If you could only eradicate the radicalization of immature islamic youth over the Internet with the push of a button. Great surgical shot!
Continue reading →
Continue reading →
Email: dancho.danchev@hush.com Bitcoin Donate: bc1qncspyks7uwdkyyxzxzp6zjgqlrwm3er3q88dju
 Every breath you take, every move you make, I'll be watching you. Used to be a great song, but has a disturbing context these days. Nino Leitner's EveryStepYouTake documentary on the state of surveillance in the U.K will premier this month, and I suspect the full version will be made available for the world to see too :
Every breath you take, every move you make, I'll be watching you. Used to be a great song, but has a disturbing context these days. Nino Leitner's EveryStepYouTake documentary on the state of surveillance in the U.K will premier this month, and I suspect the full version will be made available for the world to see too : Nitin Kumar and Vipin Kumar are about to present the Vbootkit at the upcoming Blackhat and HITB cons :
Nitin Kumar and Vipin Kumar are about to present the Vbootkit at the upcoming Blackhat and HITB cons : Enterprise 2.0 is slowly gaining grounds and you cannot deny it despite top management's neutral position on yet another major "Reengineering of the Corporation". Supply chain management was perhaps among the first departments to really utilize the power of real-time information, and interoperable data standarts -- a mashup-ed ecosystem -- but improving your employees productivity through Web 2.0 tools such as intranet blogs and wikis remains just as unpopular as actual Fortune 500 companies blogging? But how come? Lack of evangelists? Not at all. There's one minor obstacle, you cannot teach an old dog new tricks, unless of course you dedicate extra investments into training him, which is exactly what I feel is happening at the corporate stage - everyone's patiently waiting for the concepts to mature before training and implementation happen for real. What's the current attitude towards external Web 2.0 activities? A Fortune 500 blogosphere isn't emerging as fast as the mainstream one is according to the Fortune 500 Business Blogging Wiki :
Enterprise 2.0 is slowly gaining grounds and you cannot deny it despite top management's neutral position on yet another major "Reengineering of the Corporation". Supply chain management was perhaps among the first departments to really utilize the power of real-time information, and interoperable data standarts -- a mashup-ed ecosystem -- but improving your employees productivity through Web 2.0 tools such as intranet blogs and wikis remains just as unpopular as actual Fortune 500 companies blogging? But how come? Lack of evangelists? Not at all. There's one minor obstacle, you cannot teach an old dog new tricks, unless of course you dedicate extra investments into training him, which is exactly what I feel is happening at the corporate stage - everyone's patiently waiting for the concepts to mature before training and implementation happen for real. What's the current attitude towards external Web 2.0 activities? A Fortune 500 blogosphere isn't emerging as fast as the mainstream one is according to the Fortune 500 Business Blogging Wiki :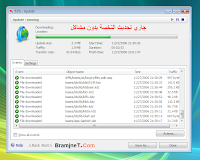 I wonder what are the low lifes actually protecting themselves from? Malware attacks in principle, or preparing to prevent a malware infection courtesy of an unamed law enforcement agency given their interest in coding malware :
I wonder what are the low lifes actually protecting themselves from? Malware attacks in principle, or preparing to prevent a malware infection courtesy of an unamed law enforcement agency given their interest in coding malware : A spammer's biggest trade off - making it through anti-spam filters doesn't mean the email receipt will even get the slightest chance of understanding what he's about to get scammed with.
A spammer's biggest trade off - making it through anti-spam filters doesn't mean the email receipt will even get the slightest chance of understanding what he's about to get scammed with. Symantec (SYMC) just released their latest Internet Security Threat Report, a 104 pages of rich on graphs observations, according to the data streaming from their sensor network :
Symantec (SYMC) just released their latest Internet Security Threat Report, a 104 pages of rich on graphs observations, according to the data streaming from their sensor network : And hey, that's from someone attending the Microsoft MVP for N-th time :
And hey, that's from someone attending the Microsoft MVP for N-th time : In a previous post I commented on O'Reilly.com's war on spam according to their statistics, and thought you might find the most recent TechCrunch blog spam stats they've recently provided, informative as well :
In a previous post I commented on O'Reilly.com's war on spam according to their statistics, and thought you might find the most recent TechCrunch blog spam stats they've recently provided, informative as well : Some stats try to emphasize on the number of people affected while forgetting the key points I outlined in a previous post related to why we cannot measure the real cost of cybercrime, and yes, duplicates among the affected people in any of the statistics available. The number of people affected will continue to rise, but that's not important, what's important is to identify the weakest link in this process, and for the time being, you're a "data hostage" in order to enjoy your modern lifestyle -- ever asked yourself what's gonna happen with your digital data after you're gone?
Some stats try to emphasize on the number of people affected while forgetting the key points I outlined in a previous post related to why we cannot measure the real cost of cybercrime, and yes, duplicates among the affected people in any of the statistics available. The number of people affected will continue to rise, but that's not important, what's important is to identify the weakest link in this process, and for the time being, you're a "data hostage" in order to enjoy your modern lifestyle -- ever asked yourself what's gonna happen with your digital data after you're gone?View figures and tables of this paper as a *.pdf. View pre-publication draft of paper as a *.pdf. View dataset of incidents as a *.xls. View University of Washington Press office news release on this research."
Graphic presenting the risk of identity theft in the U.S only, based on the severity of data breaches, courtesy of the Danny Dougherty.
 The folks at Security-Database.com -- who by the way expressed their excitement over my blog -- just released an outstanding mind mapping graph on the most common firefox security extensions used for various purposes starting from information gathering, and going up to data tampering :
The folks at Security-Database.com -- who by the way expressed their excitement over my blog -- just released an outstanding mind mapping graph on the most common firefox security extensions used for various purposes starting from information gathering, and going up to data tampering : Great idea, reminds of Ollie Whitehouse's excellent mind mapping of mobile device threats. The semantics of security when applied in a visualized manner have the potential to limit the "yet another malware variant in the wild" type of news articles, or hopefully help the mainstream media break out of the "echo chamber" and re-publishing myopia, thus covering the basics.
Great idea, reminds of Ollie Whitehouse's excellent mind mapping of mobile device threats. The semantics of security when applied in a visualized manner have the potential to limit the "yet another malware variant in the wild" type of news articles, or hopefully help the mainstream media break out of the "echo chamber" and re-publishing myopia, thus covering the basics. Continuing the coverage on the U.S government's overall paranoia of using outsourced software on DoD computers, even hardware -- firmware infections are still in a spy's arsenal only -- in a recent move by the Defense CIO office a tiger team has been officially assigned to audit the software and look for potential backdoors :
Continuing the coverage on the U.S government's overall paranoia of using outsourced software on DoD computers, even hardware -- firmware infections are still in a spy's arsenal only -- in a recent move by the Defense CIO office a tiger team has been officially assigned to audit the software and look for potential backdoors : Iran's a rising star these days. It's not just that the country recently launched it's first missile into space despite efforts of the international community to ban its nuclear program, got caught into obtaining sensitive military technology, is currently helping the enemies(Hezbollah) of its enemies(the U.S) but also, have Russia enriching their uranium in between legally supplying them with technology and upgrade parts the U.S put an embargo on -- business as usual. Here's a very in-depth and informative timeline of Iran's entire nuclear program saga :
Iran's a rising star these days. It's not just that the country recently launched it's first missile into space despite efforts of the international community to ban its nuclear program, got caught into obtaining sensitive military technology, is currently helping the enemies(Hezbollah) of its enemies(the U.S) but also, have Russia enriching their uranium in between legally supplying them with technology and upgrade parts the U.S put an embargo on -- business as usual. Here's a very in-depth and informative timeline of Iran's entire nuclear program saga : I thought I've seen the best close-ups from Google Maps in the top 10 naked people on Google Earth, but this screenshot is spooky as the guy is even looking straight into the sky which makes it even more interesting catch. It proves ones thing, Google are capable of providing high-res satellite imagery, which they aren't on a mass scale for the time being. Shall we speculate on the possible reasons why is this guy looking above, remotely controlled aerial surveillance device, but what's the relation with Google Maps whatsoever? More at Google Blogoscoped, as well as in previous posts related to the topic.
Continue reading →
I thought I've seen the best close-ups from Google Maps in the top 10 naked people on Google Earth, but this screenshot is spooky as the guy is even looking straight into the sky which makes it even more interesting catch. It proves ones thing, Google are capable of providing high-res satellite imagery, which they aren't on a mass scale for the time being. Shall we speculate on the possible reasons why is this guy looking above, remotely controlled aerial surveillance device, but what's the relation with Google Maps whatsoever? More at Google Blogoscoped, as well as in previous posts related to the topic.
Continue reading →
 Visualization in military brienfings and intelligence gathering has been a daily lifestyle of analysts for years, but combining visualization and touchscreens makes it the perfect combination to boost productivity. We're very near to entering the stage where VR will not only save lifes in a war zone, but also allow a skilled and hard to replace warrior to operate a device while enjoying his Coke back home. Great demonstration. Via Defensetech.
Visualization in military brienfings and intelligence gathering has been a daily lifestyle of analysts for years, but combining visualization and touchscreens makes it the perfect combination to boost productivity. We're very near to entering the stage where VR will not only save lifes in a war zone, but also allow a skilled and hard to replace warrior to operate a device while enjoying his Coke back home. Great demonstration. Via Defensetech. Nice slideshow courtesy of eWeek providing various screenshots related to Vladuz's impersonation attacks on Ebay :
Nice slideshow courtesy of eWeek providing various screenshots related to Vladuz's impersonation attacks on Ebay : It's not just a stereotyped beauty model, advanced image editing tools and techniques can make you believe in, but they can also influence your understand of reality too as you can see in Wired's famous altered photos collection :
It's not just a stereotyped beauty model, advanced image editing tools and techniques can make you believe in, but they can also influence your understand of reality too as you can see in Wired's famous altered photos collection : Keyloggers on demand, the so called zero day keyloggers ones created especially to be used in targeted attacks are something rather common these days. Among the many popular ones that remained in service and has been updated for over an year is The Rat! Keylogger. Here are some prices in virtual WMZ money concerning all of its versions :
Keyloggers on demand, the so called zero day keyloggers ones created especially to be used in targeted attacks are something rather common these days. Among the many popular ones that remained in service and has been updated for over an year is The Rat! Keylogger. Here are some prices in virtual WMZ money concerning all of its versions : An automated translation of its features :
An automated translation of its features :
RSS Feed