
ouned.in - Email: PoleschukovaGalina@mail.com
purnv.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
rekey.in - Email: ZaharcevSergey@mail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
scoos.in - Email: Nigmatovaanastasia@hotmail.com
sdali.in - Email: VasilevaSvetlana@mail.com
sdome.in - Email: OsvyanikovaDarya@mail.com
shkey.in - Email: FirulevAndrey@mail.com
spkey.in - Email: FirulevAndrey@mail.com
sydos.in - Email: Nigmatovaanastasia@hotmail.com
thynv.in - Email: BajenovOleg@mail.com
ugiyx.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
uithi.in - Email: IvanovEvgeny@mail.com
uityp.in - Email: IvanovEvgeny@mail.com
uityr.in - Email: IvanovEvgeny@mail.com
varyx.in - Email: GaevAlexandr@mail.com
wakey.in - Email: FirulevAndrey@mail.com
yokey.in - Email: FirulevAndrey@mail.com
yxiac.in - Email: GaevAlexandr@mail.com
yxial.in - Email: GaevAlexandr@mail.com
Parked at/responding to
91.188.60.225 are:
abrie.in - Email: Bodunovanton@mail.com
agros.in - Email: Hohlunovanika@live.com
alldh.in - Email: bondyashovandrey@mail.com
alodh.in - Email: radostovamariya@mail.com
anrio.in - Email: Ometovgordey@mail.com
antsd.in - Email: IvanovEvgeny@mail.com
aoxtv.in - Email: AkulovSergey@mail.com
appsd.in - Email: IvanovEvgeny@mail.com
aquui.in - Email: RijovAlexandr@mail.com
arrie.in - Email: Bodunovanton@mail.com
arsdh.in - Email: shadrenkovavanda@mail.com
balsd.in - Email: IvanovEvgeny@mail.com
barui.in - Email: RijovAlexandr@mail.com
bikey.in - Email: ZaharcevSergey@mail.com
bkpuo.in - Email: erofeevalexey77@gmail.com
bleui.in - Email: RijovAlexandr@mail.com
brayx.in - Email: NikitasZoya@mail.com
broyx.in - Email: NikitasZoya@mail.com
brusd.in - Email: LomaevaTatyana@mail.com
bryhw.in - Email: matatovayanna@mail.com
butui.in - Email: RijovAlexandr@mail.com
butuo.in - Email: erofeevalexey77@gmail.com
butyx.in - Email: NikitasZoya@mail.com
cated.in - Email: PoleschukovaGalina@mail.com
cedhw.in - Email: lopushkoamariya@mail.com
chrie.in - Email: Bodunovanton@mail.com
chrio.in - Email: Ometovgordey@mail.com
cirui.in - Email: RijovAlexandr@mail.com
clrio.in - Email: Ometovgordey@mail.com
cogoo.in - Email: SamatovNail@mail.com
conuo.in - Email: erofeevalexey77@gmail.com
conyx.in - Email: NikitasZoya@mail.com
corie.in - Email: Bodunovanton@mail.com
curie.in - Email: Bodunovanton@mail.com
cusnv.in - Email: SimakovSergey@mail.com
czkey.in - Email: ZaharcevSergey@mail.com
degoo.in - Email: SamatovNail@mail.com
dennv.in - Email: SimakovSergey@mail.com
dugoo.in - Email: SamatovNail@mail.com
eagoo.in - Email: SamatovNail@mail.com
eboyx.in - Email: NikitasZoya@mail.com
ecrio.in - Email: Ometovgordey@mail.co
ectuo.in - Email: erofeevalexey77@gmail.com
edbal.in - Email: VasilevOleg@mail.com
edban.in - Email: VasilevOleg@mail.com
ederc.in - Email: EvenkoIvan@mail.com
ederm.in - Email: EvenkoIvan@mail.com
edger.in - Email: EvenkoIvan@mail.com
edimp.in - Email: EvenkoIvan@mail.com
edois.in - Email: EvenkoIvan@mail.com
elrio.in - Email: Ometovgordey@mail.com
enguo.in - Email: erofeevalexey77@gmail.com
eprio.in - Email: Ometovgordey@mail.com
eqrio.in - Email: Ometovgordey@mail.com
esrie.in - Email: Bodunovanton@mail.com
fakey.in - Email: ZaharcevSergey@mail.com
fegoo.in - Email: SamatovNail@mail.com
fibnv.in - Email: SimakovSergey@mail.com
foryx.in - Email: NikitasZoya@mail.com
franv.in - Email: SimakovSergey@mail.com
fraos.in - Email: Hohlunovanika@live.com
garie.in - Email: Bodunovanton@mail.com
glouo.in - Email: erofeevalexey77@gmail.com
guinv.in - Email: SimakovSergey@mail.com
habsd.in - Email: LomaevaTatyana@mail.com
hecuo.in - Email: erofeevalexey77@gmail.com
hekey.in - Email: ZaharcevSergey@mail.com
humos.in - Email: Hohlunovanika@live.com
hygos.in - Email: Hohlunovanika@live.com
hyrie.in - Email: Bodunovanton@mail.com
imbos.in - Email: Hohlunovanika@live.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
jobos.in - Email: Hohlunovanika@live.com
kykey.in - Email: ZaharcevSergey@mail.com
latuo.in - Email: erofeevalexey77@gmail.com
leunv.in - Email: SimakovSergey@mail.com
linuo.in - Email: erofeevalexey77@gmail.com
liuyx.in - Email: NikitasZoya@mail.com
makey.in - Email: ZaharcevSergey@mail.com
moosd.in - Email: VasilevaSvetlana@mail.com
naios.in - Email: Hohlunovanika@live.com
nvenc.in - Email: BajenovOleg@mail.com
oscog.in - Email: Nigmatovaanastasia@hotmail.com
osenc.in - Email: Nigmatovaanastasia@hotmail.com
oserr.in - Email: skripnikkseniya@live.com
osmac.in - Email: skripnikkseniya@live.com
osmot.in - Email: skripnikkseniya@live.com
ospor.in - Email: skripnikkseniya@live.com
ossce.in - Email: skripnikkseniya@live.com
ossio.in - Email: skripnikkseniya@live.com
ostab.in - Email: skripnikkseniya@live.com
ostac.in - Email: skripnikkseniya@live.com
ostio.in - Email: skripnikkseniya@live.com
ostom.in - Email: skripnikkseniya@live.com
ouned.in - Email: PoleschukovaGalina@mail.com
purnv.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
ragew.in - Email: vednerovasvetlana@gmail.com
rekey.in - Email: ZaharcevSergey@mail.com
relsd.in - Email: VasilevaSvetlana@mail.com
retnv.in - Email: BajenovOleg@mail.com
saled.in - Email: VasilevOleg@mail.com
sated.in - Email: VasilevOleg@mail.com
scoos.in - Email: Nigmatovaanastasia@hotmail.com
sdali.in - Email: VasilevaSvetlana@mail.com
sdall.in - Email: VasilevaSvetlana@mail.com
sdayb.in - Email: OsvyanikovaDarya@mail.com
sdaye.in - Email: OsvyanikovaDarya@mail.com
sdayo.in - Email: OsvyanikovaDarya@mail.com
sdene.in - Email: OsvyanikovaDarya@mail.com
sdich.in - Email: OsvyanikovaDarya@mail.com
sdome.in - Email: OsvyanikovaDarya@mail.com
seedw.in - Email: vednerovasvetlana@gmail.com
shkey.in - Email: FirulevAndrey@mail.com
smoed.in - Email: VasilevOleg@mail.com
soted.in - Email: VasilevOleg@mail.com
spios.in - Email: Nigmatovaanastasia@hotmail.com
spkey.in - Email: FirulevAndrey@mail.com
stteop.in - Email: fibra_appl@yahoo.com
sunyx.in - Email: GaevAlexandr@mail.com
sydos.in - Email: Nigmatovaanastasia@hotmail.com
teaed.in - Email: VasilevOleg@mail.com
thynv.in - Email: BajenovOleg@mail.com
ugiyx.in - Email: GaevAlexandr@mail.com
uinei.in - Email: UshakovAndrey@mail.com
uinge.in - Email: UshakovAndrey@mail.com
uiren.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uisee.in - Email: UshakovAndrey@mail.com
uisma.in - Email: IvanovEvgeny@mail.com
uitem.in - Email: IvanovEvgeny@mail.com
uithi.in - Email: IvanovEvgeny@mail.com
uityp.in - Email: IvanovEvgeny@mail.com
uityr.in - Email: IvanovEvgeny@mail.com
varyx.in - Email: GaevAlexandr@mail.com
veged.in - Email: VasilevOleg@mail.com
wakey.in - Email: FirulevAndrey@mail.com
whasd.in - Email: VasilevaSvetlana@mail.com
wimed.in - Email: VasilevOleg@mail.com
woonv.in - Email: BajenovOleg@mail.com
yokey.in - Email: FirulevAndrey@mail.com
yxiac.in - Email: GaevAlexandr@mail.com
yxial.in - Email: GaevAlexandr@mail.com
yxiam.in - Email: GaevAlexandr@mail.com
Parked at/responding to
91.188.60.3 are:
0checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
10checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
20checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
30checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
40checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
50checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
60checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
70checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
80checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
90checkingyourtraffic.com - Email: FranciscoPGeorge@hotmail.com
av-scaner-onlinemachine.com - Email: gershatv07@gmail.com
easy-ns-server.org - Email: russell1985@hotmail.com
fast-scanerr-online.org - Email: roberson@hotmail.com
fast-scanneronline.org - Email: roberson@hotmail.com
fastscanner-online.org - Email: roberson@hotmail.com
fastscannerr-online.org - Email: roberson@hotmail.com
myantivirsplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirsplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirusplus.org - Email: FranciscoPGeorge@hotmail.com
my-antivirus-plus.org - Email: FranciscoPGeorge@hotmail.com
myprotectonline.org - Email: FranciscoPGeorge@hotmail.com
my-protectonline.org - Email: FranciscoPGeorge@hotmail.com
my-protect-online.org - Email: FranciscoPGeorge@hotmail.com
sysprotectonline.org - Email: FranciscoPGeorge@hotmail.com
sys-protectonline.org - Email: FranciscoPGeorge@hotmail.com
sys-protect-online.org - Email: FranciscoPGeorge@hotmail.com
Parked at/responding to
91.188.59.74 are:
allforil1i.com - Email: lordjok@gmail.com
alltubeforfree.com - Email: lordjok@gmail.com
allxtubevids.net - Email: lordjok@gmail.com
downloadfreenow.in - Email: lordjok@gmail.com
enteri1llisec.in - Email: leshapopovi@gmail.com
freeanalsextubemovies.com - Email: lordjok@gmail.com
freetube06.com - Email: lordjok@gmail.com
freeviewgogo.com - Email: leshapopovi@gmail.com
homeamateurclips.com - Email: lordjok@gmail.com
hot4youxxx.in - Email: lordjok@gmail.com
hotxtube.in - Email: lordjok@gmail.com
hotxxxtubevideo.com
iil10oil0.com
ilio01ili1.comillinoli1l.in - Email: lordjok@gmail.com
porntube2000.com - Email: welolseeees@gmail.com
porntubefast.com - Email: welolseeees@gmail.com
porn-tube-video.com - Email: welolseeees@gmail.com
viewnowfast.com - Email: lordjok@gmail.com
viewxxxfreegall.net - Email: leshapopovi@gmail.com
viiistifor1.comxhuilil1ii.com - Email: lordjok@gmail.com
youvideoxxx.com - Email: jonnytrade@gmail.com
Parked at/responding to 85.234.190.16 are:
appsd.in - Email: IvanovEvgeny@mail.com
bikey.in - Email: IvanovEvgeny@mail.com
fibnv.in - Email: SimakovSergey@mail.com
franv.in - Email: SimakovSergey@mail.com
guinv.in - Email: SimakovSergey@mail.com
hekey.in - Email: ZaharcevSergey@mail.com
intsd.in - Email: LomaevaTatyana@mail.com
ionnv.in - Email: SimakovSergey@mail.com
jamsd.in - Email: LomaevaTatyana@mail.com
leunv.in - Email: SimakovSergey@mail.com
nvenc.in - Email: BajenovOleg@mail.com
pxdmx.in - Email: GaleevDjamil@mail.com
uinei.in - Email: GaleevDjamil@mail.com
uinge.in - Email: UshakovAndrey@mail.com
uiren.in - Email: UshakovAndrey@mail.com
uirin.in - Email: UshakovAndrey@mail.com
uisap.in - Email: UshakovAndrey@mail.com
uisee.in - Email: UshakovAndrey@mail.com
woonv.in - Email: BajenovOleg@mail.com
yxiam.in - Email: GaevAlexandr@mail.com
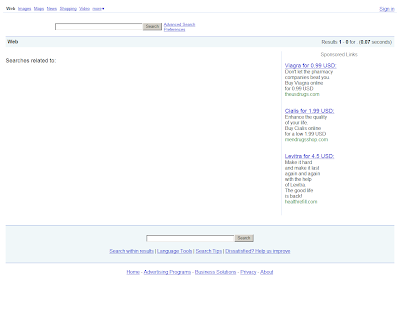
Detection rates for the currently active malware samples, including the HOSTS file modifications on infected hosts, for the purposely of redirecting users to
cybercrime-friendly search engines, monetized through traffic trading affiliate programs.
-
78490.jar - Result: 0/42 (0%)
File size: 209 bytes
MD5 : 64a19d9b7f0e81c7a5f6d63853a3ed49
SHA1 : 9f8f208c8cdb854cdc342d43a75a3d8672e87822
-
ad3.exe - Result: 41/42 (97.62%)
File size: 2560 bytes
MD5...: 9362a3aee38102dde68211ccb63c3e07
SHA1..: 8758679540f48feba82d2b022b8d71756eb935e7
-
a-fast.exe - Result: 36/42 (85.72%)
File size: 979968 bytes
MD5...: 69f3949141073679b77aa4d34e41a3e7
SHA1..: e074de46e4760eef522ab85737790058cc3f2fad
-
dm.exe - Result: 37/42 (88.1%)
File size: 83968 bytes
MD5...: b658d9b812454e99b2915ab2e9594b94
SHA1..: 134bfb643ae2f161c99db14c448485e261e96c91
-
iv.exe - Result: 8/42 (19.05%)
File size: 86016 bytes
MD5...: f94ed2f9d7a672fe3ff8bf077289b2d5
SHA1..: 2f78a296e1267ae1cf9ebd5c18de5b8d241c1306
-
j2_t895.jar - Result: 0/42 (0%)
File size: 211 bytes
MD5...: 4b34618a0499a99e9c98e03aa79d53cf
SHA1..: d109babf78ec48ba8d7798bce784097ed26757db
-
movie.exe - Result: 40/42 (95.24%)
File size: 64866 bytes
MD5...: 801f9fa958192b6714a5a4c2e2f92f07
SHA1..: 241bc9d7540d9d53cc1578e3d57c44be9931e418
-
tst.exe - Result: 35/42 (83.34%)
File size: 356352 bytes
MD5...: b0ed4701af13f11089de850a1273d24f
SHA1..: 5e98000b60d0ca0b2adbd837feaf05f439f95c87
-
wsc.exe - Result: 37/42 (88.1%)
File size: 24576 bytes
MD5...: 80427b754b11de653758dd5e1ba3de1c
SHA1..: 554e1331fdc050bd603f6f3628285008a91cba37
HOSTS file modification:AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
89.149.210.109 www.google.com
89.149.210.109 www.google.de
89.149.210.109 www.google.fr
89.149.210.109 www.google.co.uk
89.149.210.109 www.google.com.br
89.149.210.109 www.google.it
89.149.210.109 www.google.es
89.149.210.109 www.google.co.jp
89.149.210.109 www.google.com.mx
89.149.210.109 www.google.ca
89.149.210.109 www.google.com.au
89.149.210.109 www.google.nl
89.149.210.109 www.google.co.za
89.149.210.109 www.google.be
89.149.210.109 www.google.gr
89.149.210.109 www.google.at
89.149.210.109 www.google.se
89.149.210.109 www.google.ch
89.149.210.109 www.google.pt
89.149.210.109 www.google.dk
89.149.210.109 www.google.fi
89.149.210.109 www.google.ie
89.149.210.109 www.google.no
89.149.210.109 search.yahoo.com
89.149.210.109 us.search.yahoo.com
89.149.210.109 uk.search.yahoo.com-
rc.exe - Result: 41/42 (97.62%)
File size: 2560 bytes
MD5...: 9362a3aee38102dde68211ccb63c3e07
SHA1..: 8758679540f48feba82d2b022b8d71756eb935e7
HOSTS file modification:AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
89.149.249.196 www.google.com
89.149.249.196 www.google.de
89.149.249.196 www.google.fr
89.149.249.196 www.google.co.uk
89.149.249.196 www.google.com.br
89.149.249.196 www.google.it
89.149.249.196 www.google.es
89.149.249.196 www.google.co.jp
89.149.249.196 www.google.com.mx
89.149.249.196 www.google.ca
89.149.249.196 www.google.com.au
89.149.249.196 www.google.nl
89.149.249.196 www.google.co.za
89.149.249.196 www.google.be
89.149.249.196 www.google.gr
89.149.249.196 www.google.at
89.149.249.196 www.google.se
89.149.249.196 www.google.ch
89.149.249.196 www.google.pt
89.149.249.196 www.google.dk
89.149.249.196 www.google.fi
89.149.249.196 www.google.ie
89.149.249.196 www.google.no
89.149.249.196 www.google.co.in
89.149.249.196 search.yahoo.com
89.149.249.196 us.search.yahoo.com
89.149.249.196 uk.search.yahoo.com-
installer.0028.exe - Result: 9/42 (21.43%)
File size: 43735 bytes
MD5...: a6d7073b8b9bc0dc539605914c853da2
SHA1..: 1940b6a6b2f93b44633ef04eab900e0a9dc6fa64
HOSTS file modification:AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
84.16.244.60 www.google.com
84.16.244.60 us.search.yahoo.com
84.16.244.60 uk.search.yahoo.com
84.16.244.60 search.yahoo.com
84.16.244.60 www.google.com.br
84.16.244.60 www.google.it
84.16.244.60 www.google.es
84.16.244.60 www.google.co.jp
84.16.244.60 www.google.com.mx
84.16.244.60 www.google.ca
84.16.244.60 www.google.com.au
84.16.244.60 www.google.nl
84.16.244.60 www.google.co.za
84.16.244.60 www.google.be
84.16.244.60 www.google.gr
84.16.244.60 www.google.at
84.16.244.60 www.google.se
84.16.244.60 www.google.ch
84.16.244.60 www.google.pt
84.16.244.60 www.google.dk
84.16.244.60 www.google.fi
84.16.244.60 www.google.ie
84.16.244.60 www.google.no
84.16.244.60 www.google.de
84.16.244.60 www.google.fr
84.16.244.60 www.google.co.uk
84.16.244.60 www.bing.com-
installer.0022.exe - Result: 9/42 (21.43%)
File size: 43731 bytes
MD5...: 62464b9e367a9edb06541a2a90931157
SHA1..: 425c859a883900ccf5cf7b8a6a5f6bc9279d763c
HOSTS file modification:AS28753, NETDIRECT AS NETDIRECT Frankfurt, DE
84.16.244.15 www.google.com
84.16.244.15 us.search.yahoo.com
84.16.244.15 uk.search.yahoo.com
84.16.244.15 search.yahoo.com
84.16.244.15 www.google.com.br
84.16.244.15 www.google.it
84.16.244.15 www.google.es
84.16.244.15 www.google.co.jp
84.16.244.15 www.google.com.mx
84.16.244.15 www.google.ca
84.16.244.15 www.google.com.au
84.16.244.15 www.google.nl
84.16.244.15 www.google.co.za
84.16.244.15 www.google.be
84.16.244.15 www.google.gr
84.16.244.15 www.google.at
84.16.244.15 www.google.se
84.16.244.15 www.google.ch
84.16.244.15 www.google.pt
84.16.244.15 www.google.dk
84.16.244.15 www.google.fi
84.16.244.15 www.google.ie
84.16.244.15 www.google.no
84.16.244.15 www.google.de
84.16.244.15 www.google.fr
84.16.244.15 www.google.co.uk
84.16.244.15 www.bing.comThe payment gateway structure+related domains for the scareware campaigns:
-
fast-payments.com/index.php?prodid=antus_02_01&afid= - 91.188.59.27 - Email: jclarke980@gmail.com
-
ns1.fastsecurebilling.com - 91.188.59.26 - Email: jclarke980@gmail.com
-
easypayments-online.com - 91.188.59.28 - Email: jclarke980@gmail.com
-
fast-payments.com - 91.188.59.27 - Email: jclarke980@gmail.com
-
billingonline.net - 91.188.59.29 - Email: kevbush@billingonline.net
-
billsolutions.net - 91.188.59.25
In respect to the IPs used in HOSTS file modification, one is of particular interest -
89.149.210.109, as it was first profiled in November, 2009's "
Koobface Botnet's Scareware Business Model - Part Two" with
MD5: 0fbf1a9f8e6e305138151440da58b4f1 modifying HOSTS file using the same IP, and also phoning back to the Koobface gang's 1.0 hardcore C&C -
urodinam.net/8732489273.phpWhen it comes to cybercrime, there's no such thing as a coincidence. What's static is the
interaction between the usual suspects, systematically switching hosting providers, introducing new domains, and
conveniently denying their monetization tactics.
You wish.
Profiled AS6851, BKCNET/Sagade Ltd. activity:GoDaddy's Mass WordPress Blogs Compromise Serving ScarewareDissecting the Mass DreamHost Sites CompromiseSpamvertised iTunes Gift Certificates and CV Themed Malware CampaignsDissecting the 100,000+ Scareware Serving Fake YouTube Pages CampaignFacebook Photo Album Themed Malware Campaign, Mass SQL Injection Attacks Courtesy of AS42560 This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.
Continue reading →



































RSS Feed