 My "fan club" is at it again - abusing Web 2.0 in an automated fashion. A new Koobface variant, modified by a Cyrillic-aware cybercriminal going under the handle of "floppy" -- it has also been injected within legitimate sites -- has started using Twitter as a distribution channel for the group as of last week.
My "fan club" is at it again - abusing Web 2.0 in an automated fashion. A new Koobface variant, modified by a Cyrillic-aware cybercriminal going under the handle of "floppy" -- it has also been injected within legitimate sites -- has started using Twitter as a distribution channel for the group as of last week.Hundreds of users infected with Koobface and using Twitter, are now automatically tweeting links to their followers in an attempt by the Koobface gang -- evidence on my fan club's involvement keeps popping up like mushrooms -- to abuse the much more insecure micro-blogging service in comparison with their original traffic acquisition Facebook, where they had to adapt and outsource the CAPTCHA-solving process.
 The Twitter campaign is different in the sense that the Koobface serving URLs generate random strings in an attempt to defeat generic detection which is still possible due to the template-ization of malware serving sites.
The Twitter campaign is different in the sense that the Koobface serving URLs generate random strings in an attempt to defeat generic detection which is still possible due to the template-ization of malware serving sites.The Koobface serving links themselves are a combination of purely malicious and compromised legitimate web sites, serving a slightly modified fake YouTube page, and using a well known -- maintained by the fan club -- command and control/redirector domains (119.110.107 .137/redirectsoft/go/tw.php; 61.235.117 .71/redirectsoft/go/tw.php) found in their previous campaigns. This particular campaign provided factual evidence on the direct connection between the group and several Twitter, LinkedIn and Scribd malware campaigns, where scareware and Koobface variants were served.
The following is a complete list of the Koobface URLs used in the Twitter campaign:
64.37.106 .170/myfilm/
66.206.9 .169/privateaction/index.php
asachi.evolink .ro/bestdvd/
aspompierul.zzl .org/freeperformans/
aspompierul.zzl .org/publicclips/
bit.ly/ w4ITQ
bodegasjalisco .com/bestfilms/
brentsmusic .com/publicaction/
cadcam.tecnoceram .it/privatedvd/
carolslinks .com/fantastictube/
caruso89.netsons .org/bestaction/
celaneotest.fun-domain .com/uncensoredvids/
chaps.com .my/besttube/
chriscubed .com/cooldemonstration/
costafarilya .com/extrimetv/
cubman32.net .ua/extrimevids/
dalaa3.110mb .com/extrimeaction/
deathschildren .com/extrimeclips/
divya.com .au/megatube/
download.rmes .ru/uncensoredclip/
dplive.webserwer .pl/besttv/
dramat.ilive .ro/extrimeclips/
 filipicsr .biz/youtube/
filipicsr .biz/youtube/flaviusrize .com/uncensoredclips/index.php
gandhiinternational. in/extrimetv/
igorbrasil .com/freetv/
itprospecialists .com/cooldvd/
kawalkimp3.yoyo .pl/yourtv/
kuzmi4.110mb .com/yourshow/index.php
lemujeme .cz/myshow/
lepk.yoyo .pl/privatevids/
matt.freehost .pl/privatefilms/
nataly.org .ua/extrimedemonstration/
oceanacompany .com/bestvids/
oceanacompany .com/yourshow/
piuk-chow .dk/megafilms/
promo-door .ru/mymovie/
reprographic .co.in/fantasticaction/
reprographic .co.in/megaperformans/
rksrouby .cz/funnyaction/
sekurpaslanmaz .com/amaizingdvd/
 sekurpaslanmaz .com/bestfilms/
sekurpaslanmaz .com/bestfilms/siam9 .com/bestfilms/
siam9 .com/coolclip/
siam9 .com/publicmovies/
skywebupload.freeweb7 .com/funnyclips/
srbijafest .org/privatefilm/
subject.freehost .pl/extrimefilms/
subject.freehost .pl/publicvids/
supreeme .com/megademonstration/
teatrall.dramat.ilive .ro/extrimeclips/
 tenminutemedia .com/funnyclip/
tenminutemedia .com/funnyclip/thegoodhand .com/yourmovie/
thelambda.php5 .cz/privatemovies/
tinyurl .com/l48o9v
webxtreme.evolink .ro/uncensoredtube/
wiedzmin06.lua .pl/myvids/
xpertfill.com .mx/megafilm/
yarentextil .com/funnyvideo/
yasarturu.com .tr/yourvideo/
zoomtox .com/youtube/
 Interestingly, I was able to take a peek at the statistics used exclusively for the Twitter campaign on two of the command and control/redirectors domains maintained by the gang. The results? Thankfully, pretty modest as you can see in the attached screenshots.
Interestingly, I was able to take a peek at the statistics used exclusively for the Twitter campaign on two of the command and control/redirectors domains maintained by the gang. The results? Thankfully, pretty modest as you can see in the attached screenshots.What all of these URLs have in common are the Koobface command and control/redirector (r-d-cgpay-090709 .com/go/tw.php) domains that they point to, including several new additions prior to their original ones described in previous posts.
 Command and control domains sharing the same IPs - 98.143.159.138; 78.110.175.15; 61.235.117.71; 119.110.107.137:
Command and control domains sharing the same IPs - 98.143.159.138; 78.110.175.15; 61.235.117.71; 119.110.107.137:upr0306 .com - Email: bigvillyxxx@gmail.com
red-dir-cgpay-0307 .com
cgpay-re-230609 .com
r-d-cgpay-090709 .com
rjulythree .com
trisem .com - Email: 2009polevandrey@mail.ru
uprtrishest .com - Email: 2009polevandrey@mail.ru
uthreejuly .com
rd040609-cgpay .net
newcounters .cn - Email: madarkipun@yandex.ru
rd040609-cgpay .net
r2606 .com
er20090515 .com
redir2404 .com
wn20090504 .com - Email: bigvillyxxx@gmail.com
redir0705 .com
redir0805 .com
er20090515 .com
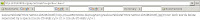 On the these very same command and control domains, we can also also seen Koobface worm's captcha7.dll component in action:
On the these very same command and control domains, we can also also seen Koobface worm's captcha7.dll component in action:rd040609-cgpay .net/cap/?a=get&i=1&v=7
upr0306 .com/cap/?a=get&i=2&v=7
rjulythree .com/cap/?a=get&i=3&v=7
uthreejuly .com/cap/?a=get&i=4&v=7
er20090515 .com/cap/?a=get&i=0&v=7
In this particular case, obtaining the CAPTCHA image from nua06032009 .biz/cap/temp - 218.93.202.50 Email: kfmnmkswrnkcxlgpfdxb68@gmail.com.
A complete list of command and control domains courtesy of FireEye, is once again emphasizing on the fact that the Koobface gang may be aware of each and every malicious traffic acquisition tactic there is, but has centralized their infrastructure making it easy to deal with it.
Who's providing them with the hosting infrastructure?
218.93.202.50 - China Beijing Chinanet Jiangsu Province Network
98.143.159.138 - United States Los Angeles Oc3 Networks & Web Solutions Llc
78.110.175.15 - Russian Federation Limit-surehost-ip/UK Dedicated Servers Limited
61.235.117.71 - China Shenzhen China Railcom Guangdong Shenzhen Subbranch
119.110.107.137 - Malaysia Kuala Lumpur Tm Net Sdn Bhd
Compared to the money they make out of scareware, since they diversify on multiple revenue-generation fronts, they money they pay for the anti-abuse hosting looks like pocket change.
Related posts:
Dissecting the Koobface Worm's December Campaign
Dissecting the Latest Koobface Facebook Campaign
The Koobface Gang Mixing Social Engineering Vectors
Ukrainian "fan club" and the Koobface connection:
Dissecting a Swine Flu Black SEO Campaign
Massive Blackhat SEO Campaign Serving Scareware
From Ukrainian Blackhat SEO Gang With Love
From Ukrainian Blackhat SEO Gang With Love - Part Two
From Ukraine with Scareware Serving Tweets, Bogus LinkedIn/Scribd Accounts, and Blackhat SEO Farms
Fake Web Hosting Provider - Front-end to Scareware Blackhat SEO Campaign at Blogspot
This post has been reproduced from Dancho Danchev's blog.

No comments:
Post a Comment