 Some informative papers covering various aspects of analyzing and protecting against phishing attacks were made available at the beginning of this month, courtesy of this year's APWG eCrime Researchers Summit :
Some informative papers covering various aspects of analyzing and protecting against phishing attacks were made available at the beginning of this month, courtesy of this year's APWG eCrime Researchers Summit :"The Anti-Phishing Working Group eCrime Researchers Summit was conceived by APWG Secretary General Peter Cassidy in 2006 as a comprehensive venue for the presentation of the state-of-the-art basic and applied research into electronic crime, engaging every aspect of its development (technical, behavioral, social and legal) as well as technologies and techniques for its detection, related forensics and its prevention."
Papers presented include :
- Examining the Impact of Website Take-down on Phishing
- Fishing for Phishes: Applying Capture-Recapture to Phishing
- Evaluating a Trial Deployment of Password Re-use for Phishing Prevention
- Behavioral Response to Phishing Risk
- Fighting Obfuscated Spam
- A Comparison of Machine Learning Techniques for Phishing Detection
- Getting Users to Pay Attention to Anti-Phishing Education Continue reading →
 Following the recently released "Journey to the Heart of Internet Censorship" report, University of Toronto's Citizen Lab took advantage of the momentum and released a guide entitled "Everyone's Guide to By-Passing Internet Censorship" :
Following the recently released "Journey to the Heart of Internet Censorship" report, University of Toronto's Citizen Lab took advantage of the momentum and released a guide entitled "Everyone's Guide to By-Passing Internet Censorship" :"This guide is meant to introduce non-technical users to Internet censorship circumvention technologies, and help them choose which of them best suits their circumstances and needs."
Here's another interesting perspective that took event recently, the art of using censorship for economic warfare by stealing Internet traffic from the U.S and forwarding the loyal visitors to local Internet properties in China :"I’ve written previously on the possibility that China may use its firewall as an economic tool as opposed to a censorship tool alone, and although censorship may be partially behind todays blanket ban of US search sites, the redirect to Baidu would indicate an economic motive; if the Chinese Government were serious about censorship alone we would have reports of page not found/ blocked messages, not redirects to Baidu."
It's all a matter of perspective - privacy is just as vital to maintain in a democratic society, as is anonymity in a modern communism societies where f*** speech is a censored word by itself. Continue reading →
 In case you haven't come across it before, here's an informative blog whose objective is to track events related to the Russian Business Network (RBN) and expose its nodes in between :
In case you haven't come across it before, here's an informative blog whose objective is to track events related to the Russian Business Network (RBN) and expose its nodes in between :"Everything you wanted to know about the RBN and related enterprises - AKA ; Russian Business Network, RBNnetwork, RBusinessNetwork; the Internet Community's favorite - exploiters, phishers, hacks, spammers, etc."
Under the pressure put by the "wisdom of crowds" collective intelligence capabilities in analyzing pieces of the puzzle who make up the big picture in respect to the Russian Business Network, a representative of the RBN speaks out for the first time :
"We can't understand on which basis these organizations have such an opinion about our company," Tim Jaret of the Russian Business Network says in an e-mail interview. "We can say that this is subjective opinion based on these organizations' guesswork." Jaret's e-mail signature identifies him as working in RBN's abuse department. Security researchers and anti-spam groups say the St. Petersburg-based RBN caters to the worst of the internet's scammers, renting them servers used for phishing and malware attacks, all the while enjoying the protection of Russian government officials. A report by VeriSign called the business "entirely illegal."
What is the RBN at the bottom line? A diversified set of IP blocks located at different parts of world, who periodically appear within the deobfuscated javascipts of the sites who got IFRAME-ed and were found to serve malware by exploiting outdated browser vulnerabilities. What's more interesting to me than the "yet another popular site which got IFRAME-ed by the RBN's network" is the success of the popular malware exploitating kits using outdated and already patched vulnerabilities. What use are patches when no one is applying them, and aren't unpatched vulnerabilities just as effective as zero day ones? Yes, they are.
Issues to consider :
- the RBN offers bullet proof hosting upon signing some sort of contract, where they may easily forward the responsibility to the hoster of the malware, phishing and spamming, namely, on a contract basis those hosting such content violate their TOS agreement, now whether or not the RBN will remove them in a self-regulation manner or wait for an abuse letter to come, then delay it for couple of weeks while the campaign is still active is entirely different topic
- during the first couple of hours of the Bank of India hack, once vendors and researchers started assessing the site, the RBN IP that was used as redirector removed the javascript obfuscation and forwarded every visitor to Google.com. My point is that, unless real-time CYBERINT is collected by trusted parties, it would be very hard to come up with historical evidence on some of their malicious activities
- despite being a consolidated organization offering bullet proof hosting, they're still not fast-fluxing any of their services on a large scale, an indication of a botnet behind the fast-flux, and while they're just a couple of netblocks to filter, it could get more ugly and harder to trace back. So let's "appreciate" the RBN's laziness for the time being
- the RBN is the tip of the iceberg whose clients' successes in the form of embedding RBN IPs on the most recent malware cases led to the inevitable wisdom of crowds effect. What about the hundreds of thousands other not so well known malware serving netblocks?
What were some of the most recent cases where RBN IPs were used to serve malware? The Massive Embedded Web Attack in Italy used to orbit around RBN IPs, various other exploits serving domains and the fake ms-counter.com were using RBN IPs, Bank of India's IFRAME and several MPack control panels were pointing to RBN's network too, and also the most recent Beer.ch malware attack. It gets even more interesting.
Here are for instance some of the fake anti-virus and anti-spyware applications hosted at the Russian Business Network in the time of blogging. The applications are cute, little, tiny 35kb adwares :
malwarealarm.com - active - Adware.Spysheriff
xscanner.malwarealarm.com - active
scanner.malwarealarm.com - active
windowsafesurf.com - 403 forbidden
spy-shredder.com - Adware.Spysheriff
scanner.spy-shredder.com - active
proantivirus.net - expired
dragracers.biz - VirusBurst
antivermins.com - Application.Antivermins.B / Virus.Win32.Spycrush.B
adwareremover2007.com - Adware.Spysheriff
The enemy you know is better than the enemy you don't know, but on a large scale I fear the enemy I don't know, namely the hundreds of thousands script kiddies now empowered with open source and localized malware kits. Here are two more related blog posts on the RBN as well. Continue reading →
 In the past, malware interested in establishing a one-to-one social engineering communication channel with potential victims, used to crawl the hard drive, even the web address book of the infected party looking for emails to self-email the binary to. And with the rise of instant messaging communications, malware authors adapted old techniques such as harvesting for emails to IM communications by introducing IM screen names harvesting and positioning the practice as both a product in the form of the segmented email databases of millions of emails already harvested, and as a service, by aggregating publicly available profile data to deliver targeted messages often in the form of phishing, malware embedded URLs, and spam. Hitlist's based malware is nothing new, it's actually malware authors borrowing the spammers "direct marketing" communication model, and while you cannot change your email's account name unless of course you're using a disposable or temporary email service, you can easily, in fact periodically change your screen name.
In the past, malware interested in establishing a one-to-one social engineering communication channel with potential victims, used to crawl the hard drive, even the web address book of the infected party looking for emails to self-email the binary to. And with the rise of instant messaging communications, malware authors adapted old techniques such as harvesting for emails to IM communications by introducing IM screen names harvesting and positioning the practice as both a product in the form of the segmented email databases of millions of emails already harvested, and as a service, by aggregating publicly available profile data to deliver targeted messages often in the form of phishing, malware embedded URLs, and spam. Hitlist's based malware is nothing new, it's actually malware authors borrowing the spammers "direct marketing" communication model, and while you cannot change your email's account name unless of course you're using a disposable or temporary email service, you can easily, in fact periodically change your screen name. IM networks are on the other hand, slowly adopting a "save the world from the clicking crowd" security awareness model by blocking common malicious file and domain extensions, an initiative that's both applaudable and futile at the same time given the failure of URL filtering in today's dynamic and user-generated content Web. Go through an informative article by ScanSafe's Dan Nadir with comments on Signature-based detection, Heuristics, Code Analysis, Code reputation, URL Reputation, and Traffic Behavioral Analysis.
Continue reading →
IM networks are on the other hand, slowly adopting a "save the world from the clicking crowd" security awareness model by blocking common malicious file and domain extensions, an initiative that's both applaudable and futile at the same time given the failure of URL filtering in today's dynamic and user-generated content Web. Go through an informative article by ScanSafe's Dan Nadir with comments on Signature-based detection, Heuristics, Code Analysis, Code reputation, URL Reputation, and Traffic Behavioral Analysis.
Continue reading →
 It is logical to consider the possibility that once a malware author starts evaluating the benefits out of releasing a malware in an open source form, malware exploitation kits can also build communities around them. Since August, 2007, Chinese hacking groups can freely enjoy "the benefits" of IcePack's and MPack's malicious economies of scale attacking approach in the combination of a brain-damaging Keep It Simple Stupid exploitation tactic in the form of serving exploit URLs, which get automatically embedded via a web application bug, or via automated remote file inclusion enabled web site.
It is logical to consider the possibility that once a malware author starts evaluating the benefits out of releasing a malware in an open source form, malware exploitation kits can also build communities around them. Since August, 2007, Chinese hacking groups can freely enjoy "the benefits" of IcePack's and MPack's malicious economies of scale attacking approach in the combination of a brain-damaging Keep It Simple Stupid exploitation tactic in the form of serving exploit URLs, which get automatically embedded via a web application bug, or via automated remote file inclusion enabled web site. Let's once again emphasize on the research question of wouldn't such malware kits and tools have a higher value if kept private, and why someone release them in the wild? Couple of months ago, the tools themselves were used as a bargain for improving the UVP (unique value proposition) on a large scale, that's of course until they became a commodity. From my perspective, all warfare is based on deception, especially infowar, namely, if the idea of embedding an exploiting serving URL at a popular site in order to infect all of its visits becomes a commodity as an attack tactic, at the end it will be the ones whose fast-fluxing, javascript obfuscation, and timely crypting and rotating the malware binary skills will put them in a market leader position, where the new entrants, the ones cheering for having access to such tools will make the headlines, like the default malware kit installation wannabies they are.
Let's once again emphasize on the research question of wouldn't such malware kits and tools have a higher value if kept private, and why someone release them in the wild? Couple of months ago, the tools themselves were used as a bargain for improving the UVP (unique value proposition) on a large scale, that's of course until they became a commodity. From my perspective, all warfare is based on deception, especially infowar, namely, if the idea of embedding an exploiting serving URL at a popular site in order to infect all of its visits becomes a commodity as an attack tactic, at the end it will be the ones whose fast-fluxing, javascript obfuscation, and timely crypting and rotating the malware binary skills will put them in a market leader position, where the new entrants, the ones cheering for having access to such tools will make the headlines, like the default malware kit installation wannabies they are.  By ensuring that the market segment for malware in this case, has many participants and is not concentrated and operated by a few over-performing groups is a highly beneficial from the perspective of the most skilled and advanced groups continuing their operations in between the noise generated by the rest of market challengers. Now Playing in Cyberspace - "The Revenge of the Chinese Script Kiddies".
By ensuring that the market segment for malware in this case, has many participants and is not concentrated and operated by a few over-performing groups is a highly beneficial from the perspective of the most skilled and advanced groups continuing their operations in between the noise generated by the rest of market challengers. Now Playing in Cyberspace - "The Revenge of the Chinese Script Kiddies". Spam and phishing are indeed starting to operate behind the curtains of a fast-flux network of constantly changing IPs of malware infected PCs that end up hosting the scams and phishing pages themselves for a certain period of time. And I'm certain that's a trend and not a fad given the potential for increasing the average time a phishing or a scam site remains online, even the inability prove a certain IP was hosting it at a given period.
Spam and phishing are indeed starting to operate behind the curtains of a fast-flux network of constantly changing IPs of malware infected PCs that end up hosting the scams and phishing pages themselves for a certain period of time. And I'm certain that's a trend and not a fad given the potential for increasing the average time a phishing or a scam site remains online, even the inability prove a certain IP was hosting it at a given period. Take for instance the latest Canadian Pharmacy spam campaign, where in between the fast-flux, they didn't even bother to register and use a legitimate SSL certificate, among the few visual proofs for the average end user that's ensuring a certain degree of security, yet, in order to establish more trust, dead link logos such as "Verified by Visa", "Secured by GeoTrust", "ScanAlert - Hacker Safe", and "Verisign" are included at the processing order page. To me, that's a typical Rock Phish mentality - efficiency vs quality of the phishing/scam campaign. The whole Canadian Pharmacy spam campaign is behind an affiliate program forwarding the responsibility for promotion (spamming) and fast-fluxing, to the participants.
Continue reading →
Take for instance the latest Canadian Pharmacy spam campaign, where in between the fast-flux, they didn't even bother to register and use a legitimate SSL certificate, among the few visual proofs for the average end user that's ensuring a certain degree of security, yet, in order to establish more trust, dead link logos such as "Verified by Visa", "Secured by GeoTrust", "ScanAlert - Hacker Safe", and "Verisign" are included at the processing order page. To me, that's a typical Rock Phish mentality - efficiency vs quality of the phishing/scam campaign. The whole Canadian Pharmacy spam campaign is behind an affiliate program forwarding the responsibility for promotion (spamming) and fast-fluxing, to the participants.
Continue reading →
 Yet another publicly available DIY malware dropper this time courtesy of German compared to Russian malware crews, whose releases on the other hand are starting to live in a "high profit margins only" product/service business model, thus introducing propriatery malware tools like the ones I've discussed in a previous post. Why would a malware crew member release such a tool for free? Respect, ego, quota of tools released to meet in order to remain inside the team? Could be, but on several occasions such freely available tools get backdoored too, like just the source codes for popular malware kits.
Yet another publicly available DIY malware dropper this time courtesy of German compared to Russian malware crews, whose releases on the other hand are starting to live in a "high profit margins only" product/service business model, thus introducing propriatery malware tools like the ones I've discussed in a previous post. Why would a malware crew member release such a tool for free? Respect, ego, quota of tools released to meet in order to remain inside the team? Could be, but on several occasions such freely available tools get backdoored too, like just the source codes for popular malware kits.You often hear that anti virus software is dead, that vendors end up their with quarters with meaningless percentage increases in every malware segment, meaningless in respect to the DIY trend. The idea has its pros and cons, no doubt about it, however it should orbit around different research questions such as :
- which AVs are more ineffective, the ones which are not running due to the process list of each and every anti virus software now easily integrated within each and every malware dropper and malware tool in the wild?
- or the ones whose often static update locations online get blocked by a malware in in order to prevent its detection supposedely to come in the next signatures update?
Here're related overviews of malware tools. Continue reading →
 The Global Security Challenge have just announced the world's five most promising security startups chosen to compete at the GSC Final in London for a $500K grant this November. They are:
The Global Security Challenge have just announced the world's five most promising security startups chosen to compete at the GSC Final in London for a $500K grant this November. They are:- Auxetix (UK) - fortifies protection against multiple explosions through helical-auxetic nets
- EyeMarker (USA) - scans the eye to rapidly and non-invasively assess a person's health
- NoblePeak Vision (USA) - enabling the rapid detection and identification of people and objects at night without active illumination
- Psylock (Germany) - identifies users through biometric analysis of typing behavior
- XID Technology (Singapore) - face synthesis technology for real-time 3D rediction/replacement in a 2D video
Disintermediating the main sources of R&D with innovation and cost-effectiveness in mind, is a business practice that's already embraced by numerous deep pocketed future clients interested in outsourcing innovation in the form of such contests. I'm particularly interested in Psylock's future development, and it's great to note that the folks behind this typing behavior authentication even set up a demo of the concept.
And given that the GSC are also embracing the blogosphere, let's wish them long-term passion and sustained professionalism in their initiative to fund promising security oriented startups. Continue reading →
 What's the future of spam? Spammers breaking CAPTCHAs of legitimate email providers and take advantage of their clean IP reputation to send out their junk, or spammers cooperating with botnet masters supplying newly infected hosts? Try outsourcing as a concept by renting a "managed spamming appliance" like the ones advertised as of recently.
What's the future of spam? Spammers breaking CAPTCHAs of legitimate email providers and take advantage of their clean IP reputation to send out their junk, or spammers cooperating with botnet masters supplying newly infected hosts? Try outsourcing as a concept by renting a "managed spamming appliance" like the ones advertised as of recently.This is an automatically translated excerpt from a recent proposition for a newly developed spam system that comes in the form of hardware with embedded botnet, just consider the idea for a second before reading and you'll get the point :
Among spammers very agreement that spam has become a profitable and die their last months, years. And it is understandable: profit fell, suppliers downloads expensive prices almost to the size of profits, a dozen well-known and had a good year or two ago turnover spammers departed from the market, so even monsters flow of spam once died theme ran in the stream than definitive did the topic boring.
I am pleased to present to you the technology that will make your distribution more efficient and voskresit characteristic of the spam profits.
Our software allows you spamit in such quantities that letter competitors simply lost among your. Also you get tools to control the delivery of letters and inboks spam those domains that are not being held by any other spam.
We have reached the maximum speed possible with the distribution of each bot and defended it against possible anti-virus and firewalls. In doing so, your botnety invincible. Interesting? And now in more detail.
Overall software works like any other botmeyler. Botnet controlled part of a server, it created letters and mailing bases loaded. Botha knocking over the job to a server, get a piece base, and a letter vdohnovlenno spamyat until the turn will come next door for the job.
Each server keeps 2500 + online bots, and the maximum speed reaches 7000 mailing letters per second, is the highest speed of all current market spam systems. Of course, the speed depends largely on the quantity and quality of downloads, quality and type of database (country, large domains, etc). 2500 online for you too little? No problem. Berit 2, 5, 10 servers, as long as you want.
In our system, there is every possible means to randomise from any randomise texts finishing randomnyh generate images on the fly or finished morphing images, as well as the ability to create their own makro-skripty. You can independently create and edit headers (if there is time to do so, fresh headlines you will download our spam-inzhenery).
You can do so zarandomlennye letter, as far themselves want. After randomization letter, you can immediately check finished look and see the results of the verification Spam Assasin ohm.
For specific newsletters (probiv major domains, etc), there is a possibility in detail settings bots (different types of reactions to the texts of error codes and mail servers). You can customize the system to thin to work with certain domains to improve the quality and speed of spam to these domains, identifying the individual parameters for each domain (how many letters it takes for a session timeouts, own blacklist bots, enter special codes for SMTP session for given domain, etc.)
To avoid zamorachivatsya processing bases on a separate server, all options included in the processing software. Among them: removal from the database of addresses abuzerov, splitting bases on the large and normal domains merger bases subtraction bases and checking for uniqueness.
24 hours a day, 7 days a week, you can use the services tehpodderzhki and complex issues of sending spam to discuss with our engineers. In addition, you can order the service "personal manager" who will help draw up a letter to monitor the continuous distribution, will help choose the supplier of downloads and decide on the overall strategy for working with partnerkami. The main advantages :
1. The speed and delivery. Average up-to medium-speed downloads of 1.5 letters per second from one spamyaschego bots, 2 to bots spamyat at speeds of 3000 letters per second, equal to 10 leading to millions of messages delivered per hour. This average figures for good loading each bot could spamit up to 3.5 letters per second.
2. The persistence of bots. Botha bypass all the latest version of anti-virus and faervollov, including the latest version of Zone Alarm, Outpost, Kaspersky, and the bot rigidly set in the system so that they are impossible to remove, even in safe mode. All innovation and refinement, we test drivers bots not only stands the test on different versions of the OS, but also on actual downloads from various suppliers. Cleaning loadera happens every day.
3. Convenience work, and further opportunities for constant refinement. We make the process convenient and efficient spam, the whole routine in the most automated, the time our customers spend at statov refresh. However, if you or your staff would like to have enough knowledge to extract the maximum from their bots and bases, you have a beautiful high-tech istrument it may izmennie any settings.
4. Business centers, skilled technical support. Complex program complex, which is fully explored - unique challenge, our support team will help you in any questions and solve any problems.
5. Flexible pricing policy. Our command is spam many years in different directions, and our customers are top-sellerami many partnerships programs we are familiar with the process of naslyshke not spam. With this experience and knowledge, we do your business more stable and profitable. Our tariff plans:
1-2 servers - $ 4000 per server
3-5 servers - $ 3000 per server
Let's summarize the key points :
- a "spamming appliance" comes with 2500+ zombie bots, capable of sending 7000 emails per second
- built-in verification for detection against common spam scoring systems
- managed anti virus bypassing capabilities and signatures based detection
- technical support
What's next to come? Possibly a USB stick with built-in C&C to a botnet with full admin rights. Continue reading →
 Reporters Without Borders just released their latest report on China's Internet Censorship practices, outlining how exactly bureaucracy intersects with technology, perhaps the worst combination I could think of :
Reporters Without Borders just released their latest report on China's Internet Censorship practices, outlining how exactly bureaucracy intersects with technology, perhaps the worst combination I could think of :"The report also documents how the Beijing Internet Information Administrative Bureau has in practice asserted its daily editorial control over the leading news websites based in the nation’s Capital. It gives many examples of the actual instructions issued by officials in charge of this bureau. The last part of the report gives the results of a series of tests conducted with the mechanism of control through filtering keywords. These tests clearly show that, though there are still many disparities in the levels of censorship, the authorities have successfully coerced the online media into submission to censor themselves heavily on sensitive subjects."
Information is not free, but it just wants to be free and you cannot control the rules of curiosity and the basic right to know who's what and what's when -- even if you shut down the Internet access inside the country. China's Internet censorship is on the other hand a driving force for academic research across the globe. Even wondered what are the latest blocked keywords discovered filtered over time? Try the list of blacklisted keywords discovered by ConceptDoppler, as of 19 Sep 2007, part of the ConceptDoppler project - A Weather Tracker for Internet Censorship.
Related posts:
Twisted Reality
China - the biggest black spot on the Internet’s map
Chinese Internet Censorship efforts and the outbreak
Securing Political Investments Through Censorship
World's Internet Censorship Map
China's Interest of Censoring Mobile Communications
South Korea's View on China's Media Control and Censorship
China's Internet Censorship Report 2006
Media Censorship in China - FAQ
Google and Yahoo's Shareholders Against Censorship
It's all About the Vision and the Courage to Execute it
Gender Based Censorship in the News Media
Real Time Censored URL Check in China
Censoring Flickr in China Continue reading →
 Before January 2007, I could only say that I'm glad to have you as a reader of this blog, but with the Talkr-ization of my blog during that month, I can now freely say I'm also glad to have you as both, a reader and a listener taking into consideration the interest in the audio versions of my analyses. It's great to follow the progress of the service and the efforts the folks behind it put into improving its quality. I can only hope that they reach Ms. Dewey's speech engine, even go beyond it by allowing customization in the form of different voices to choose from.
Before January 2007, I could only say that I'm glad to have you as a reader of this blog, but with the Talkr-ization of my blog during that month, I can now freely say I'm also glad to have you as both, a reader and a listener taking into consideration the interest in the audio versions of my analyses. It's great to follow the progress of the service and the efforts the folks behind it put into improving its quality. I can only hope that they reach Ms. Dewey's speech engine, even go beyond it by allowing customization in the form of different voices to choose from. "MoFuse is short for Mobile Fusion. MoFuse was founded in July of 2007 and released it's first private beta in late September of 2007. MoFuse allows content publishers to create RSS driven mobile sites and gives our users the ability to control almost every aspect of the design using some of our AJAX features."
"MoFuse is short for Mobile Fusion. MoFuse was founded in July of 2007 and released it's first private beta in late September of 2007. MoFuse allows content publishers to create RSS driven mobile sites and gives our users the ability to control almost every aspect of the design using some of our AJAX features." As I pointed out in my last series of posts assessing pharmaceutical scams and phishing campaigns, both, botnet masters, pharma masters, and rock phishers, are starting to take advantage of fast-flux networks to make it harder to trace back and shut down their operations. Here's a related article on the topic :
As I pointed out in my last series of posts assessing pharmaceutical scams and phishing campaigns, both, botnet masters, pharma masters, and rock phishers, are starting to take advantage of fast-flux networks to make it harder to trace back and shut down their operations. Here's a related article on the topic : Let's showcase this emerging trend. Take for instance some recently spammed .cn domains such as considerjust.cn and pageagainst.cn advertising a Canadian Pharmacy scam. The domains have an allocated space of IPs to rotate on each and every request to them, something you can easily verify by pinging them and see how their IPs change on every new ping in coordination with the allocated IP table you can see in the screenshot. It gets even more interesting, especially in terms of locating the main fast-flux domain, in this case it's mainseven.com, a central point for a great deal of other pharma domains in its fast-flux. Here are graphs of fast-flux spam and scam networks :
Let's showcase this emerging trend. Take for instance some recently spammed .cn domains such as considerjust.cn and pageagainst.cn advertising a Canadian Pharmacy scam. The domains have an allocated space of IPs to rotate on each and every request to them, something you can easily verify by pinging them and see how their IPs change on every new ping in coordination with the allocated IP table you can see in the screenshot. It gets even more interesting, especially in terms of locating the main fast-flux domain, in this case it's mainseven.com, a central point for a great deal of other pharma domains in its fast-flux. Here are graphs of fast-flux spam and scam networks :





As in every other competitive industry, pretty much all the market participants such as botnet masters, pharma masters, spammers and scammers, follow what the others are doing and by taking notice in which practices the others outperform them, figure out how to apply them within their practices at a later stage - competitive benchmarking within the underground ecosystem is already a fact. Continue reading →
 Wish it was the average .cn domain I'm referring to, in this case it's the web sites of three U.S towns, namely the City of Chetek, Winsonsin, the City of Somerset, Texas and Town of Norwood, Massachusetts, who are the latest victims of embedded malware and blackhat SEO injected within their juicy from a blackhat SEO perspective .gov tld extensions.
Wish it was the average .cn domain I'm referring to, in this case it's the web sites of three U.S towns, namely the City of Chetek, Winsonsin, the City of Somerset, Texas and Town of Norwood, Massachusetts, who are the latest victims of embedded malware and blackhat SEO injected within their juicy from a blackhat SEO perspective .gov tld extensions.Apparently, malicious parties managed to compromise City of Chetek's official site and created several subdomains with URLs consisting of spam redirecting to the downloader's page :
 st-3.x.cityofchetek-wi.gov/porn/st3/502.html
st-3.x.cityofchetek-wi.gov/porn/st3/502.htmlst-3.x.cityofchetek-wi.gov/porn/st3/537.html
st-2.x.cityofchetek-wi.gov/porn/st2/322.html
2k.x.cityofchetek-wi.gov/porn/2k-003/1618.html
st-2.x.cityofchetek-wi.gov/porn/st2/409.html
The following URLs redirect to the downloader : freeclipoftheday.com/movie1.php?id=4154&n=teens&border=FFFFFF&bgcolor=000000
Detection rate : Result: 9/32 (28.13%)
File size: 75771 bytes
MD5: a74b09c7e6ca828ec0382c4f4f234bac
SHA1: 2861a4215dd2a579afe1e30372e05d2ea00223f2
 City of Somerset, Texas official site is also embedded with the same blackhat SEO content structure, which leads me to the conclusion that these two are related :
City of Somerset, Texas official site is also embedded with the same blackhat SEO content structure, which leads me to the conclusion that these two are related :2k.x.somersettx.gov/porn/2k-004/156.html
2k.x.somersettx.gov/porn/2k-004/313.html
2k.x.somersettx.gov/porn/2k-004/829.html
2k.x.somersettx.gov/porn/2k-004/830.html
st-5.x.somersettx.gov/porn/st5/103.html
 Town of Norwood, Massachusetts :
Town of Norwood, Massachusetts :sql.norwood-ma.gov/libraries/transformations/.dir/132/valium-cost.html
Several more high profile sites hosting such scams I came across to yesterday are NASA's Worldwind, and the State of New Jersey that used to historically host such pages :
issues.worldwind.arc.nasa.gov/secure/attachment/10781/Buy-Valium.html
issues.worldwind.arc.nasa.gov/secure/attachment/10800/Valium.html
issues.worldwind.arc.nasa.gov/secure/attachment/10791/Panasonic-Ringtone.html
nj.gov/education/voc/9/2007/
nj.gov/education/voc/9/2007/viagra/viagra-online.html
nj.gov/education/voc/9/2007/zoloft/buy-zoloft-online.html
nj.gov/education/voc/9/2007/tramadol/discount-tramadol.html
Just yesterday for instance, F-Secure discovered a phishing page hosted at India's Police Academy site, and
Sunbelt pointed out that Beer.ch got IFRAME-ed with the following URLs belonging to the Russian Business Network who also IFRAME-ed Bank of India once :
81.95.149.74/1/index.php
How is all this happening? In both, automated, and sometimes targeted way, where automated stands for remote file inclusion through botnets.
I sure know all the pharmaceutical blockbusters now.
Related posts:
Bank of India Serving Malware
U.S Consulate in St.Petersburg Serving Malware
Syrian Embassy in London Serving Malware
CISRT Serving Malware
 Sometimes, it's unbelievable how easy is in fact to social engineer people on their way to "make a deal" online, especially when buying pharmaceuticals online. Let's discuss organized pharmaceutical scams the way I perceive them, which like phishing also aim at reaching the efficiency level.
Sometimes, it's unbelievable how easy is in fact to social engineer people on their way to "make a deal" online, especially when buying pharmaceuticals online. Let's discuss organized pharmaceutical scams the way I perceive them, which like phishing also aim at reaching the efficiency level.It's a public secret that Amazon.com's success in terms of sustained profitability has to do with their affiliation based model, namely "let the others do the sale for you". Pharmaceutical scammers have been anticipating this model for quite some now, a model where the pharma masters forward the processes of collecting potential customers (emails harvesting), contacting them and letting them know of how cheap their pharmaceutical are (spamming), enticing them to initiate a transaction with a fancy and professionally looking like site (freely available pharmacuitical web site templates) to those who become part of an affiliate network like the one you can see in the screenshot.
 Pharmaceutical scammers have their own fast-flux networks of constantly changing domain and IP addresses, shared hosting of multiple scams in different segmets. Remember meds247.org? It's still up and running but the javascript obfuscation I reviewed before is now pointing to web server's directory whose main index hosts a p0rn site - center4cares.com, so you have a p0rn site that's hosting viagra propositions - "insightful". Moreover, pharmacuitical scam campaigns are also known to use free web space providers as doorway pages in the form of redirectors. For instance, the most recent spamming campaign promoting a Canadian Pharmacy scam located at rxlovecaptain.com, is taking advantage of the already established trusted brand of Geocities to redirect the spammers users to the main page :
Pharmaceutical scammers have their own fast-flux networks of constantly changing domain and IP addresses, shared hosting of multiple scams in different segmets. Remember meds247.org? It's still up and running but the javascript obfuscation I reviewed before is now pointing to web server's directory whose main index hosts a p0rn site - center4cares.com, so you have a p0rn site that's hosting viagra propositions - "insightful". Moreover, pharmacuitical scam campaigns are also known to use free web space providers as doorway pages in the form of redirectors. For instance, the most recent spamming campaign promoting a Canadian Pharmacy scam located at rxlovecaptain.com, is taking advantage of the already established trusted brand of Geocities to redirect the spammers users to the main page :
geocities.com/AishaDeleon78
geocities.com/CarsonNguyen93
If efficiency truly matters from a scammer's perspective, we may soon witness actual DIY marketing packages with templates, "collection of potential customers", and a list of services to use when "contacting them". Now, if the pharma masters want to diversify as well, they can vertically integrate by owning or renting the spamming services themselves, something I haven't come across to - yet.
 The majority of Rock Phish campaigns usually take advantage of a single domain that's hosting numerous different phishing scams targeting different financial organizations. However, another trend is slowly emerging and that is the development of phishing domain farms, either taking advantage of a shared hosting as you can see in the graph on the left, or fast-fluxing the campaigns to increase the average time a phishing site remains online. Here's the interesting part acting as proof on the emerging trend of so called malicious economies of scale, and also, showcasing Rock Phish's effiency vs security trade off due to the centralization of the campaign on a single IP only. In this campaign we see a single IP (200.77.213.15) hosting 38 rock phish domains, that on the other hand in a typical Rock Phish style host multiple phishing pages targeting different companies.
The majority of Rock Phish campaigns usually take advantage of a single domain that's hosting numerous different phishing scams targeting different financial organizations. However, another trend is slowly emerging and that is the development of phishing domain farms, either taking advantage of a shared hosting as you can see in the graph on the left, or fast-fluxing the campaigns to increase the average time a phishing site remains online. Here's the interesting part acting as proof on the emerging trend of so called malicious economies of scale, and also, showcasing Rock Phish's effiency vs security trade off due to the centralization of the campaign on a single IP only. In this campaign we see a single IP (200.77.213.15) hosting 38 rock phish domains, that on the other hand in a typical Rock Phish style host multiple phishing pages targeting different companies. In reality, Rock Phish is a script taking advantage of the now commoditized phishing pages of each and every web property and company that is a potential victim, hosted on a single domain in order to achieve efficiency. Once the script and the phishing pages are in the wild, the entry barriers into phishing scams become significantly lower allowing novice phishers to easily launch what used to a professional phishing campaign much easier than ever.
In reality, Rock Phish is a script taking advantage of the now commoditized phishing pages of each and every web property and company that is a potential victim, hosted on a single domain in order to achieve efficiency. Once the script and the phishing pages are in the wild, the entry barriers into phishing scams become significantly lower allowing novice phishers to easily launch what used to a professional phishing campaign much easier than ever. Continue reading →
 Malicious Culture of Participation
Malicious Culture of ParticipationDoS battle stations operational in the name of the "Please, input your cause". Preventing a malware infection in order to limit the possibility for the host to become part of a botnet that will later one start a large scale DDoS attack is such a rational thinking that information warriors truly understanding what information warfare is all about, tend to undermine. The recently discussed "people's information warfare" concept highlighting China's growing interest in the idea, is a great example of a culture of participation orbiting around hacktivism cause, a culture we've also seen in many other hacktivism tensions in the past, and will continue to see in the future. The entire concept is relying on the fact that the collective bandwidth of people voluntarily "donating" it, is far more efficient from a "malicious economies of scale" perspective, compared to for instance the botnet masters having to create the botnet by infecting users in one way or another. Moreover, empowering an average Internet user with diversified DoS capabilities is directly increasing the nation's asymmetric warfare capabilities in an event of a hacktivism war.
Furthermore, the majority of DoS or DDoS flooding tools have a relatively high detection rate, but when people
 want to use them, they'll simply turn off their anti virus software, the one they use to prevent malware infections, but in a "people's information warfare" they can go as far as consciously becoming a part of a hacktivism centered botnet. Take this DoS tool featured in the screenshot for instance, it has a high detection rate only if the anti virus software is running, but in situation where a "malicious culture of participation" is the desired outcome it doesn't really matter. Donating their bandwidth and pretending to be malware infected is far more dangerous than botnet masters acquiring DDoS capability by figuring out how to infect the massess. It's one thing to operate a botnet and direct it to attack a certain site, and entirely another to be infected with a malware that's DDoS-ing the site, a situation where you become an "awakened and fully conscious zombie host".
want to use them, they'll simply turn off their anti virus software, the one they use to prevent malware infections, but in a "people's information warfare" they can go as far as consciously becoming a part of a hacktivism centered botnet. Take this DoS tool featured in the screenshot for instance, it has a high detection rate only if the anti virus software is running, but in situation where a "malicious culture of participation" is the desired outcome it doesn't really matter. Donating their bandwidth and pretending to be malware infected is far more dangerous than botnet masters acquiring DDoS capability by figuring out how to infect the massess. It's one thing to operate a botnet and direct it to attack a certain site, and entirely another to be infected with a malware that's DDoS-ing the site, a situation where you become an "awakened and fully conscious zombie host". Examples of the "People's Information Warfare Concept" :
Examples of the "People's Information Warfare Concept" :- During the China/U.S hacktivism tensions in 2001 over the death of a Chinese pilot crashing into an AWACS, Chinese hacktivists released mail bombers with pre-defined U.S government and military emails to be attacked, thus taking advantage of the people's information warfare concept
- The release of the Muhammad cartoons had its old-school hacktivism effect, namely mass defacements of Danish sites courtesy of Muslim hacktivists to achieve a decent PSYOPS effect online and in real-life
- The Israel vs Palestine Cyberwars is a great example of how DIY web site defacement tools were released from both sites which resulted in a web vulnerabilities audit of the entire web space they were interested in defacing to spread hacktivism propaganda
- Cyber jihadists taking advantage of the "people's information warfare" concept by syndicating a list of sites to be attacked from a central location, and promoting the use of a Arabic themed DoS tool against "infidel" supporting sites
- What exactly happened during Russia's and Estonia's hacktivism tensions? The voting poll that is still available indicates that people believe it was botnet masters with radical nationalism modes of thinking. But judging from the publicly obtainable stats, ICMP often comes in the form of primitive DIY DoS tools compared to the more advanced attacks for instance. Collectivist societies do not need coordination because they know everyone else will do it one way or another.
Power to the people.
 UPDATE:
UPDATE:Turkish hackers target Swedish Web sites - "Hackers in Turkey have attacked more than 5,000 Swedish Web sites in the past week, and at least some of the sabotage appears linked to Muslim anger over a Swedish newspaper drawing that depicted the Prophet Muhammad's head on a dog's body. Around 1,600 Web sites hosted by server-provider Proinet and 3,800 sites hosted by another company have been targeted, Proinet spokesman Kjetil Jensen said Sunday. Jensen said hackers, operating on a Turkish network, at times replaced files on the sites with messages."
Continue reading →
 Given that spammers and phishers are already breaking, bypassing our outsourcing their CAPTCHA breaking needs, the introduction of a DIY (do-it-yourself) model provided confidence in the recognition process is over 80%, was inevitable. The CAPTCHA Bot is a good example of a recently released DIY CAPTCHA breaking service where the users feed their accounts with credits, sets URLs and CAPTCHA's to get recognized. If it were pitched at vendors or anyone out there maintaining a CAPTCHA as a service it would have been a great idea, trouble is, it would be largely abused in its current form. Let's discuss the incentives model. Are developers of CAPTCHAs interested in improving the security of their CAPTCHAs in the form of contests with financial rewards or job propositions for those who dare to break them in a contest form? Not necessarily, and fixing vulnerabilities whenever such appear is done in an "on demand" fashion like we've seen with Vladuz's Ebay CAPTCHA populator. CAPTCHAs at the most popular web services are the gatekeepers of their online reputation, else, the flood of splogs and malware embedded blogs, as well as spam and phishing emails coming from free web based email providers may outpace the current model.
Continue reading →
Given that spammers and phishers are already breaking, bypassing our outsourcing their CAPTCHA breaking needs, the introduction of a DIY (do-it-yourself) model provided confidence in the recognition process is over 80%, was inevitable. The CAPTCHA Bot is a good example of a recently released DIY CAPTCHA breaking service where the users feed their accounts with credits, sets URLs and CAPTCHA's to get recognized. If it were pitched at vendors or anyone out there maintaining a CAPTCHA as a service it would have been a great idea, trouble is, it would be largely abused in its current form. Let's discuss the incentives model. Are developers of CAPTCHAs interested in improving the security of their CAPTCHAs in the form of contests with financial rewards or job propositions for those who dare to break them in a contest form? Not necessarily, and fixing vulnerabilities whenever such appear is done in an "on demand" fashion like we've seen with Vladuz's Ebay CAPTCHA populator. CAPTCHAs at the most popular web services are the gatekeepers of their online reputation, else, the flood of splogs and malware embedded blogs, as well as spam and phishing emails coming from free web based email providers may outpace the current model.
Continue reading →
 The Chinese Internet Security Response Team is reporting that it has found embedded IFRAMEs serving malware within some of its pages. And despite that the blog itself is now clean, Trend Micro are pointing out that the main index is still IFRAME-ed and that the attackers took advantage of the momentum during China's "Golden Week" holiday.
The Chinese Internet Security Response Team is reporting that it has found embedded IFRAMEs serving malware within some of its pages. And despite that the blog itself is now clean, Trend Micro are pointing out that the main index is still IFRAME-ed and that the attackers took advantage of the momentum during China's "Golden Week" holiday.IFRAMEs at the main index lead to :
js.users.51.la/392481.js
51.la/?392481
img.users.51.la/392481.asp
IFRAMEs at the blog used to point to :
mms.nmmmn.com/99913.htm
mms.nmmmn.com/30000.htm
mms.nmmmn.com/11122.htm
and ganbibi.com - where the twenty password stealers for online games located at ads.ganbibi.com/100.exe to ads.ganbibi.com/120.exe in numerical order are still active.
Related posts:
Bank of India Serving Malware
U.S Consulate St. Petersburg Serving Malware
Syrian Embassy in London Serving Malware Continue reading →
 The Underground Economy's Supply of Goods and Services
The Underground Economy's Supply of Goods and Services The concept of proprietary malware tools is a very interesting one mainly because the coders of the malware tools are exercising control over the supply and distribution of the malicious goods in order to earn a higher return on investment, and ensure the customer gets the best product ever, one that must remain undetected for as long as possible. In respect to the distribution, it's sort of a self-regulation issue mainly because the buyer that spent a significant amount of money to obtain the latest malware tool will not leak it online and turn it into a commodity. As for the seller, he's ensuring that the tool will be sold to, for instance, five different people, no more and no less, since the perceived value and coder-added exclusiveness will result in a very high profit margin.
The concept of proprietary malware tools is a very interesting one mainly because the coders of the malware tools are exercising control over the supply and distribution of the malicious goods in order to earn a higher return on investment, and ensure the customer gets the best product ever, one that must remain undetected for as long as possible. In respect to the distribution, it's sort of a self-regulation issue mainly because the buyer that spent a significant amount of money to obtain the latest malware tool will not leak it online and turn it into a commodity. As for the seller, he's ensuring that the tool will be sold to, for instance, five different people, no more and no less, since the perceived value and coder-added exclusiveness will result in a very high profit margin.
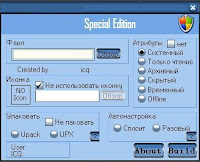 The market gets even more dynamic with the possibility for the buyer to exchange the malware tool he obtained at the over-the-counter market, and by doing so to limit the tool's exclusiveness, risk to have its value come close to zero if it leaks online, and most interestingly, his actions would have a butterfly effect on the other four people that hypothetically paid a higher profit margin price to obtain it. Given that the seller is interested in a higher profit margin only, he could either increase it and sell it to less than five people thinking that the less people have it the lower the chance it will leak or get exchanged, or if customer satisfaction and long-term relationships matter come up with a strategy on how to ensure the tools remain exclusive, though educating his customers for instance.
The market gets even more dynamic with the possibility for the buyer to exchange the malware tool he obtained at the over-the-counter market, and by doing so to limit the tool's exclusiveness, risk to have its value come close to zero if it leaks online, and most interestingly, his actions would have a butterfly effect on the other four people that hypothetically paid a higher profit margin price to obtain it. Given that the seller is interested in a higher profit margin only, he could either increase it and sell it to less than five people thinking that the less people have it the lower the chance it will leak or get exchanged, or if customer satisfaction and long-term relationships matter come up with a strategy on how to ensure the tools remain exclusive, though educating his customers for instance.Images of crypters and joiners are samples of currently available proprietary malware tools for sale.


RSS Feed