What's the average price for a stolen credit card? How are prices shaped within the cybercrime ecosystem? Can we talk about price discrimination within the underground marketplace? Just how easy is to purchase stolen credit cards known as dumps or full dumps, nowadays?
In this intelligence brief, I will expose the market for stolen credit cards data, by profiling 20 currently active and responding gateways for processing of fraudulently obtained financial data.
Key summary points:
- Tens of thousands of stolen credit cards a.k.a. dumps and full dumps offered for sale in a DIY market fashion
- The majority of the carding sites are hosted in the Ukraine and the Netherlands
- Liberty Reserve is the payment option of choice for the majority of the portals
- Four domains are using Yahoo accounts and one using Live.com account for domain registration
- Four of the domains are using identical name servers
- Each DIY gateway for processing of fraudulently obtained financial data has a built-in credit cards checker or offers links to external sites performing the service
- Several of the fraudulent gateways offered proxies-as-a-service, allowing cybercriminals to hide their real IPs by using the malware infected hosts as stepping stones
What used to be a market where over-the-counter trade was the primary growth factor, is today's highly standardized marketplace with DIY online interfaces, allowing anyone to join and purchase stolen credit card details. Naturally, the vendors of dumps and full dumps are vertically integrating within the marketplace, and are offering additional services such as checkers for credit cards validity, and proxies-as-a-service -- compromised malware infected hosts -- allowing a potential cybercriminal to opportunity to hide their IP while using the recently purchased credit cards data.
How are prices shaped within this new and standardized market model offered commodity goods such as stolen credit cards, and is price discrimination for the stolen credit cards even feasible? The vendors are currently offered fixed prices for the majority of credit cards, with slight increases in the price of a stolen credit card, if the card is Premium. Bulk orders are naturally also considered as a growth factor the DIY interfaces, with slight discounts being offered for bulk orders.
As far as price discrimination is concerned, the concept is long gone, and has become the victim of this ongoing standardization of the market. The same goes for penetration pricing, as the vendors of stolen credit cards details are now enjoying a better underground market transparency into the fraudulent propositions of competing portals, helping them to set the prices more easily, without the need to lower the price in order to enter the market segment.
Let's profile the 20 gateways for processing of fraudulently obtained financial data.
Responding IPs, registered emails, name servers, ASs, associated ICQ numbers, geolocation of the hosting IP is as follows:
ccmall.cc - 213.5.70.34 - Name server: TR1.ONLINESHOP.SU - Email: gwylhcfktm@whoisservices.cn - AS49544, INTERACTIVE3D-AS - HOSTED IN THE NETHERLANDS
track2.name - 91.213.175.121 - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
trackstore.su - 46.21.148.26 - Email: roger.sroy@yahoo.com - AS35017, SWIFTWAY-AS - HOSTED IN THE NETHERLANDS
magic-numbers.cc - 91.213.175.89; 91.223.77.35 Name server: NS1.1000DNS.NET - Email: contact@privacyprotect.org - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
allfresh.us - 46.21.144.115 - Name server: YNS1.YAHOO.COM - Email: keikomiyahara@yahoo.com - AS35017, SWIFTWAY-AS - HOSTED IN THE NETHERLANDS
freshstock.biz - 38.97.225.166; 69.175.73.184 - Name server - NS1.PIPEDNS.COM Email: ghmbfvntxs@whoisprivacyprotect.com - AS32475, SINGLEHOP , Inc. - HOSTED IN THE UNITED STATES
bulba.cc - 91.223.77.254 - Name server: NS1.NAMESELF.COM - Email: bulbacc@yahoo.com - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
approven.su - 91.229.248.20 - Name server: dns1.naunet.ru - Email: yurtan20@e1.ru - HOSTED IN UKRAINE
cv2shop.com - 72.20.12.205 - Name server: DNS1.NAME-SERVICES.COM - Email: wnfxgjdg@whoisprivacyprotect.com - AS25761, STAMINUS-COMM - HOSTED IN THE UNITED STATES
vzone.tc - 49.212.25.242 - Name server: dns1.yandex.ru - Email: adamsnames@rrpproxy.net - AS9371, SAKURA-C SAKURA Internet - HOSTED IN JAPAN
ccStore.ru - 91.220.101.200 - Name server: ns1.1000dns.net - Email: ccstoreru@yahoo.com - AS49704 - HOSTED IN THE NETHERLANDS
dumps.cc redirects to privateservices.ws and trackservices.ws - 124.217.247.59 - Name server: NS1.IPSTATES.NET - Email: dumps.cc@domainsproxy.net - AS45839, PIRADIUS-AS PIRADIUS NET - HOSTED IN MALAYSIA
privateservices.ws - 217.23.9.92 - Name server: ns1.servicedns.nl - AS49981, WorldStream AS Maasdijk - HOSTED IN THE NETHERLANDS
perfect-numbers.cc - 91.220.101.75 - Name server: NS1.1000DNS.NET - AS49704, ADDOS-AS FOP Litvinenko Sergey Nikolaevich; icq: 605099359 - HOSTED IN THE NETHERLANDS
mega4u.biz - 178.162.174.71 - Name server: NS1.FREEDNS.WS - Email: persiks@online.ua - AS28753, LEASEWEB-DE - HOSTED IN GERMANY
accessltd.ru - 91.213.175.167 - Name server: ns14.zoneedit.com - Email - admin@accessltd.ru - AS6849, UKRTELNET JSC UKRTELECOM, 18, Shevchenko blvd. Kiev, Ukraine - HOSTED IN UKRAINE
pwnshop.cc - 77.79.13.209 - Name server: NS1.AFRAID.ORG - AS16125, DC-AS UAB - HOSTED IN LITHUANIA
bestdumps.su - 91.213.175.57 - Name server: ns1.1000dns.net - Email: bestdumpssu@live.com ICQ : 619429330 - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
mycc.su - 188.93.17.180 - Name server: ns1.deltahost.com.ua - Email: admin@mycc.su - AS49505, SELECTEL Ltd. - HOSTED IN RUSSIA
bestdumps.biz - 195.3.145.87 - Name server: NS1.BESTDUMPS.BIZ - Email: admin@bestdumps.biz - AS50244 - HOSTED IN LATVIA, Associated email: bdsupport@jabber.org, Associated ICQ: 655584
dumpshop.bz - 217.23.9.93 - Name server: ns1.servicedns.nl - Email: contact@privacyprotect.org; AS49981, WorldStream; HOSTED IN THE NETHERLANDS
cardshop.bz - 217.23.9.67 - Name server: ns1.servicedns.nl - Email: contact@privacyprotect.org; AS49981, WorldStream; HOSTED IN THE NETHERLANDS
Let's now take an inside view into each and every of the above-profiled gateways.
_accessltd.ru
Accessltd.ru is currently offering an inventory of 39328 U.S based stolen credit card details for just $2.10 each, followed by another inventory of 342 U.K based credit cards for $9 each, and 108 Japanese based credit cards for $8 each, with another dump of 293 Canadian credit cards for $7 each, and 198 Australian based credit cards for $8 each.
According to the service - "We accept Liberty Reserve only.Refund on your wallets is not possible."
Moreover, here's how the service operates based on the Service Rules:
"To check the card is integrated into the platform checker CCChecker, currently the best checker, not only in our opinion. Replacement cards are only based on the result of this checker. Check Card is available immediately after order payment, in the section My Orders. To check, click "Check". Cards checking in for a few seconds. Button "Check" - available within 20 minutes after purchase. Check Card - a paid service, which costs $ 0.3, if the card is not valid - the cost of cards back to your
account automatically.
Replacement card can only be made in the automatic mode. If checker dont working, for replace need screens your checker in the Support section with a description of the problem. These tickets will only be considered if they contain the results of your test, not a "paid for Skype, did not work, replace". We do not care where and how you use the material, loading support extra information is needed.We will check the card manually, and if any parameter is not correct to make you refund. Sorting:
Our shop is available sorted by the following parameters:
1. BIN ( Multiple)
2. State (Multiple)
3. City (Multiple)
4. Zip (Multiple)"
_Domain reconnaissance
accessltd.ru - 91.213.175.167 - Name server: ns14.zoneedit.com - Email - admin@accessltd.ru - AS6849, UKRTELNET JSC UKRTELECOM, 18, Shevchenko blvd. Kiev, Ukraine - HOSTED IN UKRAINE
_AllFresh.us
AllFresh.us is yet another DIY shop for purchasing stolen credit card details, all fresh as the name says.
On 2011/08/04 the service issued updates for "updated US Amex, Discover fresh and good", followed by another update on the next day, this time advertising "updated more cvv Franche new and good today."
The price for a stole card number is static and is $6 per credit card.
