 Following my previous post on "Personal Data Security Breaches - 2000/2005", you may also find this "Chart of Security Breaches for 2005 - 2006" worth taking a look at -- lost or stolen equipment with data dominate the threatscape.
Following my previous post on "Personal Data Security Breaches - 2000/2005", you may also find this "Chart of Security Breaches for 2005 - 2006" worth taking a look at -- lost or stolen equipment with data dominate the threatscape. Following my previous post on "Personal Data Security Breaches - 2000/2005", you may also find this "Chart of Security Breaches for 2005 - 2006" worth taking a look at -- lost or stolen equipment with data dominate the threatscape.
Following my previous post on "Personal Data Security Breaches - 2000/2005", you may also find this "Chart of Security Breaches for 2005 - 2006" worth taking a look at -- lost or stolen equipment with data dominate the threatscape. Great opinionated introduction to the topic. Trusted computing isn't the panacea of total security simply because there can never be 100% secure OS or a device, unless of course you put so much security layers in place to end up with zero usability, so what's it gonna be? Insecurities are a commodity, but security and usability issues are always a matter of viewpoint, so don't act as if you can provide 100% security, because what you're actually offering is a marginal thinking while proposing a solution.
Great opinionated introduction to the topic. Trusted computing isn't the panacea of total security simply because there can never be 100% secure OS or a device, unless of course you put so much security layers in place to end up with zero usability, so what's it gonna be? Insecurities are a commodity, but security and usability issues are always a matter of viewpoint, so don't act as if you can provide 100% security, because what you're actually offering is a marginal thinking while proposing a solution.
 An impressive mastermind is what I got as a type of personality, quite a bit of suspicious flattery isn't it?
An impressive mastermind is what I got as a type of personality, quite a bit of suspicious flattery isn't it?I feel the quiz is more of an ice-breaker, and it's hell of an amusing one as a matter of fact. Hint to the CIA's HR department - promise to show the ones who make it up for a final interview a randomly chosen analyst's collection of secret UFO files, and see your conversion rates skyrocketing. Then explain them the basics of access programs based on classification and why they have to perform better. Arbeit macht access to secret UFO files as a factor for productivity, cute.
More comments from another wannabe secret AGent.
 Mother Nature on the basics of asymmetric warfare :
Mother Nature on the basics of asymmetric warfare :And no, don't even think on speculating of terrorists training divisions of crows to attack, or early warn of UAVs flying around the birds' air space, unless of course your wild imagination prevails.
 With all the buzz of fingerprinting this and that, fingerprint these instructions on how copy and fake fingerprints :
With all the buzz of fingerprinting this and that, fingerprint these instructions on how copy and fake fingerprints :"In order to fake a fingerprint, one needs an original first. Latent fingerprints are nothing but fat and sweat on touched items. Thus to retrieve someone elses fingerprint (in this case the fingerprint you want to forge) one should rely on well tested forensic research methods. Which is what's to be explained here."
Bow to the CCC's full disclosure shedding more light on a common sense insecurity. While it can be tackled by both ensuring the quality of the fingerprinting process, and by technological means such as adding extra layers or cross-referencing through different databases, multiple-factor authentication's benefits are proportional with their immaturity and usability issues. Fancy? For sure. Cutting-edge security? Absolutely from a technological point of view. But when fingerprints start getting more empowerment and integration within our daily lifes, malicious parties would have already taken notice, and again be a step ahead of the technological bias on fingerprinting. Coming up with new identities may indeed end up as a commodity neatly stored in a central database, or perhaps ones collected from elsewhere.
 Outstanding project demonstrating the benefits of open source intelligence positioned on Google Maps while providing you with the very latest global security and suspicious events in categories such as :
Outstanding project demonstrating the benefits of open source intelligence positioned on Google Maps while providing you with the very latest global security and suspicious events in categories such as :- Airport/Aviation Incidents
No more "slicing the threat on pieces", now you can see the big picture for yourself.
 Here's an article arguing that "publishing a privacy statement may be more harmful than not publishing one"only if enforcement, implementation and monitoring don't intersect as they should :
Here's an article arguing that "publishing a privacy statement may be more harmful than not publishing one"only if enforcement, implementation and monitoring don't intersect as they should :"This case demonstrates a complication relating to companies' claiming that they have security measures to protect their end users' privacy. Large, established companies, like Eli Lilly, understand this issue but may still have problems ensuring compliance to their privacy policy. But many emerging companies immediately post their claimed privacy policies on their company websites. These companies often fail to assess the potential risks, burdens and liabilities associated with publishing a privacy policy. They do not realize that publishing a privacy statement may be more harmful than not publishing one."
Privacy exposure assessments still remain rather unpopular among leading companies, and compliance with industry specific requirements for processing and storing personal information continue indirectly replacing what a Chief Privacy Officer would have done in a much more adaptive manner. Can we that easily talk about Total Privacy Management (TPM), the way talk about Total Quality Management (TQM) as an internal key objective for strengthening a company's reputation as a socially-oriented one? It would definitely turn into a criteria for the stakeholders, and a differentiating point for any company in question in the long term. The future of privacy? Don't over-empower the watchers or you'll have the entire data aggregation model of our society used against your rights for the sake of protecting you from "the enemy or the threat of the day".
You may also find some comments from a previous post on "Examining Internet Privacy Policies" relevant to the topic :
"Accountability, public commitment, or copywriters charging per word, privacy policies are often taken for fully enforced ones, whereas the truth is that actually no one is reading, bothering to assess them. And why would you, as by the time you've finished you'll again have no other choice but to accept them in order to use the service in question -- too much personal and sensitive identifying information is what I hear ticking. That's of course the privacy conscious perspective, and to me security is a matter of viewpoint, the way you perceive it going beyond the basics, the very same way you're going to implement it -- Identity 2.0 as a single sign on Web is slowly emerging as the real beast."
 Interactive slideshow providing ten tips on how to tell if someone's lying to you. These can of course be interpreted in different ways and applied under specific circumstances only. Some are very practical though :
Interactive slideshow providing ten tips on how to tell if someone's lying to you. These can of course be interpreted in different ways and applied under specific circumstances only. Some are very practical though :01. Watch Body Language
02. Seek Detail
03. Beware Unpleasantness
04. Observe Eye Contact
05. Signs of Stress
06. Listen for the Pause
07. Ask Again
08. Beware Those Who Protest Too Much
09. Know Thyself
10. Work on Your Intuition
Two more I can add -- answering without being asked, and on purposely stating the possibility as a negative statement already. Here's the article itself, as well as several more handy tips on detecting lies. Don't forget - if someone's being too nice with you, it means they're beating you already.
Ear whisper courtesy of Cartoonstock.com
 Innovative, but a full scale violation of privacy -- what privacy with walking CCTVs nowadays?!
Innovative, but a full scale violation of privacy -- what privacy with walking CCTVs nowadays?!"The world draws ever-closer to the dystopia imagined in Hollywood blockbusters -- police in London are to be equipped with head-mounted cameras which will record everything in the direction the officer is looking. The tiny cameras are about the size of an AA battery and can record images of an extremely high quality.
Claimed to be a deterrent for anti-social behaviour, the first run of head-cams are being tested by eight Metropolitan beat officers this month. If successful, all police officers will eventually be equipped with a head camera.
These new 'robocops' add to the growing number of surveillance machines that peer at the public. Cynics argue that the logical progression of the police head-cam will be head-cameras that all citizens are required to wear. The video data would be relayed back to a central database where transgressions are recorded by a computer."
George Orwell is definitely turning upside down in his grave in the time of writing, and it's entirely up to you to come up with the possible scenarios for abusing this innovation -- The Final Cut too, has a good perspective.
Think that's not enough to raise your eyebrows? British Telecom is also about to "put thousands of spy camera recorders in its phone boxes and beam suspects mugshots to police. Cameras stationed on top of lampposts near the kiosks will send images to hidden digital video recorders inside the booths. Suspects photos will then be messaged almost instantly to hand-held digital assistants used by police and emergency services."
Issues to keep in mind:
- No more tax payers' money wasted on CCTVs to only cover the blind spots introduced by the old ones, now you have the "walking CCTVs" taking care
- Face and voice recognition, as well as parabolic type of remote listening capabilities will be the next milestones to reach
- Data collected would prove invaluable to ongoing investigations, and you know, "computers never lie" so digitally introducing minor motives here and there becomes a handy weakness
- More entertaining reality shows will follow for the purpose of communicating the value of the cameras to the general public
- Someone will sooner or later find a way to jam the stream
 There's a saying about not looking anyone straight into the eyes on the mean streets of New York, guess the same applies to not looking straight into the eyes of London's police anymore. Every country needs an EFF of its own, especially the U.K these days. To illustrate what I have in mind, EPIC's listing the U.K at the top of the leading EU surveillance societies, and you may also find the U.K's opinion on its state of total surveillance, informative as well.
There's a saying about not looking anyone straight into the eyes on the mean streets of New York, guess the same applies to not looking straight into the eyes of London's police anymore. Every country needs an EFF of its own, especially the U.K these days. To illustrate what I have in mind, EPIC's listing the U.K at the top of the leading EU surveillance societies, and you may also find the U.K's opinion on its state of total surveillance, informative as well.Finger-mounted keyboard chick courtesy of Kittytech.
 Just noticed that the reading materials for the course are also listing my "Steganography and Cyber Terrorism Communications" post. Looks nice!
Just noticed that the reading materials for the course are also listing my "Steganography and Cyber Terrorism Communications" post. Looks nice!
 Informative to know :
Informative to know :"Eventually, Andersen said, the big but light telescopes could solve a spy-satellite conundrum. Now, those camera equipped satellites must fly closer to Earth to generate usable pictures. That means their orbits exceed the speed of Earth’s rotation, so the satellites cannot spend much time photographing one location. If spy satellites had huge telescopes, they could be placed higher above the planet in an orbit that moves at the same speed as Earth’s rotation, so they could photograph the same region constantly."
There's just one tiny comment that makes a bad impression - “That way, you could keep a constant eye on someone like Osama bin Laden” he said." In exactly the say way a security consultant wrongly tries to talk top management into increasing a budget by using the buzzword cyberterrorism, it wouldn't work and it's a rather desperate move. Even though, in case you're interested in keeping track of Bin Laden's desert trips, make sure you add a detection pattern for a white horse riding through Afghanistan.
Go through some of my previous posts to catch up with my comments on related topics. Apparently, the no-fly-list has been recently used as an access control measure at the Deutsche Bank's NYC's office according to the DealBreaker :
Apparently, the no-fly-list has been recently used as an access control measure at the Deutsche Bank's NYC's office according to the DealBreaker :"We hear Deutsche Bank’s super-suped-up security extends beyond just the beefy armed guards patrolling the street outside its headquarters at 60 Wall. Yesterday apparently a consultant who was scheduled to attend a meeting at the bank was denied entry because his name appears on the federal “no fly” list. “It was the most intense security I've seen, except for maybe the Israeli consulate,” a source who was present when the consultant was denied entry tells DealBreaker."
While that's a very unpragmatic paranoia, a U.S congresswoman seems to have recently experienced the "no-fly-list trip" too :
"Sanchez said her staff had booked her a one-way ticket from Boise, Idaho to Cincinnati through Denver. Her staff, however, was prevented from printing her boarding pass online and were also blocked from printing her boarding pass at an airport kiosk. Sanchez said she was instructed to check in with a United employee, who told her she was on the terrorist watch list. The employee asked her for identification, Sanchez recalled. "I handed over my congressional ID and he started laughing and said, 'I'm going to need an ID that has your birthday on it,'" Sanchez said in a phone interview with The Associated Press. The employee used Sanchez's birth date to determine that she was not the same Loretta Sanchez listed in the database and she was able to board her flight, she said."
Bureaucrats don't just slow down innovation and take credit for it, but when they also fall down from a window it takes a week for them to hit the ground.
 Last week, the Internet Haganah reported on rumors around jihadist forums, namely, that the CIA has been attacking jihadi web sites.
Last week, the Internet Haganah reported on rumors around jihadist forums, namely, that the CIA has been attacking jihadi web sites.Now while this is totally untrue -- the CIA would rather be monitoring instead of shuting them down, or shut them down only after they've gathered enough info -- it's a good example of twisting the facts to improve the productivity and self-esteem of the jihadists supposed to strike back.
