The Avalanche Botnet and the TROYAK-AS Connection
According to the latest APWG Global Phishing Survey:
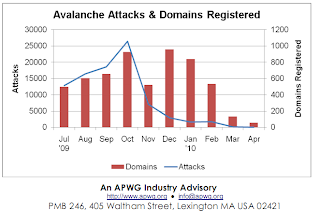
- But by mid-2009, phishing was dominated by one player as never before the Avalanche phishing operation. This criminal entity is one of the most sophisticated and damaging on the Internet, and perfected a mass-production system for deploying phishing sites and "crimeware" - malware designed specifically to automate identity theft and facilitate unauthorized transactions from consumer bank accounts. Avalanche was responsible for two-thirds (66%) of all phishing attacks launched in the second half of 2009, and was responsible for the overall increase in phishing attacks recorded across the Internet."
- "Cutwail aka PushDo is a spamming trojan being used to send out massive amounts of spam with links (or lures) to phishing pages or pages that ask the users to download and run programs. Those programs invariably turn out to be instances of the Zeus/ZBot/WNSPOEM banking Trojan. There are also unrelated criminals that also use Zeus Trojans to steal online banking information that are not related to this set of scams.
The Avalanche botnet is the middle-step between the spamming botnet and Trojans that steal banking information. It is basically a hosting platform used by the attackers. Because the Avalanche bots act as a simple proxy, and there are thousands of them, it has been exceedingly difficult to shutdown the phish pages. Instead most Anti-Phishing organizations have focused on shutting down the domain names that were used in the phishing URLs."
The Avalanche Botnet's ZeuS crimeware/client-side exploit serving campaigns, in chronological order:
Zeus Crimeware/Client-Side Exploits Serving Campaign in the Wild
Scareware, Sinowal, Client-Side Exploits Serving Spam Campaign in the Wild
IRS/PhotoArchive Themed Zeus/Client-Side Exploits Serving Campaign in the Wild
Tax Report Themed Zeus/Client-Side Exploits Serving Campaign in the Wild
PhotoArchive Crimeware/Client-Side Exploits Serving Campaign in the Wild
Facebook/AOL Update Tool Spam Campaign Serving Crimeware and Client-Side Exploits
Pushdo Serving Crimeware, Client-Side Exploits and Russian Bride Scams
Outlook Web Access Themed Spam Campaign Serves Zeus Crimeware
Pushdo Injecting Bogus Swine Flu Vaccine
"Your mailbox has been deactivated" Spam Campaign Serving Crimeware
Ongoing FDIC Spam Campaign Serves Zeus Crimeware
The Multitasking Fast-Flux Botnet that Wants to Bank With You
Related articles on TROYAK-AS, and various cybercrime trends:
TROYAK-AS: the cybercrime-friendly ISP that just won't go away
AS-Troyak Exposes a Large Cybercrime Infrastructure
The current state of the crimeware threat - Q&A
Report: ZeuS crimeware kit, malicious PDFs drive growth of cybercrime
Report: Malicious PDF files comprised 80 percent of all exploits for 2009
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.