_Domain reconnaissance
allfresh.us - 46.21.144.115 - Name server: YNS1.YAHOO.COM - Email: keikomiyahara@yahoo.com - AS35017, SWIFTWAY-AS - HOSTED IN THE NETHERLANDS
_Approven.su
Approven.su is a relatively more advanced DIY shop for purchasing of stolen credit card details, due to to its advanced search options, allowing cybercriminals an easier way for searching into the the dumps/full dumps of stolen credit card details.
The most recent annoucement at Approven.su says "Sumer Jam: 8 new bases - Georgia2, California3, Pennsylvania3, Puerto Rico, California4, Texas4, Virginia, California5".
The price for a stolen credit card is $10, with Platinum cards going for $15.
_Domain reconnaissance
approven.su - 91.229.248.20 - Name server: dns1.naunet.ru - Email: yurtan20@e1.ru - HOSTED IN UKRAINE
_BestDumps.biz
BestDumps.biz doesn't allow newly registered visitors the opportunity to search across its database of stolen credit card details, unless they pay $50 using Liberty Reserve.
_Domain reconnaissance
bestdumps.biz - 195.3.145.87 - Name server: NS1.BESTDUMPS.BIZ - Email: admin@bestdumps.biz - AS50244 - HOSTED IN LATVIA, Associated email: bdsupport@jabber.org, Associated ICQ: 655584
_Bulba.cc
Bulba.cc offers a Checker for stolen credit cards. The most recent announcement is "UPDATE ADDED 1000 MEXICO RARE! FRESH! 95% VALID!!! Hurry up to load the account".
The service advertised itself as follows:
"Hello my name is Bulba. I am official reseller of TRACK2.NAME service. Bulba.cc opened because track2.name closed registration and don't accept new customers. We don't have any specific rules. Our only rule is "we don't replace bad dumps". That means we don't replace them at all and we don't have replacement policy. Don't ask about it in any case!
We accept Libery Reserve, WU, MG, Bank Transfer (NEW) without any fees. Minimum for payment by LR - 10$, WU, MG - 500$, Bank Transfer - 500$. Also we give 10% bonus of money to all purchases.
Our bases: SALES - track2, 50% valid, alot dumps! Very cheap $7 per one! DATABASE9 - TRACK1+TRACK2(90%) + TRACK2(10%) only! 80% valid, FRESH. NEW DATABASE, TRACK 2 only, 95% valid, FRESH! NEW!"
_Domain reconnaissance
bulba.cc - 91.223.77.254 - Name server: NS1.NAMESELF.COM - Email: bulbacc@yahoo.com - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
_CardShop.bz
CardShop.bz is yet another DIY interface for purchasing stolen credit cards data (dumps/full dumps). The general rules of the site are as follows:
2.1.1) All calculations on a site and its services - automatic
2.1.2) Minimum funding amount on a site 10$ that equals to 50 credits
2.1.3) Period of validity of credits is 1 month (under the additional oral agreement term can be increased). In a case if you had not time to spend all credits, it is possible to make fund of your account and credits will automatically be restored
2.1.4) Refund for not used credits - IS NOT POSSIBLE
In order to avoid conflict situations, please check information that you need before funding account
The Rules of service ONLINE sale CC/DUMPS reads:
"2.2) Rules of service ONLINE sale CC/DUMPS
2.2.1) Return of credits for purchased CC/Dumps which have been checked before purchase and have status VALID - IS NOT POSSIBLE
2.2.1) Return of credits for purchased CC/Dumps which have been checked in 1 hour after purchase through the link 'Check' and having status VALID - IS NOT POSSIBLE
2.2.2) Return of credits for purchased invalid CC/Dumps (DECLINE/HOLD CALL/PICKUP) which are not checked before purchase, is possible only within 24 hours after the order. After 24 hours any claims on return of credits are not accepted
2.2.3) You will not be charged for invalid CC/Dumps if you checked it instant or in 1 hour and credits will be refunded automatically. You will be charged only for CC/Dumps checking even if CC/Dumps is invalid
2.2.4) We do not guarantee limits and amounts on CC/Dumps
2.3) Rules of service ONLINE Check CC/Dumps
2.3.1) Status Valid, means that at the moment of check CC/Dump was Approved
2.3.2) Status Declined, means that at the moment of check CC/Dump was Decline/Pickup/Hold Call
2.3.3) Claims on checked DUMP/CC are not accepted.
2.7) Rules of other services on site CardShop will be added in this agreement later
3) Prices and Tariffs
3.1.1) 1 credit is accepted to a unit of account on site CardShop. Initially 1 credit = 1$. The price for 1 credit can change according to tariffs for funding. Tariffs could be found in Tariff section at site
3.1.2) Administration CardShop reserves the right to itself at any moment to change tariffs. You agree periodically check tariffs on site CardShop to learn about possible changes in them"
The is currently offering 33903 U.S based stolen credit cards for sale. The web site is also offering Proxies for sale -- compromised malware infected hosts- where the price is 0.3$ per proxy. Next to the inventory of stolen credit cards and the proxy service, the web site is also offering batch checking for the validity of the stolen credit cards, and is also performing Lookups SSN|MMN services, with the ability to Lookup MMN in California state.
_Domain reconnaissance
cardshop.bz - 217.23.9.67 - Name server: ns1.servicedns.nl - Email: contact@privacyprotect.org; AS49981, WorldStream; HOSTED IN THE NETHERLANDS
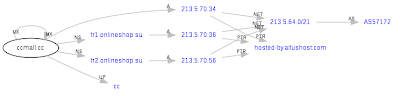
_CcMall.cc
CcMall.cc is associated with the following ICQ number 777605, where potential buyers would have to connect with the seller in order to be offered the ability to register in the site. "For private limited registration only into the new shop" is currently displayed on CcMall.cc's web site.
_Domain reconnaissance
ccmall.cc - 213.5.70.34 - Name server: TR1.ONLINESHOP.SU - Email: gwylhcfktm@whoisservices.cn - AS49544, INTERACTIVE3D-AS - HOSTED IN THE NETHERLANDS; Name server: tr1.onlineshop.su - Emaill: exchangers@msn.com context.cx is also registered using exchangers@msn.com.
_ccStore.ru
ccStore.ru is associated with the following ICQ - 20606, and requires that a valid email address is supplied in order to activate the access to yet another interface for selling and reselling fraudulently obtained financial data.
_Domain reconnaissance
ccStore.ru - 91.220.101.200 - Name server: ns1.1000dns.net - Email: ccstoreru@yahoo.com - AS49704 - HOSTED IN THE NETHERLANDS
_Cv2Shop.com
Cv2Shop.com has an inventory of 734 U.S based stolen credit cards for the price of Discovery - $2.2 per piece; Amex for $2; Mastercard for $2; Visa for $1.7 per piece. The fraudulent interface is also offering 80 Canadian stolen credit cards for the price of $7 per piece for Discovery and Amex, and for $6 for Mastercard and $5 for Visa.
_Domain reconnaissance
cv2shop.com - 72.20.12.205 - Name server: DNS1.NAME-SERVICES.COM - Email: wnfxgjdg@whoisprivacyprotect.com - AS25761, STAMINUS-COMM - HOSTED IN THE UNITED STATES
_FreshStock.biz
FreshStock.biz is associated with the following ICQ - 607373112 where users have to initiate the contact in order to obtain access to the DIY shop for stolen credit cards..
_Domain reconnaissance
freshstock.biz - 38.97.225.166; 69.175.73.184 - Name server - NS1.PIPEDNS.COM Email: ghmbfvntxs@whoisprivacyprotect.com - AS32475, SINGLEHOP , Inc. - HOSTED IN THE UNITED STATES
_Magic-Numbers.cc
Magic-Numbers.cc is associated with the following ICQ - 333277 and Jabber: elche@jabber.org where users wanting bulk orders have to contact the cybercriminals offering the DIY interface for stolen credit card numbers.
The web site is currently offering 24642 U.S based stolen credit cards, followed by another 1545 Israeli based credit cards, with a total dumps currently being offered at 43,507. The most recent advertisements read: "Australia base, ultra virgin fresh base - track2 available. Approval rate 85%"
_Domain reconnaissance
magic-numbers.cc - 91.213.175.89; 91.223.77.35 Name server: NS1.1000DNS.NET - Email: contact@privacyprotect.org - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
_Mega4u.biz
mega4u.biz is currently closed for free registration.
_Domain reconnaissance
mega4u.biz - 178.162.174.71 - Name server: NS1.FREEDNS.WS - Email: persiks@online.ua - AS28753, LEASEWEB-DE - HOSTED IN GERMANY
_MyCc.su
MyCc.su is associated with the following ICQ - 40040000 and next to offering stolen credit cards for sale, is also soliciting for security vulnerabilities - "Found a bug? We will pay!". The latest update from September 29 says that 1500 EU based stolen credit cards have been added, followed by another update from the same date, this time with 300 French based stolen credit cards added.
The price of the stolen credit cards varies between $2 and $5
_Domain reconnaissance
mycc.su - 188.93.17.180 - Name server: ns1.deltahost.com.ua - Email: admin@mycc.su - AS49505, SELECTEL Ltd. - HOSTED IN RUSSIA
_Perfect-Numbers.cc
Perfect-Numbers.cc is yet another DIY interface for purchasing stolen credit cards. It's associated with teh following ICQ - 605099359. Users are able to search within the interface only after they have refilled their balance using Liberty Reserve as a means for payment.
_Domain reconnaissance
perfect-numbers.cc - 91.220.101.75 - Name server: NS1.1000DNS.NET - AS49704, ADDOS-AS FOP Litvinenko Sergey Nikolaevich; icq: 605099359 - HOSTED IN THE NETHERLANDS
_PrivateServices.ws
privateservices.ws currently has a database of 634 U.K based stolen credit cards, and another 293 French based stolen credit cards.
_Domain reconnaissance
privateservices.ws - 217.23.9.92 - Name server: ns1.servicedns.nl - AS49981, WorldStream AS Maasdijk - HOSTED IN THE NETHERLANDS
_pwnshop.cc
pwnshop.cc is yet another DIY interface for selling stolen credit card numbers. The web site is currently returning the following message: "You can obtain registration code only from exist clients.Please be aware of scam - registration code is free for exist clients, so if you pay for it - as for refund."
_Domain reconnaissance
pwnshop.cc - 77.79.13.209 - Name server: NS1.AFRAID.ORG - AS16125, DC-AS UAB - HOSTED IN LITHUANIA
_TrackStore.su
trackstore.su is offering existing clients to option to refer additional customers for the price of $20 each. The web site is currently offering 1648 U.S based stolen credit cards, exclusively from the Suntrust Bank for the price of $10 for each stolen credit card.
_Domain reconnaissance
trackstore.su - 46.21.148.26 - Email: roger.sroy@yahoo.com - AS35017, SWIFTWAY-AS - HOSTED IN THE NETHERLANDS
_Track2.name
track2.name is offering stolen credit card numbers for the price of $20 for each stolen credit card.
_Domain reconnaissance
track2.name - 91.213.175.121 - AS6849, UKRTELNET JSC UKRTELECOM - HOSTED IN UKRAINE
_vzone.tc
vzone.tc is yet another DIY shop for stolen credid card numbers. The current announcement reads : "Dear users, after you buy cards, to view proper information, please click download all cards or download selected card from My Cards page. It will show you all information like Last Name and all the additional info like phone, email.
P.S If you dislike new shop V.2 of our shop, then please use support link and send us your feedback to admin, if you want to back old shop V.1 then send feedback with proper reasons why u again want to see old shop V.1"
The current price for a stolen credit card is $1.80 for every card. Next to offering stolen credit cards as a service, the shop is also offering SSN and DOB Searcher, next to the opportunity for customers of the shop to also purchase proxies -- compromised malware infected hosts.
_Domain reconnaissance
vzone.tc - 49.212.25.242 - Name server: dns1.yandex.ru - Email: adamsnames@rrpproxy.net - AS9371, SAKURA-C SAKURA Internet - HOSTED IN JAPAN
_DumpsSheck.com
dumpscheck.com is associated wit the following ICQ - 612303315 is an advanced checker for the validity of stolen credit card details. The web site says "Current merchant accepts VISA, MASTERCARD, AMEX, DISCOVER, DINERS, JCB."
_Domain reconnaissance
dumpscheck.com - 206.217.196.47 - Name server: NS1.DUMPSCHECK.COM - Icq 612303315; AS4436, NLAYER Communications, Inc. - HOSTED IN THE UNITED STATES
Related posts on the economics of cybercrime:
New report details the prices within the cybercrime market
CardCops: Stolen credit card details getting cheaper
Microsoft study debunks profitability of the underground economy
Are Stolen Credit Card Details Getting Cheaper?
Squeezing the Cybercrime Ecosystem in 2009
Price Discrimination in the Market for Stolen Credit Cards
The Underground Economy's Supply of Goods
Microsoft study debunks phishing profitability
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter. Continue reading →











































































RSS Feed