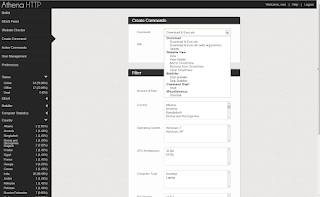
Among the key features of the new DIY botnet building tool is the geographical distribution of the affected hosts on a global map where the ultimate goal for the malware coders behind the release of this malicious software would be to make it easier for their clients to keep track of newly infected hosts.
Related MD5s known to have been involved in the campaign include:
MD5: cdb54a3654ff2fdda7e90c48cbacda02
I'll continue monitoring the development of this DIY botnet builder and will post updates as soon as new developments take place.































0 Comments: