
ConsumerAffairs.com did a great job in summarizing the
top 10 scams of 2006 "
from the roughly 50,000 consumer complaints we've processed in the past year". Here's what the gullible consumer complains about :
01. Fake Lottery ScamConsumerAffairs.com reported on one case in which an elderly Kansas man lost over $300,000. You should have Asked Merrill to point you to the "tickets" with the highest probability of success, but it's too late for you now. Baby booming gullibility in action.
02. Phishing-Vishing ScamsI'm very surprised it's the second and not the first complain, but how come? Consumers aren't even aware they got scammed at the first place. Do
yourself a favour, and don't discuss your financial details with automated systems. Think before you act, it's like deciding whether to enter a singles bar or not.
03. Phony Job Scam"Any employment offered online without a formal interview, no matter where it originates, should be treated with skepticism," said Arkansas Attorney General Mike Beebe, who investigated one of these scams in 2006. Thank you, you've just ruined the entire virtual telecommuting concept. I'm aware of another type of scam where fake job postings seek to harvest as much personal information from applications as possible.
Other practices are also used.
04. Negative Option ScamsLook for the ASTERISKS, it should be somewhere around the FREE proposal.
05. Nigerian 419 ScamsPeople falling into this one, are the type of people suffering from the "
rich-uncle complex". You don't know his exact wealth, but you secretly hope that on a sunny day a handsome, and of course charging by the minute laywer will bring the news you've been subconsciously expecting your entire life. Think for real and forget about the Internet. Would a complete stranger offer you millions of dollars because he has no one else to give the money to, or cannot open up a bank account for themselves?
06. Pump & Dump ScamRainer Böhme and Thorsten Holz evaluated
the situation.
07. Bogus Fuel Saving DevicesMake an analogy with washing powder/tablets/liquid who's actively advertised as an "energy saver" due to its sophisticated technology that doesn't require hot water, when it happens to be a commodity and if you're going to be saving energy from it, then you've either watched a movie about the Third World, or are very desperate.
08. Grandparents ScamAn elderly person is targeted by the scammer who calls and says something like, "It's me, grandpa." The elderly person will respond, thinking it's one of their grandchildren. Unbelieavable, and perhaps another reason to keep in touch with your grand-parents more often, so they could at least recognize your voice.
09. Oprah Ticket ScamIn case you fall victim into this one, you're not just bored to the bottom of your brain, but a potential guest at Oprah's show with the unique ability to explain how this scam ruined your life, but later on helped your meet the person of your life, where else if not in an online scam discussion group. I feel you.
10. craigslist ScamIt's like the Yellow Pages, some postings are so automatically generated that they happen to be a waste of time, but hopefully not money, so be aware.
 Well, well, well. What do we got here? Couple of interesting domains hosting phishing sites of multiple banks for you to take a look at, or at the cached versions to be precise. What's worth mentioning is the rise of phishing sites using the much more easily and anonymously registered .biz ; .info ; .name domains. However, the first part of these is related to 211.137.13.131 :
Well, well, well. What do we got here? Couple of interesting domains hosting phishing sites of multiple banks for you to take a look at, or at the cached versions to be precise. What's worth mentioning is the rise of phishing sites using the much more easily and anonymously registered .biz ; .info ; .name domains. However, the first part of these is related to 211.137.13.131 :























 Mother Nature
Mother Nature
 Outstanding project
Outstanding project
 Interactive slideshow
Interactive slideshow


 Informative
Informative
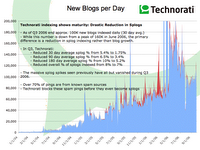
 Last week, the Internet Haganah
Last week, the Internet Haganah 


0 Comments: