
Remember the Ukrainian group of cyber criminals that was responsible for last week's
massive blackhat SEO campaign that was serving scareware, followed by the
timely hijacking of Mickeyy worm keywords a week earlier to once again serve rogue security software?
They are back with new blackhat SEO farms which they continue monetizing through
rogue security software. Time to dissect their latest campaign and expose their malicious practices.

Once having most of their previous domains blacklisted/shut down, the group naturally introduced new ones, and changed the search engine optimization theme to swine flu, in between a variation of their previous one relying on catchy titles such as
USA News; BBC News; CNN News as well as Hottest info!; HOT NEWS; Official Website and Official Site.

Upon visiting the site, an obfuscated iFrame statically hosted on all of the participating domains in the form of
2qnews.07x .net/images/menu.js redirects the user to
sexerotika2009 .ru/admin/red/en.php (74.54.176.50; Email: rebsdtis@land.ru). Are you noticing the
directory structure similarities? Appreciate my rhetoric, it's last month's
blackhat SEO gang with a new portfolio of domains.
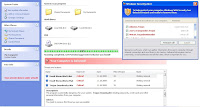
What follows is the usual referrer check : "
var ref,i,is_se=0; var se = new Array("google.","msn.","yahoo.","comcast.","aol.");" from where the user is redirected to
liveavantbrowser2 .cn/go.php?id=2022&key=4c69e59ac&p=1 (83.133.123.140) acting as central redirection point to the typosquatted portfolio of rogue security software domains.
The original scareware domain
vrusstatuscheck .com/1/?id=2022&smersh=a9fd94859&back=%3DjQ51TT1MUQMMI%3DN - (69.4.230.204; 38.99.170.209; 78.47.172.66; 78.47.91.153; 94.76.212.239; 94.102.48.28) is exposing the rest of the scareware (
detection rate) portfolio with the following domains parked at these IPs:
antivirusbestscannerv1 .com
antivirus-powerful-scanv2 .com
antivirus-powerful-scannerv2 .com
virusinfocheck .com
vrusstatuscheck .com
adware-removal-tool .com
1quickpcscanner .com
1spywareonlinescanner .com
1computeronlinescanner .com
1bestprotectionscanner .com
securityhelpcenter .com
antivirus-online-pro-scan .com
securedonlinecomputerscan .com
antispywarepcscanner .com
securedvirusscanner .com
virusinfocheck .com
antivirusbestscannerv1 .com
antispywareupdateservice .com
platinumsecurityupdate .com
antispywareupdatesystem .com
onlineupdatessystem .com
softwareupdatessystem .com
securedpaymentsystem .com
infosecuritycenter .com
antispywareproupdates .com
securedsoftwareupdate .cn
securedupdateslive .cn
thankyouforinstall .cn
securityupdatessystem .cn
securedsystemresources .cn
securedosupdates .cn
windowssecurityupdates .cnOnce executed it downloads Microsoft's original thank you note (
update.microsoft.com/windowsupdate/v6/thanks.aspx), and confirms the installation so that the blackhat SEO campaigners will receive a piece of the pie at
securedliveuploads .com/?act=fb&1=0&2=0&3=kfddnffaffihlcoemdkedcaefcfaffedhfmdmboc&4=eebajfjafekaifnbddghoclg&5=22&6=1&7=63&8=31&9=0&10=1Related phone-back locations:
liveavantbrowser2 .cn - (83.133.123.140)
securedliveuploads .com
liveavantbrowser2 .cn
awardspacelooksbig .us
crytheriver .biz
softwareupdatessystem .com
securedsoftwareupdate .cn
securedupdateslive .cn
securedosupdates .cn
Blackhat SEO subdomains at the free web site hosting services:
2qnews.07x .net
2rnews.07x .net
1news.07x .net
1knews.07x .net
1xnews.07x .net
gerandong.07x .net
kort.07x .net
30newsx.07x .net
4dnews.07x .net
4dnews.07x .net
laptop.07x .net
30newsf.07x .netBlackhat SEO domains participating in the second multi-theme campaign:
01may2009 .us
m1m18test .us
m1m17test .us
m1m21test .us
m1m11test .us
m1m16test .us
m1m20test .us
m1m15test .us
m1m14test .us
m1m13test .us
m1m11test .us
m1m15test .us
m1m19test .us
f9o852test .us
f9o851test .us
f9o87test .us
f9o86test .us
f9o5test .us
f9o8test .us
ff7test5 .us
g2g1test .us
Blackhat SEO domains participating in the third campaign:
greg-page-boxing.6may2009 .com - 212.95.58.156
dualsaw.06may2009 .com
craigslist-killer.5may2009 .com
Upon clicking, the user is redirected to
berusimcom .com/t.php?s=18&pk=, then to the SEO keyword logger at
berusimcom .com/in.cgi?18&seoref=¶meter=$keyword&se=$se&ur=1&HTTP_REFERER=nfl-draft.5may2009 .com&ppckey=, and then exposed to another portfolio of rogue security software (
detection rate) at
hot-porn-tubes.com/promo3/?aid=1361&vname=antivirus - 78.129.166.166; 91.212.132.12, with the following domains parked at the same IPs:
xxxtube-for-xxxtube .com
youporn-for-free .com
xtube-xmovie .com
free-xxx-central .com
xtube-downloads .com
porn-tube-movies .com
my-fuck-movies .com
niche-tube-videos-here .net
free-tube-video-central .net
tubezzz-boobezzz .net
hot-tube-tuberzzz .netPersistence must be met with persistence.
 The concept of ransomware is clearly making a comeback. During the past two months, scareware met the ransomware business model in the face of File Fix Professional 2009 and FakeAlert-CO or System Security, followed by two separate SMS-based ransomware variants Trj/SMSlock.A and a modified version of it.
The concept of ransomware is clearly making a comeback. During the past two months, scareware met the ransomware business model in the face of File Fix Professional 2009 and FakeAlert-CO or System Security, followed by two separate SMS-based ransomware variants Trj/SMSlock.A and a modified version of it.


































