This presentation aims to detail Dancho Danchev's perspective into gathering threat intelligence processing it and enriching and disseminating it to users vendors and organizations globally heavily relying on a threat intelligence "rock star" model and methodology where the ultimate goal for this case study would be to take down Iran-based hackers and hacking groups and their entire online operations and attempt to shut them down and take them offline citing possible malicious use and actual abuse of international Internet laws and regulations and ultimatetely attempt to make an impact in terms of tracking them down and offering never-published and discussed personally identifiable information on their whereabouts and malicious online activities.
Continue reading →Exposing the Internet-Connected Infrastructure of the REvil Ransomware Gang - An In-Depth OSINT Analysis
0In this post I've decided to do an in-depth OSINT analysis on the recently busted REvil ransomware gang and decided to elaborate more and emphasize on the key fact in specific how come that a single ransomware group with several publicly accessible and easy to shut down C&C (command and control) server domains including several randomly generated Dark Web Onion URLs could easily result in millions of damage and who really remembers a situation when getting paid for getting hacked including the basic principle that you should never interact with cybercriminals but instead should passively and proactively monitor them could result in today's modern and unspoken ransomware growth epidemic and the rise of wrong buzz words as for instance ransomware-as-a-corporation where you basically have the bad guys obtain initial access to an organization's network and then hold its information encryption leading us to the logical conclusion who on Earth would pay millions of dollars to avoid possible bad reputation damage including to fuel growth into a rogue and fraudulent scheme as as for instance the encryption of sensitive company information and leaking it to the public in exchange for financial rewards.
Related responding IPs for hxxp://decryptor[.]cc:
2021/12/30 - 103[.]224[.]212[.]219
2021/10/23 - 198[.]58[.]118[.]167
2021/10/23 - 45[.]79[.]19[.]196
2021/10/23 - 45[.]56[.]79[.]23
2021/10/23 - 45[.]33[.]18[.]44
2021/10/23 - 72[.]14[.]178[.]174
2021/10/23 - 45[.]33[.]2[.]79
2021/10/23 - 45[.]33[.]30[.]197
2021/10/23 - 96[.]126[.]123[.]244
2021/10/23 - 45[.]33[.]23[.]183
2021/10/23 - 173[.]255[.]194[.]134
2021/10/23 - 45[.]33[.]20[.]235
2021/10/23 - 72[.]14[.]185[.]43
2021/10/08 - 78[.]41[.]204[.]37
2021/10/03 - 209[.]126[.]123[.]12
2021/09/24 - 78[.]41[.]204[.]28
2021/09/03 - 209[.]126[.]123[.]13
2021/08/19 - 78[.]41[.]204[.]38
2021/08/02 - 81[.]171[.]22[.]4
2021/07/27 - 81[.]171[.]22[.]6
2021/04/17 - 103[.]224[.]212[.]219
2020/11/10 - 45[.]138[.]74[.]27
2020/11/04 - 45[.]138[.]74[.]27
2020/09/14 - 136[.]243[.]214[.]30
2020/09/06 - 136[.]243[.]214[.]30
2020/08/30 - 212[.]22[.]78[.]23
2020/08/23 - 212[.]22[.]78[.]23
2020/07/30 - 212[.]22[.]78[.]23
2020/07/24 - 212[.]22[.]78[.]23
2020/07/07 - 212[.]22[.]78[.]23
2020/05/30 - 193[.]164[.]150[.]68
2020/05/20 - 193[.]164[.]150[.]68
2020/05/10 - 194[.]36[.]190[.]41
2020/05/08 - 194[.]36[.]190[.]41
2020/04/29 - 194[.]36[.]190[.]41
2020/04/06 - 194[.]36[.]190[.]41
2020/02/17 - 94[.]103[.]87[.]78
Related responding IPs for hxxp://decryptor[.]top (185[.]193[.]127[.]162; 192[.]124[.]249[.]13; 96[.]9[.]252[.]156):
2021/07/12 - 45[.]9[.]148[.]108
2020/09/18 - 185[.]193[.]127[.]162
2020/09/15 - 185[.]193[.]127[.]162
2020/08/07 - 185[.]193[.]127[.]162
2020/01/16 - 162[.]251[.]120[.]66
2019/12/23 - 45[.]138[.]96[.]206
2019/12/12 - 107[.]175[.]217[.]162
2019/10/07 - 96[.]9[.]252[.]156
2019/09/04 - 96[.]9[.]252[.]156
2019/07/15 - 91[.]214[.]71[.]139
Related MD5s known to have been involved in the campaign:
MD5: 57d4ea7d1a9f6b1ee6b22262c40c8ef6
MD5: fe682fad324bd55e3ea9999abc463d76
MD5: e87402a779262d1a90879f86dba9249acb3dce47
MD5: 4334009488b277d8ea378a2dba5ec609990f2338
MD5: 2dccf13e199b60dd2cd52000a26f8394dceccaa6
Stay tuned!
Folks,
Who's been following my work on this blog since December, 2005? Are you interested in OSINT training? One-on-one or one-to-many sessions? Drop me a line today at dancho.danchev@hush.com on behalf of you or your organization or team and let's help you take your team and organization to the next level.
Sample portfolio of services which I'm currently offering can be also seen here - https://disruptive-individuals.com including a copy of my CV here including the following two sample of my work here and here.
Check out some sample chapters from a free book on cyber attribution that I'm currently working on to get a better idea of what I have in mind including my style and methodology:
Stay tuned!
Continue reading →My Participation in GCHQ's Top Secret "Lovely Horse" Program to Monitor Hackers Online - An Elaboration
0Dear blog readers,
Sample personal email address accounts belonging to Blood and Honor International Groups include:
bloodandhonouraustralis@hotmail[.]com
bloodhonournsw@hotmail[.]com
bloodhonoursa@hotmail[.]com
bloodhonourqld@hotmail[.]com
bloodhonourvic@hotmail[.]com
bloodhonourwa@hotmail[.]com
bhvlaanderen@hotmail[.]com
bh_wallonie@hotmail[.]com
bloodandhonour_bulgaria@abv[.]bg
bandhcanada@yahoo[.]co[.]uk
bhhexagone@hotmail[.]fr
bh_hellas@yahoo[.]gr
support_28_zh@hotmail[.]com
nederland@bloodhonournederland[.]com
bloodandhonourhungary28@gmail[.]com
isdm2010@gmail[.]com
vfs@libero[.]it
bhportugal28@yahoo[.]com
brotherhood28serbia@hotmail[.]com
28slov@gmail[.]com
bhe_bloodhonour@yahoo[.]es
28sweden@hotmail[.]se
ehukraine@bhukraine[.]org
RAGEN[.]FURY@VIRGIN[.]NET
axis@bloodandhonourworldwide[.]co[.]uk
southlands28@hotmail[.]com
westcountrybloodandhonour@yahoo[.]co[.]uk
wycombe828@yahoo[.]com
bandhcentral@bloodandhonourcentral[.]co[.]uk
westmidsbandh@yahoo[.]co[.]uk
bnsm@bnsm[.]co[.]uk
general@bloodandhonourworldwide[.]co[.]uk
webmaster@bloodandhonourworldwide[.]co[.]uk
s[.]london-bh@hotmail[.]co[.]uk
bloodandhonour[.]yorkshire@hotmail[.]co[.]uk
northeast1488@hotmail[.]co[.]uk
highlanderdivision28@hotmail[.]co[.]uk
highlander[.]eastcoast@hotmail[.]com ;
bhamericandivision@yahoo[.]com
bhwales@googlemail[.]com
ulsterbg@hotmail[.]co[.]uk
Sample screenshots of logo of Blood and Honor Bulgaria include:
An Update on My Disappearance and Kidnapping Attempt Courtesy of Bulgarian Law Enforcement Officers from the City of Troyan Bulgaria Circa 2010 - An Analysis
0Folks,
Check this out! An image is worth a thousand words.
Related Facebook profile IDs known to have been involved in the case:
https://www.facebook.com/profile.php?id=100005932519460 - Birthdate - 1976 - July 12
https://www.facebook.com/profile.php?id=100030506870037 - Birthdate - 1964 - August 21
Dancho Danchev's Disappearance 2010 - Official Complaint Against Republic of Bulgaria
Dancho Danchev's Disappearance - 2010 - Official Complaint Against Republic of Bulgaria - Part Three
Dancho Danchev's Disappearance - 2010 - Official Complaint Against Republic of Bulgaria - Part Two
Deep from the Trenches in Bulgaria - Part Three
Deep from the Trenches in Bulgaria - Part Two
How I Got Robbed and Beaten and Illegally Arrested by a Local Troyan Gang in Bulgaria
A Profile of a Bulgarian Kidnapper – Pavlin Georgiev (Павлин Георгиев/Васил Моев Гачевски/Явор Колев) – An Elaboration on Dancho Danchev’s Disappearance circa 2010 – An Analysis
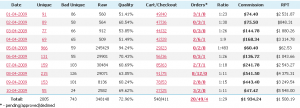
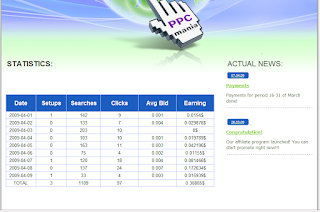
Exposing the Pay Per Install (PPI) Underground Market Fraudulent and Rogue Business Model - A Photos Compilation
0Stay tuned! Continue reading →





















































































































































































































































































RSS Feed