 Confused Bill Gates, but a regularly attacked one too. A rather predictable comment given he's not the only one selling the chewing gums and the soaps this time, so keep on bubbling folks. Think mature Web 2.0, think Semantic web, or at least dare to envision -- Microsoft wishes the Internet was never invented, unless of course they could sell you the license to use it.
Confused Bill Gates, but a regularly attacked one too. A rather predictable comment given he's not the only one selling the chewing gums and the soaps this time, so keep on bubbling folks. Think mature Web 2.0, think Semantic web, or at least dare to envision -- Microsoft wishes the Internet was never invented, unless of course they could sell you the license to use it."There are a hundred YouTube sites out there," Gates said during an interview with a group of journalists in Brussels before a speech to European lawmakers. "You never know. It's very complicated in terms of what are the business models for these sites." Some of them, including sites that offer Web-based word processing and search engines, are being promoted by their creators and analysts as possible competitors to makers of retail packaged software like Microsoft. "We're back kind of in Internet-bubble era in terms of people thinking: 'O.K., traffic. We want traffic. We want traffic,'" Gates said. "There are still some areas where it is unclear what's going to come out of that."
The very basics of Internet marketing which transform branding into communication, segments into communities for instance doesn't necessarily mean that traffic is the cornerstone of E-business. Eyeballs, thus participants marely visitors converted into revenue sources speak for themselves. Win-win-win business models need no comment. Once you get the traffic, boy, what wonders are there for you to discover, sense and profitably respond to. But then again, keep in mind that search and online video represent a tiny portion of the overal Internet user's activities. Don't look for the next Google, or the next YouTube, look beyond.
Having R&D centers on enemy territories creates more job opportunities, and improves Microsoft's comfortability with its stakeholders :
"Microsoft said that it would invest $7.8 billion globally in research and development this year, about 15 percent of sales, and it plans to spend $500 million in Europe next year. Microsoft operates its main European research center on the campus of Cambridge University in England, with other research offices in Denmark and Ireland."
While it's also cheaper to operate them in Europe than in the U.S, money cannot buy innovation and many other things, so don't get too excited but learn how to surf tidal waves, the ones Bill Gates himself predicted back in 1995.
Related posts:
5 things Microsoft can do to secure the Internet, and why it wouldn't?
Microsoft in the Information Security Market
Microsoft's OneCare Penetration Pricing Strategy
 In case you're unaware of Nuclear Grabber's existence -- Babelfish it --WebSense commented on it in their latest "Security Trends - first half of 2006 report" :
In case you're unaware of Nuclear Grabber's existence -- Babelfish it --WebSense commented on it in their latest "Security Trends - first half of 2006 report" : Full scale automation in action, quite some infected folks geolocated already. Going to wash my hands now..
Full scale automation in action, quite some infected folks geolocated already. Going to wash my hands now.. This is worth mentioning, as while you try not to talk about these locations for as long as someone doesn't start blowing the whistle too loud, all you really need is someone to pass by and feel the hyper-sensitive harassment due to Trimingham's ELINT capabilities -- and news articles keep coming about this particular case.
This is worth mentioning, as while you try not to talk about these locations for as long as someone doesn't start blowing the whistle too loud, all you really need is someone to pass by and feel the hyper-sensitive harassment due to Trimingham's ELINT capabilities -- and news articles keep coming about this particular case."The Ministry of Defence has admitted that a fault at a radar dome was responsible for causing electrical problems with dozens of cars. Engines and lights cut out and speedometer dials swung up to 150mph as motorists drove past the dome. At the time the MoD said there was no guarantee that the Trimingham radar on the north Norfolk coast was the cause."
Read some of the memories of a serviceman that was stationed there during the 60s :
"Another story that might be of interest relates to the time that a Russian trawler went aground at Skaw. The indications were that it was an Elint (Electronic intelligence gathering) vessel as the crew hid what they were doing from an RAF Shackleton which flew overhead as part of the search and rescue mission. Whether there was any spying equipment on board is debatable. In any event, the Unst folk did well in "liberating" fishing nets and sundry bits and pieces including the steering wheel, which was subsequently returned to the Russians. However, two RAF lads a steward and a cook found signals, maps and other papers in the skipper's cabin, some of this hidden under his mattress. They brought these back to me and our station intelligence officer had a look at them. By chance he was a Russian linguist and was able to provide a summary of what was in the documents before they were forwarded to the RAF intelligence staff at the Ministry of Defence. One of the documents proved extremely valuable to the Navy but what amazed them was that the translated summary had been done by an RAF flying officer on Unst."
You may also be interested in going through a table that "includes all military sites which have significant intelligence-gathering or analysis capability with official US presence; these are the sites which have figures for numbers of US and UK personnel".
Trimingham's radar dome courtesy of munkt0n, and Flickr's Radars group.
Related posts:
Why's that radar screen not blinking over there?
Achieving Information Warfare Dominance Back in 1962
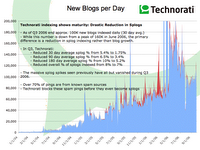 Just read Technorati's latest "State of the Blogosphere, October, 2006" presented with in-depth visual stats on the 57 million blogs they're currently tracking, and yes, all the splogs they're fighting to filter. Worth taking your time to go through the post, and you may also be interested in finding how come my ROI out of blogging is so positive these days.
Just read Technorati's latest "State of the Blogosphere, October, 2006" presented with in-depth visual stats on the 57 million blogs they're currently tracking, and yes, all the splogs they're fighting to filter. Worth taking your time to go through the post, and you may also be interested in finding how come my ROI out of blogging is so positive these days."As we’ve said in the past, some of the new blogs in our index are Spam blogs or 'splogs'. The good news is Technorati has gotten much better at preventing these kinds of blogs from getting into our indexes in the first place, which may be a factor in the slight slowing in the average of new blogs created each day.
The spikes in red on the chart above shows the increased activity that occurs when spammers create massive numbers of fake blogs and try to get them into our indexes. As the chart shows, we’ve done a much better job over the last quarter at nearly eliminating those red spikes. While last quarter I reported about 8% of new blogs that get past our filters and make it into the index are splogs, I’m happy to report that that number is now more like 4%. As always, we’ll continue to be hyper-focused on making sure that new attacks are spotted and eliminated as quickly as possible.
My gut feeling is that since we're better at dealing with Spam now, even some of the blue areas in last quarter's graph were probably accountable to spam, which would mean that rather than the bumpy ride shown above, we're actually seeing a steady increased (but slower) growth of the blogosphere. Hopefully we'll be able to have a more detailed analysis of these issues next quarter."
Meanwhile, the splogfigher is doing an amazing job of analyzing and coming up with exact splog URLs -- I'm reposting so that third-parties of particular interest reading here take a notice -- and week ago came up with 150,000 splogs, notice the dominating blogging platform? Blogspot all the way!
"I see that Google has been deleting quite a large number of splogs but even then they are on average about 20% effective. What that means is if a single spammer creates 1000 splogs, Google will eventually delete at most about 200 of them leaving 800 alone. Obvously this is rather poor percentage and hopefully my efforts will bump up that figure close to 90% and above.
20061030_1.txt - 19401 splogs20061030_2.txt - 4332 splogs
20061030_3.txt - 8936 splogs
20061030_4.txt - 8794 splogs
20061030_5.txt - 18912 splogs
20061030_6.txt - 5158 splogs
20061030_7.txt - 70755 splogs
20061030_8.txt - 1182 splogs
20061030_9.txt - 11410 splogs
20061030_10.txt - 968 splogs
20061030_11.txt - 1584 splogs
Here is a tarball of all splog list files listed above: 20061030.tar.gz"
Obviously, spammers are exploiting Blogspot's signup process, and I really feel it's about time Google starts tolerating more errors with users having trouble reading a sophisticated CAPTCHA, compared to its current too user-friendly and easily defeated one. They can balance for sure. Something else to consider, take for example the splogs collected for May, and whole the splogfighter is pointing out on the engineered 404s and Google's efforts in removing them, I was able to verify content response from over 200 splogs reported back then, take cigar-accessories-2008.blogspot.com for instance -- anyone up for crawling the lists and clustering the results? Once the signup process is flawed, not even the wisdom of crowds flagging splogs can help you.
Another recommended and very recent analysis "Characterizing the Splogosphere" is also full of juicy details, and statistical info on the emerging problem. Spammers are anything but old-fashioned.
 Wish I could blog everything I read and makes me an impression but that's not the point. The point is to emphasize on the big picture, and find the balance between information overload and information underload.
Wish I could blog everything I read and makes me an impression but that's not the point. The point is to emphasize on the big picture, and find the balance between information overload and information underload.01. North Korea, Turkmenistan, Eritrea the worst violators of press freedom - Journalists in North Korea, Eritrea, Turkmenistan, Cuba, Burma and China are still risking their life or imprisonment for trying to keep us informed. to FreeSpeech Censorship
02. When North Korea Falls - The furor over Kim Jong Il’s missile tests and nuclear brinksmanship obscures the real threat: the prospect of North Korea’s catastrophic collapse. How the regime ends could determine the balance of power in Asia for decades. The likely winner? China to Geopolitics
03. U.S. revives terror data mining - In response to concerns about the program's privacy and civil liberties implications, Congress in 2003 cut all funding for it, but research continued in different agencies, funded by classified appropriations for Pentagon intelligence agencies. to Intelligence Terrorism
04. Singapore Slings Censorship - StarHub Cable Vision of Singapore is being fined $6,350 for showing footage of lesbian sex and bondage during episodes of the reality program "Cheaters." to Censorship Singapore
05. Googlers Worldwide - Number of Google employees 2004-2006. to Google
06. Can IPS Alleviate The Botnet Problem? - Next-Generation IPS devices bring a number of extra benefits, and solve many of the botnet problems. When deployed at the network edge, IPS devices can see all traffic entering and exciting the network. to Security Malware Botnet IPS
07. Abu Ghraib Photos, Videos To Come - The ACLU has sought the release of 87 photos and four videotapes taken at the prison as part of an October 2003 lawsuit demanding information on the treatment of detainees in U.S. custody and the transfer of prisoners to countries known to use torture. to Military PSYOPS
08. 'Censorship' controversy? Sometimes it's just part of the ad campaign - NBC and the CW network had refused to run ads in which the singer Natalie Maines refers to President George W. Bush with an expletive and as "dumb." to Censorship Advertising
09. Rutkowska: Anti-Virus Software Is Ineffective - Stealth malware researcher Joanna Rutkowska discusses her interest in computer security, the threat from rootkits and why the world is not ready for virtual machine technology. to Malware Interview
10. Under Fire, Soldiers Kill Blogs - Some of the web's more popular "milblogs" -- blogs maintained by present or former active duty military personnel -- are going quiet following a renewed push by U.S. military officials to scan sites for security risks. to Blog Military OPSEC
11. Is Google Evil? - Internet privacy? Google already knows more about you than the National Security Agency ever will. to Google Privacy
12. Google Earth Update of Eyeballs 1 - ECHELON's Global Stations - Sebana Seca Echelon Station, Pine Gap Echelon Station, Geraldton Echelon Station, Misawa Echelon Station, Kunia Echelon Station, Waihopai Echelon Station. to OSINT ECHELON Intelligence SIGINT
13. U.N. blasts Cisco, others on China cooperation - "It's the same equipment that we sell in every country around the world in which we sell equipment," said Art Reilly, Cisco's senior director for strategic technology policy. "There is no differentiation." to Censorship China Microsoft Google Yahoo Cisco
14. GAO: Better coordination of cybersecurity R&D needed - DOD officials told GAO that the department provided about $150 million to its cybersecurity research programs in fiscal 2005. to Security
15. The Reinvention Of Martha Stewart - Stewart no longer has total control over the brand she built. She still owns the bulk of the company's stock and holds 92% of the voting power--prompting speculation that she may one day take it private--but she can't dictate the agenda. to Branding
16. Raytheon Announces Revolutionary New 'Cockpit' For Unmanned Aircraft - "We took the best-of-breed technologies from the gaming industry and coupled them with 35-years Raytheon UAS command and control expertise and developed a state-of-the-art universal cockpit built around the operator". to Military UAV
17. The Tangram Intelligence Program - The Tangram program makes no distinction between intentional and deliberate acts to avoid detection versus the consequences of spotty collection and reporting of intelligence. to Intelligence TIA Tangram
18. Intellipedia - a Classified Wiki - Intellipedia is a classified wiki that runs on JWICS, the top-secret network Intelink that links the 16 agencies that comprise the U.S. intelligence community. It is not accessible to the public. to Intelligence Wikipedia
19. China: We don't censor the Internet. Really - We have hundreds of journalists in China, and some of them have legal problems. It has nothing to do with freedom of expression. to Censorship China FreeSpeech
20. Ratings Table of EU and Leading Surveillance Societies - This year Privacy International took the decision to use the report as the basis for a ranking assessment of the state of privacy in all EU countries together with eleven benchmark countries. to Privacy Surveillance 1984
21. Watch a live spam bot in action - Take a peek with me into one trojan’s junkmail activities. The following account is happening as I type, and shows that some image spam is not unique even though it appears to be random. to Malware Bots Spam
22. OS X proof of concept virus -Macarena - OSX.Macarena is a proof of concept virus that infects files in the current folder on the compromised computer. to Malware MAC
23. American Leadership and War - Which presidents and political parties were responsible for America's deadliest wars? Republicans, Democrats, or the Founding Fathers? This map answers our question by illustrating the history of American conflict from the Revolutionary War to Iraq. to Military War Leadership
24. Diebold slams HBO Hacking Democracy documentary - According to Diebold, 40 per cent of votes this November will be recorded electronically with its own machines accounting for 40 per cent of that market. to Security Diebold Voting
 Professor Falken would have loved this one. The Federation of American Scientists recently released their report from the Summit on Educational Games, and an upcoming educational game :
Professor Falken would have loved this one. The Federation of American Scientists recently released their report from the Summit on Educational Games, and an upcoming educational game : Know your enemy to better predict his moves and future strategies as Symbian malware optimization is getting the necessary attention from the academic community :
Know your enemy to better predict his moves and future strategies as Symbian malware optimization is getting the necessary attention from the academic community :"The University of Santa Barbara's software group released the source code for their proof of concept 'Feakk' worm that was developed by Paul Haas in March 2005. The worm uses SMS to send a hyperlink to its target. The targeted user then has to visit the hyperlink and download and acknowledge three sets of prompts in order for the worm to install, at which point it will immediately start to run in the background. It will scan the user's contact list and send a message to each contact (including the recipients' names) and will also scan for new contacts at certain intervals.
Upon installation, the worm checks for a contact with the first name "HACKME." If this isn't found the worm will exit. If it is found, then the worm sends itself to every mobile number it finds in the user's contact list. The author did not write a payload because this was for demonstration purposes only and it should be noted that it can be removed via the "Uninstall List."
While malware authors will turn the concept into a commodity, it doesn't exploit a speficic OS vulnerability, thus the possibility of large scale outbreaks doesn't really exist at all. In a previous post I commented on some future developments related to the penetration of mobile devices in our daily lifes and the trust factor assuming whoever holds the handset is actually the one using it :
"Malware authors indeed have financial incentives to futher continue recompling publicly available PoC mobile malware source code, and it's the purchasing/identification features phones, opening a car with an SMS, opening a door with an SMS, purchasing over an SMS or direct barcode scanning, mobile impersonation scams, harvesting phone numbers of infected victims, as well as unknowingly interacting with premium numbers are the things about to get directly abused -- efficiently and automatically."
Digitally fingerprinting mobile malware may be marketable, but it's rather useless as we've seen in the past compared to basic user awareness.
I feel the University of Santa Barbara's software group are very much on the right track, conducting research on OS and application specific vulnerabilities, as they've released quite some interesting papers during 2006 :
Advanced Attacks Against PocketPC Phones
PocketPC MMS - Remote Code Injection/Execution Vulnerability and Denial-of-Service
Vulnerability Analysis of MMS User Agents
Security of Smart Phones
Using Labeling to Prevent Cross-Service Attacks Against Smart Phones

0 Comments: